filmov
tv
Elliptic Curve Cryptography: Key Exchange (ECDH), Digital Sig (ECDSA/EdDSA) and Encryption (ECIES)

Показать описание
Elliptic Curve Cryptography (ECC) was co-invented by Neal Koblitz and Victor Miller and scaled our discrete log method (g^x) into a multiplicative space (x.G). So the DH (Diffie-Hellman) key exchange method became ECDH and DSA (Digital Signature Algorithm) become ECDSA, and with a tweak, we can also encrypt with ECIES.
Some links on background theory and practice are:
Some links on background theory and practice are:
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Elliptic Curves - Computerphile
Elliptic Curve Cryptography Overview
Secret Key Exchange (Diffie-Hellman) - Computerphile
Math Behind Bitcoin and Elliptic Curve Cryptography (Explained Simply)
Elliptic Curve Cryptography | ECC in Cryptography and Network Security
Elliptic Curve Cryptography
Curves which make Bitcoin possible.
Elliptic Curve Cryptography & Diffie-Hellman
Elliptic Curve Cryptography: Key Exchange (ECDH), Digital Sig (ECDSA/EdDSA) and Encryption (ECIES)
Key Exchange Problems - Computerphile
Elliptic Curve Back Door - Computerphile
18 Diffie Hellman vs Elliptic Curve Cryptography
Elliptic Curves: Diffie-Hellman key exchange
13 Elliptic Curve Cryptography Overview
Lecture 17: Elliptic Curve Cryptography (ECC) by Christof Paar
What is Elliptic Curve Cryptography (ECC)? Let’s try to understand the building blocks of #crypto
Elliptic Curve Cryptography & ECDH with Example
How did the NSA hack our emails?
Elliptic Curve Cryptography
19 ECDHE - Elliptic Curve Diffie Hellman Exchange
Blockchain tutorial 11: Elliptic Curve key pair generation
Using Elliptic-Curve Cryptography (ECC) To Protect Websites - Part 1
The Math Behind Bitcoin - Elliptic Curves
Комментарии
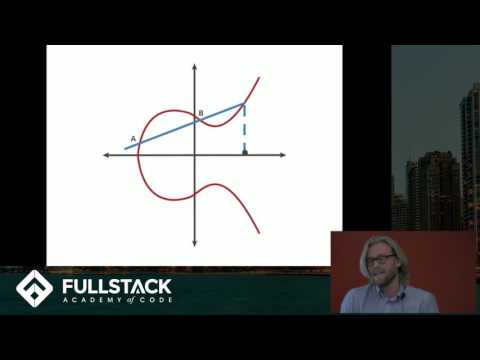 0:11:34
0:11:34
 0:08:42
0:08:42
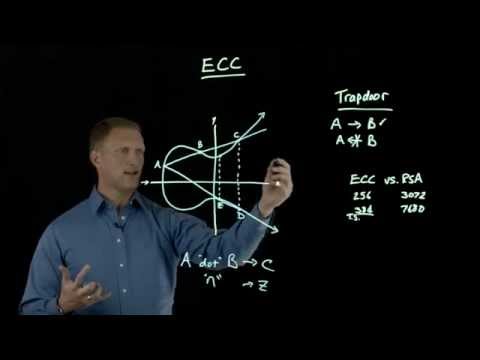 0:11:29
0:11:29
 0:08:40
0:08:40
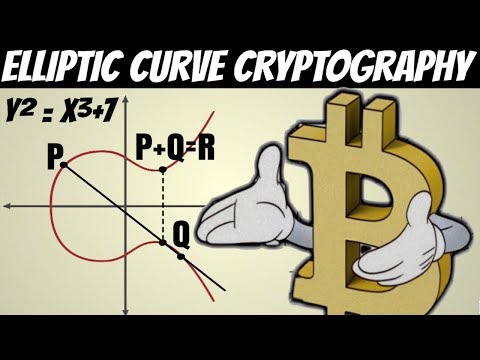 0:11:13
0:11:13
 0:14:32
0:14:32
 0:15:18
0:15:18
 0:07:45
0:07:45
 0:12:10
0:12:10
 0:47:40
0:47:40
 0:09:18
0:09:18
 0:12:24
0:12:24
 0:02:51
0:02:51
 0:03:16
0:03:16
 0:01:54
0:01:54
 1:26:31
1:26:31
 0:00:58
0:00:58
 0:27:42
0:27:42
 0:10:59
0:10:59
 0:17:10
0:17:10
 0:05:48
0:05:48
 0:18:58
0:18:58
 0:07:22
0:07:22
 0:02:35
0:02:35