filmov
tv
Break the Double Columnar Transposition Challenge (Doppelwürfel)

Показать описание
#cryptology, #cryptography, #cryptanalysis
In this video, we break the famous double columnar transposition (in German "Doppelwürfel") challenge.
The double columnar cipher was one of the most secure hand ciphers used in the Second World War and in the Cold War. It is the columnar transposition performed twice.
The actual challenge was suggested by Otto Leiberich, former head of the BSI, in 1999 and then created by crypto author Klaus Schmeh in 2007.
There was no known solution for many years. Then, it was solved finally in 2013 by George Lasry.
We published a paper about the solution, together with Lasry, which you find here [1].
Also interesting: the blog [2] of Klaus Schmeh, who is the creator of the challenge. On his blog, you will find many interesting articles about cryptological topics.
You may download the latest version of CrypTool 2 from our website [3].
[1] Lasry, George, Nils Kopal, and Arno Wacker. "Solving the double transposition challenge with a divide-and-conquer approach." Cryptologia 38.3 (2014): 197-214.
In this video, we break the famous double columnar transposition (in German "Doppelwürfel") challenge.
The double columnar cipher was one of the most secure hand ciphers used in the Second World War and in the Cold War. It is the columnar transposition performed twice.
The actual challenge was suggested by Otto Leiberich, former head of the BSI, in 1999 and then created by crypto author Klaus Schmeh in 2007.
There was no known solution for many years. Then, it was solved finally in 2013 by George Lasry.
We published a paper about the solution, together with Lasry, which you find here [1].
Also interesting: the blog [2] of Klaus Schmeh, who is the creator of the challenge. On his blog, you will find many interesting articles about cryptological topics.
You may download the latest version of CrypTool 2 from our website [3].
[1] Lasry, George, Nils Kopal, and Arno Wacker. "Solving the double transposition challenge with a divide-and-conquer approach." Cryptologia 38.3 (2014): 197-214.
Break the Double Columnar Transposition Challenge (Doppelwürfel)
Row Column Transposition Ciphering Technique
How to solve a columnar transposition cipher
The Columnar Transposition Cipher Explained and Broken
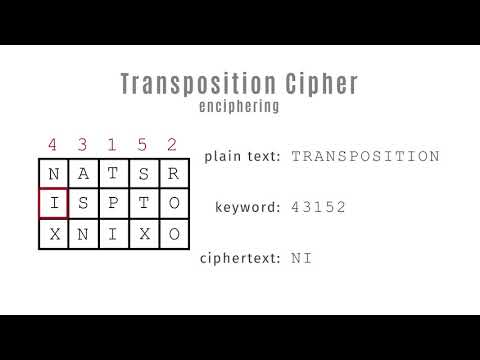
Transposition Cipher
Columnar Cipher Encryption and Decryption
Decrypt with Double Transposition
columnar transposition cipher without a key| COLUMNAR CIPHER ENCRYPTION AND DECRYPTION with example
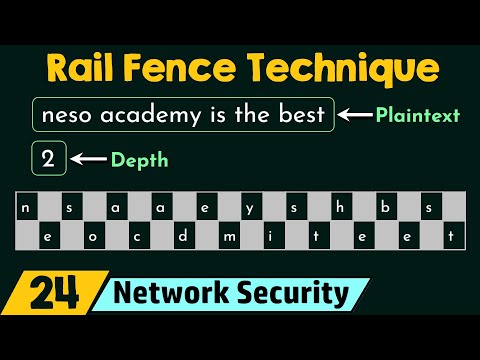
Rail Fence Technique
Module1
Columnar Transposition Technique Encryption Explained with Solved Example in Hindi
Breaking the Transposition Cipher: How to Crack a Transposition Cipher
columnar and double columnar (Cipher & Decipher) [HH]
Ep. 003 - Complete Columnar encryption and decryption
Vigenere CIpher
Double Transposition
Codemaking and Codebreaking - Transposition Ciphers
Ep. 004 - Incomplete Columnar encryption and decryption
NIS - 3.2-2 Transposition Technique (Rail Fence Technique, Simple Columnar Transposition)
Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques
Transposition cipher (columnar and double columnar)
Module 2:Transposition cipher 1.columnar Transposition cipher
Double Transposition Card Mat Tutorials
CrypTool Transposition Demo
Комментарии
 0:17:26
0:17:26
 0:08:15
0:08:15
 0:05:01
0:05:01
 0:26:25
0:26:25
 0:01:14
0:01:14
 0:12:03
0:12:03
 0:10:16
0:10:16
 0:08:54
0:08:54
 0:06:46
0:06:46
 0:13:01
0:13:01
 0:07:40
0:07:40
 0:15:46
0:15:46
 0:23:12
0:23:12
 0:10:44
0:10:44
 0:02:02
0:02:02
 0:08:47
0:08:47
 0:08:07
0:08:07
 0:11:28
0:11:28
 0:30:20
0:30:20
 0:16:34
0:16:34
 0:12:35
0:12:35
 0:08:30
0:08:30
 0:16:23
0:16:23
 0:00:57
0:00:57