filmov
tv
JSON Web Token Security
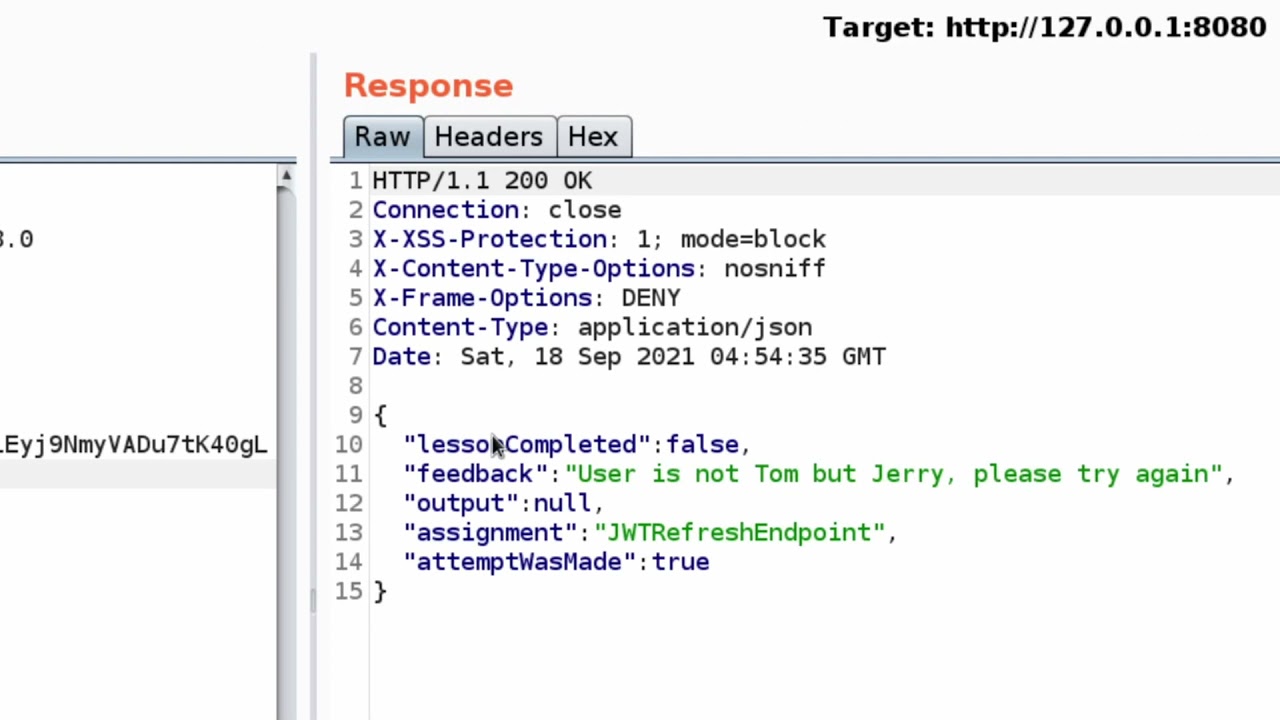
Показать описание
// Membership //
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
// Courses //
// Books //
// Social Links //
// Disclaimer //
Hacking without permission is illegal. This channel is strictly educational for learning about cyber-security in the areas of ethical hacking and penetration testing so that we can protect ourselves against the real hackers.
JSON Web Token Hacking
Why is JWT popular?
Session vs Token Authentication in 100 Seconds
What Is JWT and Why Should You Use JWT
What is JWT ? JSON Web Token Explained
Securing REST APIs - JWT Token Explained in 4 Minutes For Beginners Tutorial - S27E01
JSON Web Token Security
JWT best practices for max security
Mastering JWT Token Integration in Spring Security 6 and Spring Boot 3
What is JWT? JSON Web Tokens Explained (Java Brains)
JWT Authentication Explained
Cracking JSON Web Tokens
How does JWT work
JSON Web Tokens (JWTs) explained with examples | System Design
How to Use JWT Authorization
How Hackers Hack JSON Web Tokens
Day 27: JSON Web Tokens (JWT) | #CybersecurityAwarenessMonth 2023
JWT | JSON Web Token | Bug Bounty | Penetration Testing
Learn JWT in 10 Minutes with Express, Node, and Cookie Parser
JWT Authentication Tutorial - Node.js
Difference between cookies, session and tokens
Stop using JSON Web Tokens. Use Cookies & Server Sessions instead
What's the Structure of a JSON Web Token?
How to use a JWT Token to get data from an API with Javascript
Комментарии
 0:06:30
0:06:30
 0:05:14
0:05:14
 0:02:18
0:02:18
 0:14:53
0:14:53
 0:05:13
0:05:13
 0:04:24
0:04:24
 0:07:49
0:07:49
 0:04:50
0:04:50
 0:58:44
0:58:44
 0:14:53
0:14:53
 0:07:52
0:07:52
 0:14:34
0:14:34
 0:01:07
0:01:07
 0:11:24
0:11:24
 0:04:30
0:04:30
 0:13:15
0:13:15
 0:00:57
0:00:57
 0:09:50
0:09:50
 0:10:20
0:10:20
 0:27:36
0:27:36
 0:11:53
0:11:53
 0:23:33
0:23:33
 0:01:00
0:01:00
 0:01:00
0:01:00