filmov
tv
Multiplicative inverse in Information security

Показать описание
1.Security goals
4.Basic terms in information security
5.Caesar cipher
6.Affine cipher
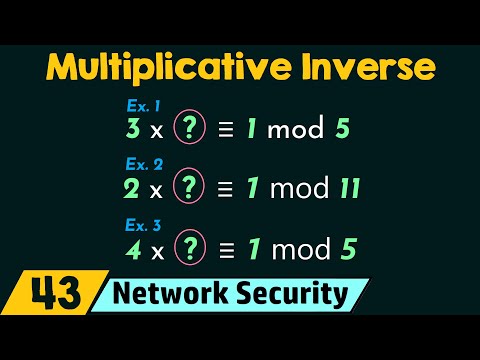
8.Multiplicative inverse
11.Autokey cipher
12.Hill cipher
13. Vernam cipher
14. Vigenere cipher
15.Raifence cipher
16. Railfence cipher when depth not given
17.Columnar cipher
18.Gcd of alphabets
19.Euclidean algorithm
20.Extended Euclidean algorithm
21.Euler's Totient function
22.Fermat's Theorem
23.Euler's Theorem
24 .Chinese Remainder Theorem
25)Diffie Hellman Key Exchange Cryptosystem
26) Simplified DES(Data Encryption standard)
27)RSA algorithm
28) Elgamal Digital Signature Scheme
4.Basic terms in information security
5.Caesar cipher
6.Affine cipher
8.Multiplicative inverse
11.Autokey cipher
12.Hill cipher
13. Vernam cipher
14. Vigenere cipher
15.Raifence cipher
16. Railfence cipher when depth not given
17.Columnar cipher
18.Gcd of alphabets
19.Euclidean algorithm
20.Extended Euclidean algorithm
21.Euler's Totient function
22.Fermat's Theorem
23.Euler's Theorem
24 .Chinese Remainder Theorem
25)Diffie Hellman Key Exchange Cryptosystem
26) Simplified DES(Data Encryption standard)
27)RSA algorithm
28) Elgamal Digital Signature Scheme
 0:10:03
0:10:03
 0:05:49
0:05:49
 0:06:38
0:06:38
 0:10:58
0:10:58
 0:07:14
0:07:14
 0:07:46
0:07:46
 0:06:10
0:06:10
 0:11:05
0:11:05
 0:17:22
0:17:22
 0:10:16
0:10:16
 0:07:36
0:07:36
 0:06:20
0:06:20
 0:10:40
0:10:40
 0:08:45
0:08:45
 0:07:17
0:07:17
 0:08:23
0:08:23
 0:13:37
0:13:37
 0:05:08
0:05:08
 0:02:37
0:02:37
 0:16:50
0:16:50
 0:01:16
0:01:16
 0:13:01
0:13:01
 0:05:43
0:05:43
 0:00:54
0:00:54