filmov
tv
Row Column Transposition Ciphering Technique

Показать описание
Network Security: Row Column Transposition Ciphering Technique
Topics discussed:
1) Introduction to transposition classical ciphering technique.
2) Difference between substitution cipher and transposition cipher.
3) Operation of Row Column transposition ciphering technique with an example.
4) Generation of ciphertext using Row Column transposition technique with an example.
5) Generation of ciphertext using more complex Row Column transposition technique with an example.
Music:
Axol x Alex Skrindo - You [NCS Release]
#NetworkSecurityByNeso #Cryptography #NetworkSecurity #RowColumnTransposition
Topics discussed:
1) Introduction to transposition classical ciphering technique.
2) Difference between substitution cipher and transposition cipher.
3) Operation of Row Column transposition ciphering technique with an example.
4) Generation of ciphertext using Row Column transposition technique with an example.
5) Generation of ciphertext using more complex Row Column transposition technique with an example.
Music:
Axol x Alex Skrindo - You [NCS Release]
#NetworkSecurityByNeso #Cryptography #NetworkSecurity #RowColumnTransposition
Row Column Transposition Ciphering Technique
Transposition Cipher
Columnar Cipher Encryption and Decryption
Rectangular Transposition Encryption and Decryption
Cryptography: Transposition Cipher
Rail Fence and Row Transposition cipher techniques | Types Of Transposition Techniques
Rail Fence Technique
Columnar Transposition Technique Encryption Explained with Solved Example in Hindi
The Columnar Transposition Cipher Explained and Broken
TRANSPOSITION TECHNIQUES IN NETWORK SECURITY || RAIL FENCE CIPHER || ROW TRANSPOSITION CIPHER
Columnar transposition Cipher
The Row & Column Transposition cipher | Journey into cryptography
Columnar Transposition Cipher Technique | Encrypt Plain Text Message | Cipher & Decipher
Columnar transposition cipher(Information Security)
Columnar Transposition Cipher 🔥🔥
Columnar Transposition Cipher (Network Security) | Columnar Transposition Cipher in Network Security
#12 Columnar Transposition
columnar transposition cipher without a key| COLUMNAR CIPHER ENCRYPTION AND DECRYPTION with example
Columnar Transposition Cipher
1.8 Transposition in Tamil
Row Transposition Cipher
Transposition ciphers - Rail fence cipher, columnar transposition cipher, examples of ciphers
Cryptography - Transposition Cipher
Rail Fence cipher example : Rail fence cipher encryption and decryption technique in Cryptography
Комментарии
 0:08:15
0:08:15
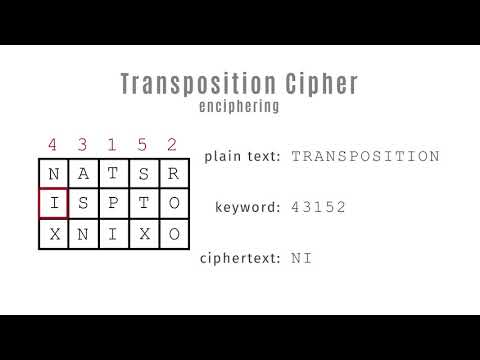 0:01:14
0:01:14
 0:12:03
0:12:03
 0:07:52
0:07:52
 0:10:23
0:10:23
 0:16:34
0:16:34
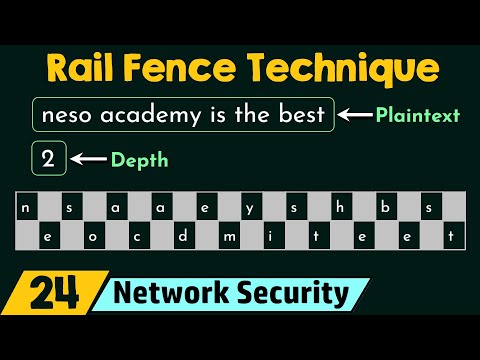 0:06:46
0:06:46
 0:07:40
0:07:40
 0:26:25
0:26:25
 0:12:47
0:12:47
 0:03:57
0:03:57
 0:02:52
0:02:52
 0:05:57
0:05:57
 0:05:08
0:05:08
 0:05:23
0:05:23
 0:05:24
0:05:24
 0:07:19
0:07:19
 0:08:54
0:08:54
 0:11:20
0:11:20
 0:06:37
0:06:37
 0:08:26
0:08:26
 0:16:06
0:16:06
 0:03:17
0:03:17
 0:04:56
0:04:56