filmov
tv
What is an Integer Overflow Vulnerability? | Hacking 101

Показать описание
A quick introduction to how binary integers work, what an integer overflow is, and how they can lead to software vulnerabilities.
What is an Integer Overflow Vulnerability? | Hacking 101
overflow.c: integer overflow in C (Kevin Lynch)
Buffer Overflows and Integer Overflows - CompTIA Security+ SY0-401: 3.5
What is an integer overflow in Solidity?
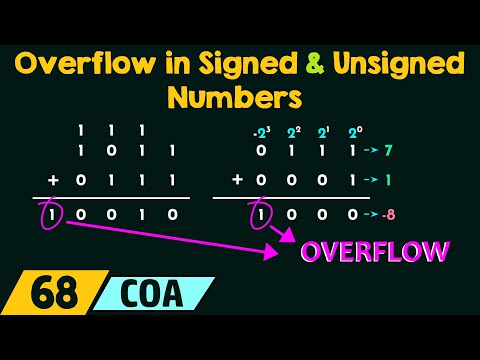
Overflow in Signed and Unsigned Numbers
What is Integer Overflow? Under 1 min.
Domain 1.19: Integer overflow - CompTIA Security+ SY0 601
Integer Overflow Vulnerability | Binary Exploitation - 0x2
What is Integer Overflow Attack? | Impossible Number 247 CTF
Integer overflow in practice
Java Integer Overflow Problem Explained by Example - Java Tutorial - Appficial
23. Integer Overflow in C - CS101 Introduction to Computing
Integer Overflow in Solidity 0.8.0?
Integer Overflow in Buckshot Roulette
Integer Overflow - CTF Cookbook - pwn
†: Signed and Unsigned Integers - Integer Overflows - Pwn Adventure 3
Binary Overflow
Check for Integer Overflow | GeeksforGeeks
The Integer Overflow Error
Integer Overflows: When 15 + 1 doesn't equal 16 [Capture The Flag Fundamentals]
Demonstrating an Integer Overflow in Bitdefender Internet Security
C++ : why there is a integer overflow in this multiplication?
Binary Addition & Overflow - Computerphile
Integer overflow and underflow explained
Комментарии
 0:04:53
0:04:53
 0:02:44
0:02:44
 0:05:06
0:05:06
 0:02:03
0:02:03
 0:10:11
0:10:11
 0:00:58
0:00:58
 0:01:00
0:01:00
 0:14:28
0:14:28
 0:03:11
0:03:11
 0:00:21
0:00:21
 0:02:08
0:02:08
 0:03:52
0:03:52
 0:07:45
0:07:45
 0:00:20
0:00:20
 0:03:20
0:03:20
 0:03:12
0:03:12
 0:03:22
0:03:22
 0:02:47
0:02:47
 0:04:47
0:04:47
 0:07:32
0:07:32
 0:00:31
0:00:31
 0:01:17
0:01:17
 0:07:00
0:07:00
 0:14:17
0:14:17