filmov
tv
How They Hack: Simple Buffer Overflow

Показать описание
I bashed this video together to show you the loose concept of a buffer overflow and how abusing inputs can enable an attacker to execute code or change the behaviour of a program in a noteworthy way. This example is very simple compared to more modern examples which are covered in my other videos.
How They Hack: Simple Buffer Overflow
How They Hack: Buffer Overflow & GDB Analysis - James Lyne
Running a Buffer Overflow Attack - Computerphile
HACKED! How a Buffer Overflow Exploit works, plus Code Red!
simple buffer overflow attack/hack
How to hack back to the basic (Remote buffer overflow)
Watch these hackers crack an ATM in seconds
A simple Format String exploit example - bin 0x11
How to exploit a buffer overflow vulnerability - Practical
coding in c until my program is unsafe
Mini militia Hack mod😈 ( how to hack mini militia) mod apk 😤mini malasiya 🔥#youtubeshorts #shorts...
😱 You gonna love this French bun hairstyle HACK #shorts
Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro Hacker
First Exploit! Buffer Overflow with Shellcode - bin 0x0E
17 Introduction to Buffer Overflows.mp4 | Hacking with kali | Hack The Planet
🤯YOU WON'T BELIEVE THIS INSANE WD-40 CLEANING HACK! #shorts
Top 5 Acrylic application mistakes‼️What mistake are you guilty of ???
The Secret step-by-step Guide to learn Hacking
4 Nail Drill Bits you need in your nail kit for the perfect fill.
how to hack highly secured website using Buffer Over Flow Injection
Easy Hack For Warts 🔥#shorts
Buffer Overflows can Redirect Program Execution - bin 0x0D
Cyberpunk 2077, Breach Protocols Explained (Hacking) - Getting the Most Out of Breach/Access Points
Nail Art Hack with Old Eyeliner Brush
Комментарии
 0:07:37
0:07:37
 0:16:06
0:16:06
 0:17:30
0:17:30
 0:25:50
0:25:50
 0:04:57
0:04:57
 0:08:07
0:08:07
 0:05:42
0:05:42
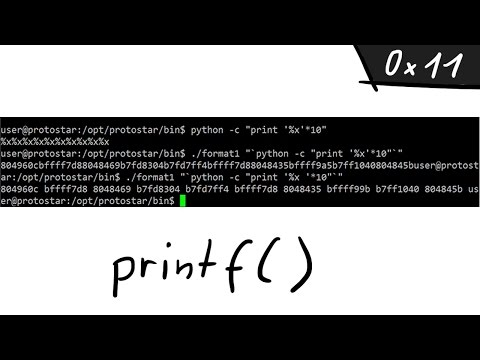 0:10:01
0:10:01
 0:09:44
0:09:44
 0:00:48
0:00:48
 0:00:16
0:00:16
 0:00:38
0:00:38
 0:10:03
0:10:03
 0:12:23
0:12:23
 0:05:00
0:05:00
 0:00:47
0:00:47
 0:00:31
0:00:31
 0:14:42
0:14:42
 0:00:27
0:00:27
 0:08:43
0:08:43
 0:00:44
0:00:44
 0:07:23
0:07:23
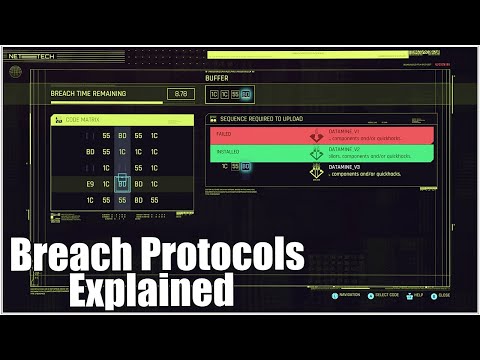 0:04:24
0:04:24
 0:00:24
0:00:24