filmov
tv
JSON Web Token Hacking

Показать описание
// Membership //
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
JSON Web Token Hacking
How Hackers Hack JSON Web Tokens
Cracking JSON Web Tokens
How to Exploit 'Json Web Token'(JWT) vulnerabilities | Full Practical
Hack JWT using JSON Web Tokens Attacker BurpSuite extensions
JWT | JSON Web Token | Bug Bounty | Penetration Testing
Session vs Token Authentication in 100 Seconds
JSON Web Keys (JWK & JWT) - 'Emergency' - HackTheBox Business CTF
JWT Hacking (JSON Web Token)
JSON Web Token Vulnerabilities
BUG BOUNTY TUTORIAL: ACCOUNT TAKEOVER | JWT HACKING
ATTACKING JWT FOR BEGINNERS!
JSON Web Token Security
Attacking JWT - Header Injections
Hack Jwt Authentication Bypass Via Weak Signing Key | JSON Web Token Security | #ethicalhacking #jwt
Hacking and Securing JSON Web Tokens(JWT) - None signature attack
JWT jku&x5u = ❤️ by @snyff #NahamCon2020
API9 - Hacking JSON Web Tokens | JWT | crAPI
The Hacker's Guide to JWT Security
JWT authentication bypass via 'X-HTTP-Method-Override' Header
JWT Attack | JSON web token | Ethical Hacking | Practical Video
Hacking and Securing JSON Web Tokens(JWT) - Manually creating HS256 signature
Working with JWTs in Burp Suite
The Hacker's Guide to JWT Security by Patrycja Wegrzynowicz
Комментарии
 0:06:30
0:06:30
 0:13:15
0:13:15
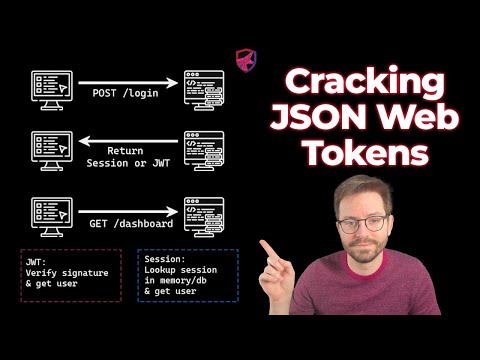 0:14:34
0:14:34
 0:07:25
0:07:25
 0:17:23
0:17:23
 0:09:50
0:09:50
 0:02:18
0:02:18
 0:29:09
0:29:09
 0:35:24
0:35:24
 0:16:28
0:16:28
 0:10:28
0:10:28
 0:07:39
0:07:39
 0:07:49
0:07:49
 0:18:28
0:18:28
 0:22:49
0:22:49
 0:04:42
0:04:42
 0:17:00
0:17:00
 0:20:23
0:20:23
 0:27:52
0:27:52
 0:03:14
0:03:14
 0:08:54
0:08:54
 0:07:09
0:07:09
 0:03:13
0:03:13
 0:48:25
0:48:25