filmov
tv
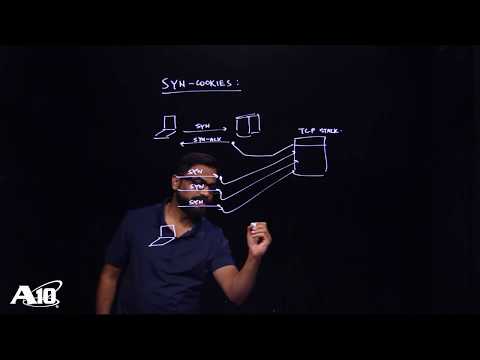
What are Syn Cookies and how are they used?

Показать описание
In this video, we look at what SYN cookies are and how they can be used for TCP authentication to protect against SYN flood attacks.
#TCPauthentication #DDoSattacks #DDoSprotection
#TCPauthentication #DDoSattacks #DDoSprotection
What are Syn Cookies and how are they used?
Denial of Service (Part 4): Protecting Against SYN Flooding via SYN Cookies
Netzwerktechnik Tutorial #51 - SYN Flooding Angriffe und SYN Cookies
SYN Cookie on ASA Stop DDoS SYN flood attack
02 05 SYN Flood Attacks
DevOps & SysAdmins: How to avoid syn cookies?
Netdev 0x14 - Issuing SYN cookies in XDP
How to enable SYN cookies on windows server 2008? (2 Solutions!!)
TCP SYN cookies are always turned on when enabled?
How to defend against DOS caused by SYN cookies?
DevOps & SysAdmins: TCP syn cookie calculation on Windows Server
What is a SYN Flood Attack? | Cybersecurity & DoS Explained in 60 Seconds!
Unix & Linux: How to enable SYN Cookies on Debian 7.5?
DevOps & SysAdmins: SYN cookies on internal machines (2 Solutions!!)
SYN Flood Attack
eBPF XDP syncookie protect F5 BIG-IP VE from SYN flood attack
What Is SYN Flood Attack? - SecurityFirstCorp.com
SYN Cookies on a LAN server - Ok / advisable to disable? (2 Solutions!!)
Unix & Linux: How to permamently disable SYN-Cookies? (3 Solutions!!)
57 - TCP Reset Cookies – a heuristic method for TCP SYN Flood mitigation (Patrik Goldschmidt)
eBPF XDP syncookie protect F5 BIG-IP VE from SYN flood attack continues
SYN-Flood DDOS Attack Explained & Simulated
#2- Cyber Security Principles - Dos SYN Flood Attack
Lär dig hur man gör de godaste småkakor någon syn. Cookie HIDAMARI COOKINg.
Комментарии
 0:05:53
0:05:53
 0:11:30
0:11:30
 0:08:42
0:08:42
 0:06:04
0:06:04
 0:03:13
0:03:13
 0:01:20
0:01:20
 0:29:34
0:29:34
 0:01:33
0:01:33
 0:02:19
0:02:19
 0:01:25
0:01:25
 0:01:32
0:01:32
 0:00:13
0:00:13
 0:01:22
0:01:22
 0:01:46
0:01:46
 0:02:31
0:02:31
 0:09:35
0:09:35
 0:01:59
0:01:59
 0:01:43
0:01:43
 0:02:29
0:02:29
 0:01:38
0:01:38
 0:03:10
0:03:10
 0:04:29
0:04:29
 0:07:00
0:07:00
 0:04:29
0:04:29