filmov
tv
UDP Flood Denial of Service - DOS Penetration Testing using Kali Linux | Wireshark

Показать описание
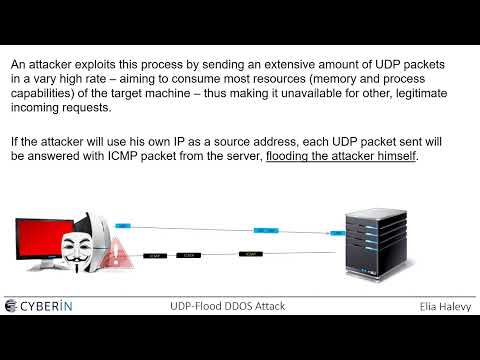
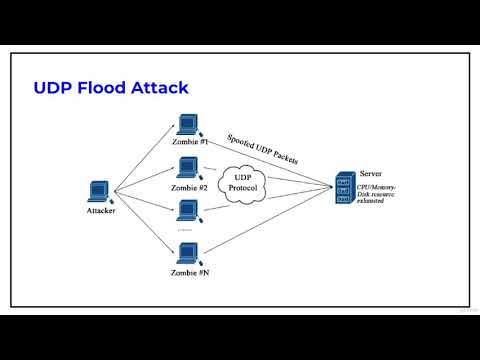
A UDP flood is a type of denial-of-service attack in which a large number of User Datagram Protocol (UDP) packets are sent to a targeted server with the aim of overwhelming that device’s ability to process and respond. The firewall protecting the targeted server can also become exhausted as a result of UDP flooding, resulting in a denial-of-service to legitimate traffic.
A UDP flood works primarily by exploiting the steps that a server takes when it responds to a UDP packet sent to one of it’s ports. Under normal conditions, when a server receives a UDP packet at a particular port, it goes through two steps in response:
The server first checks to see if any programs are running which are presently listening for requests at the specified port.
If no programs are receiving packets at that port, the server responds with a ICMP (ping) packet to inform the sender that the destination was unreachable.
A UDP flood works primarily by exploiting the steps that a server takes when it responds to a UDP packet sent to one of it’s ports. Under normal conditions, when a server receives a UDP packet at a particular port, it goes through two steps in response:
The server first checks to see if any programs are running which are presently listening for requests at the specified port.
If no programs are receiving packets at that port, the server responds with a ICMP (ping) packet to inform the sender that the destination was unreachable.
What is a UDP Flood?
UDP Flood Denial of Service - DOS Penetration Testing using Kali Linux | Wireshark
How to Investigate a UDP Flood / Denial-of-Service (DoS) Attack in NetIQ Sentinel
UDP Flood attack and Prevention- Mikrotik
DDOS UDP Flood Attack - explained and simulated
What is a UDP FLOOD DDoS Attack?
New DoS Tool (UDP FLOOD)
UDP Flood Attack
hping3 Tutorial - TCP SYN Flood Attacks - DoS and DDoS Attacks using Kali Linux 2022 and Windows XP
Lecture 35-ICMP Flooding Attack
Network Security - UDP (DNS) Flooding (Part 1)
DoS/DDoS Protection - How To Enable ICMP, UDP & TCP Flood Filtering
Real-Time DDoS Attack Showcase
Denial of Service Attacks Explained
Dos attack | Denial-of-Service Attack, SYN flood, Smurf attack, UDP (User Datagram Protocol)
SYN Flood Denial of Service (DOS) Penetration Testing using Kali Linux | Metasploit Framework
Web Server Attacks and Mitigation Using Snort - UDP flood
Hping3 Demo- Kali Linux - Ping Flood and SYN Flood Attack - DOS and DDOS - Explained - CSE4003
UDP DDoS attack Demonstration
DDoS Attack Explained
Network Security - UDP (DNS) Flooding (Part 2)
UDP Flood Lab in EVE ng | Networkforyou | CCNA
How works the UDP Flood with download link
UDP DDOS ATTACK UDP FLOOD ATTACK UDP HEADER USER DATAGRAM PROTOCOL UDP WORKS
Комментарии
 0:01:40
0:01:40
 0:07:10
0:07:10
 0:05:32
0:05:32
 0:04:24
0:04:24
 0:04:29
0:04:29
 0:00:27
0:00:27
 0:00:33
0:00:33
 0:04:00
0:04:00
 0:16:46
0:16:46
 0:10:58
0:10:58
 0:16:46
0:16:46
 0:03:47
0:03:47
 0:03:31
0:03:31
 0:09:52
0:09:52
 0:08:00
0:08:00
 0:04:43
0:04:43
 0:01:09
0:01:09
 0:48:51
0:48:51
 0:02:26
0:02:26
 0:05:43
0:05:43
 0:15:48
0:15:48
 0:06:26
0:06:26
 0:03:37
0:03:37
 0:09:10
0:09:10