filmov
tv
Can you DISABLE Windows Defender Antivirus?

Показать описание
Help the channel grow with a Like, Comment, & Subscribe!
Check out the affiliates below for more free or discounted learning!
📧Contact me! (I may be very slow to respond or completely unable to)
Check out the affiliates below for more free or discounted learning!
📧Contact me! (I may be very slow to respond or completely unable to)
Turn Off or Disable Windows Defender in Windows 11/10 (2023)
Best Way To Turn Off or Disable Windows Defender in Windows 10 (2021)
Can you DISABLE Windows Defender Antivirus?
How to Disable Microsoft Defender Antivirus in Windows 11
Don't Like Windows Defender? Remove It
How to Turn Off or Disable Windows Defender in Windows 11 (2023)
How to completely disable Windows Defender in Windows 10 (2020)
How to permanently disable windows defender from windows 10
⚡️Forza Horizon 5 Mod Menu FREE | 2024 Forza Horizon 5 Cheat | Forza 5 Hack Menu
How to Completely Turn Off Windows Defender in Windows 10
How To Disable Windows Defender In Windows 10 (Now Called Defender Antivirus)
Best Way To Turn Off or Disable Windows Defender in Windows 11/10
How to completely Turn Off Windows Defender in windows 10/11/7.
How to Disable Windows Defender
How to Turn Off Antivirus on Windows 11 or 10 PC (Windows Defender)
Best Way To Turn Off or Disable Windows Defender in Windows 11/10 (2022)
How to Disable or Enable Windows Defender on Windows 10
How to Disable Windows Defender in Windows 11 for GOOD
How to disable Windows defender correctly
PERMANENTLY TURN OFF Windows Defender on Windows 11
How to Disable Windows Defender Antivirus in Windows 10, 11?
How to Disable or Enable Windows Defender in Windows 10
how to turn off or disable windows defender in windows 10, windows 11
Goodbye Microsoft Defender
Комментарии
 0:03:09
0:03:09
 0:03:24
0:03:24
 0:28:36
0:28:36
 0:13:42
0:13:42
 0:15:17
0:15:17
 0:00:47
0:00:47
 0:01:33
0:01:33
 0:05:37
0:05:37
 0:02:07
0:02:07
 0:08:52
0:08:52
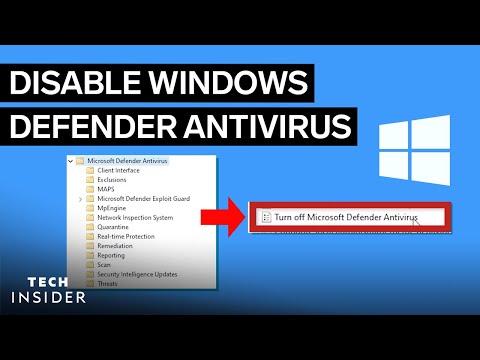 0:02:02
0:02:02
 0:05:24
0:05:24
 0:00:16
0:00:16
 0:04:06
0:04:06
 0:01:29
0:01:29
 0:05:24
0:05:24
 0:09:04
0:09:04
 0:02:44
0:02:44
 0:04:39
0:04:39
 0:10:56
0:10:56
 0:07:02
0:07:02
 0:05:27
0:05:27
 0:00:55
0:00:55
 0:10:16
0:10:16