filmov
tv
How to Exploit 'Json Web Token'(JWT) vulnerabilities | Full Practical

Показать описание
JSON Web Token (JWT, RFC 7519) is a way to encode claims in a JSON document that is then signed. JWTs can be used as OAuth 2.0 Bearer Tokens to encode all relevant parts of an access token into the access token itself instead of having to store them in a database.
:::::::::::::::::::::::::::::::::::::::::::
00:00 - intro
00:12 - What is JWT?
01:19 - None Algorithm Vulnerability
01:45 - Practical : None Algorithm Vulnerability
02:30 - RS256 to HS256 Vulnerability
03:04 - Practical : RS256 to HS256 Vulnerability
05:32 - Weak JWT Signature
07:08 - Conclusion
:::::::::::::::::::::::::::::::::::::::::::
:::::::::::::::::::::::::::::::::::::::::::
00:00 - intro
00:12 - What is JWT?
01:19 - None Algorithm Vulnerability
01:45 - Practical : None Algorithm Vulnerability
02:30 - RS256 to HS256 Vulnerability
03:04 - Practical : RS256 to HS256 Vulnerability
05:32 - Weak JWT Signature
07:08 - Conclusion
:::::::::::::::::::::::::::::::::::::::::::
How to Exploit 'Json Web Token'(JWT) vulnerabilities | Full Practical
How Hackers Hack JSON Web Tokens
JSON Web Token Hacking
Cracking JSON Web Tokens
Hands-On Realistic Pentesting - How to Exploit JWT Vulnerabilities
Bug Bounty Explained! How Hackers Break Into Your Website Using Only JSON?! Protect Your Website!
JSON Web Token Security
Taking over a website with JWT Tokens!
OWASP London Chapter Meetup 15-Jan-2025 Live-Stream
JSON Web Token Vulnerabilities
JWT | JSON Web Token | Bug Bounty | Penetration Testing
🚨Admin Panel Bypass | Privilege Escalation with JWT (JSON Web Token) | Bug Bounty - PoC 🚨
ATTACKING JWT FOR BEGINNERS!
Hacking and Securing JSON Web Tokens(JWT) - Manually creating HS256 signature
JSON Web Keys (JWK & JWT) - 'Emergency' - HackTheBox Business CTF
Hack JWT using JSON Web Tokens Attacker BurpSuite extensions
Attacking JWT - Header Injections
Introduction to JWT tokens - What are they and how can we hack them
BUG BOUNTY TUTORIAL: ACCOUNT TAKEOVER | JWT HACKING
What is JWT token | How to exploit | explain hackerone reports | Bug bounty technique
Hacking and Securing JSON Web Tokens(JWT) - None signature attack
JSON Web Token Exploitation
JWT Hacking (JSON Web Token)
JSON Web Token (JWT) Exploit with SQL Injection | CTF Walkthrough
Комментарии
 0:07:25
0:07:25
 0:13:15
0:13:15
 0:06:30
0:06:30
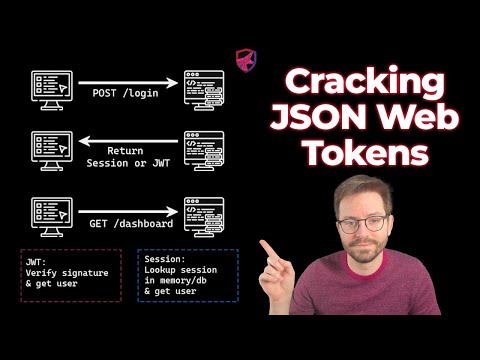 0:14:34
0:14:34
 0:07:28
0:07:28
 0:12:20
0:12:20
 0:07:49
0:07:49
 0:14:27
0:14:27
 2:18:20
2:18:20
 0:16:28
0:16:28
 0:09:50
0:09:50
 0:04:13
0:04:13
 0:07:39
0:07:39
 0:07:09
0:07:09
 0:29:09
0:29:09
 0:17:23
0:17:23
 0:18:28
0:18:28
 0:03:46
0:03:46
 0:10:28
0:10:28
 0:06:34
0:06:34
 0:04:42
0:04:42
 0:17:17
0:17:17
 0:35:24
0:35:24
 0:30:16
0:30:16