filmov
tv
SYN Flood Denial of Service (DOS) Penetration Testing using Kali Linux | Metasploit Framework

Показать описание
In a SYN flood attack, the attacker sends repeated SYN packets to every port on the targeted server, often using a fake IP address. The server, unaware of the attack, receives multiple, apparently legitimate requests to establish communication. It responds to each attempt with a SYN-ACK packet from each open port.
The malicious client either does not send the expected ACK, or—if the IP address is spoofed—never receives the SYN-ACK in the first place. Either way, the server under attack will wait for acknowledgement of its SYN-ACK packet for some time.
The malicious client either does not send the expected ACK, or—if the IP address is spoofed—never receives the SYN-ACK in the first place. Either way, the server under attack will wait for acknowledgement of its SYN-ACK packet for some time.
SYN Flood Attack Explained
SYN Flood Denial of Service (DOS) Penetration Testing using Kali Linux | Metasploit Framework
SYN-Flood DDOS Attack Explained & Simulated
hping3 Tutorial - TCP SYN Flood Attacks - DoS and DDoS Attacks using Kali Linux 2022 and Windows XP
Denial of Service Attacks (Part 3): TCP SYN Flooding
What is a TCP SYN Flood?
Network Attack Types - DDOS and SYN Floods
02 05 SYN Flood Attacks
Denial of Service Attacks Explained
SYN Flood Denial of Service (DOS) using Kali Linux
Hping3 Demo- Kali Linux - Ping Flood and SYN Flood Attack - DOS and DDOS - Explained - CSE4003
Denial of Service SYN flood Demonstration
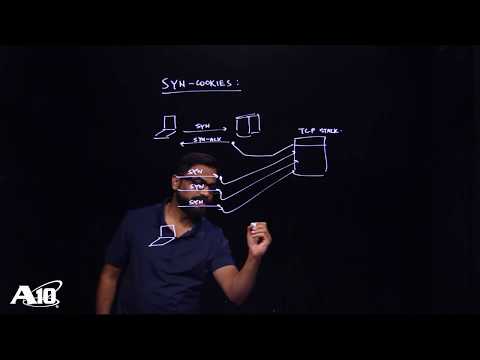
What are Syn Cookies and how are they used?
Denial of Service (Part 4): Protecting Against SYN Flooding via SYN Cookies
hping3 Tutorial - TCP SYN Flood Attacks - DoS and DDoS Attacks using Kali Linux 2022 #freeeducation
UDP Flood Denial of Service - DOS Penetration Testing using Kali Linux | Wireshark
What is a UDP Flood?
SYN Flooding Attack Using Metasploit
Performing a TCP SYN Flood Attack
Explain TCP SYN Flooding Attack or Denial of Service Attacks | DOS attack
#2- Cyber Security Principles - Dos SYN Flood Attack
DOS SYN FLOOD ATTACK USING hping3
TCP SYN FLOODING DoS ATTACK
Breaking my web server with DDOS - HTTP flood & SYN flood
Комментарии
 0:07:28
0:07:28
 0:04:43
0:04:43
 0:04:29
0:04:29
 0:16:46
0:16:46
 0:08:51
0:08:51
 0:01:52
0:01:52
 0:01:40
0:01:40
 0:03:13
0:03:13
 0:09:52
0:09:52
 0:06:39
0:06:39
 0:48:51
0:48:51
 0:03:16
0:03:16
 0:05:53
0:05:53
 0:11:30
0:11:30
 0:00:21
0:00:21
 0:07:10
0:07:10
 0:01:40
0:01:40
 0:03:55
0:03:55
 0:00:54
0:00:54
 0:03:33
0:03:33
 0:07:00
0:07:00
 0:03:48
0:03:48
 0:03:30
0:03:30
 0:24:27
0:24:27