filmov
tv
Learn How to Hack JWT Token | Multiple way to exploit JWT Token

Показать описание
100K $ bug
#JWTtoken #pentestingJWT #AppleBounty
POC Link :
JWT TOKEN (JSON WEB TOKENS)
2:00 JWT token identification
5:00 Ways to Attck JWT token
9:00 Bounty 100k$ issue analysis
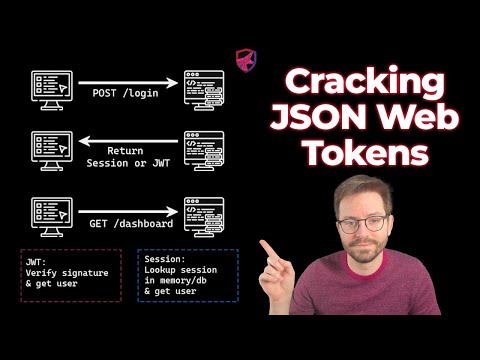
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Ways to attack
2.NONE algorithm
3.Changing the Algorithm from RS256 to HS256
4.Cracking the hs256
JWT brute tool
-----------------------
Authorization: Bearer token
KID
SQL injection, Directory Traversal
“kid”: "aaaaaaa' UNION SELECT 'key';--"
Example JWT Token:
Reference :
DISCLAIMER: This Channel Does NOT Promote or encourage Any illegal activities, all contents provided by This Channel is meant for EDUCATIONAL PURPOSE only.
Copyright Disclaimer Under Section 107 of the Copyright Act 1976, allowance is made for "fair use" for purposes such as criticism, comment, news reporting, teaching, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational, or personal use tips the balance in favor of fair use.
#JWTtoken #pentestingJWT #AppleBounty
POC Link :
JWT TOKEN (JSON WEB TOKENS)
2:00 JWT token identification
5:00 Ways to Attck JWT token
9:00 Bounty 100k$ issue analysis
JSON Web Token (JWT) is an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
Ways to attack
2.NONE algorithm
3.Changing the Algorithm from RS256 to HS256
4.Cracking the hs256
JWT brute tool
-----------------------
Authorization: Bearer token
KID
SQL injection, Directory Traversal
“kid”: "aaaaaaa' UNION SELECT 'key';--"
Example JWT Token:
Reference :
DISCLAIMER: This Channel Does NOT Promote or encourage Any illegal activities, all contents provided by This Channel is meant for EDUCATIONAL PURPOSE only.
Copyright Disclaimer Under Section 107 of the Copyright Act 1976, allowance is made for "fair use" for purposes such as criticism, comment, news reporting, teaching, scholarship, and research. Fair use is a use permitted by copyright statute that might otherwise be infringing. Non-profit, educational, or personal use tips the balance in favor of fair use.
Комментарии
 0:06:30
0:06:30
 0:12:13
0:12:13
 0:10:28
0:10:28
 0:13:15
0:13:15
 0:07:39
0:07:39
 0:07:28
0:07:28
 0:14:34
0:14:34
 0:17:23
0:17:23
 0:09:50
0:09:50
 0:31:05
0:31:05
 0:17:00
0:17:00
 0:07:25
0:07:25
 0:18:28
0:18:28
 0:35:24
0:35:24
 0:22:49
0:22:49
 0:03:46
0:03:46
 1:32:47
1:32:47
 0:04:42
0:04:42
 0:04:50
0:04:50
 0:06:37
0:06:37
 0:00:28
0:00:28
 0:03:41
0:03:41
 0:00:16
0:00:16
 0:20:23
0:20:23