filmov
tv
Elliptic Curve Cryptography & Diffie-Hellman
Показать описание
Today we're going over Elliptic Curve Cryptography, particularly as it pertains to the Diffie-Hellman protocol. The ECC Digital Signing Algorithm was also discussed in a separate video concerning Bitcoin's cryptography.
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
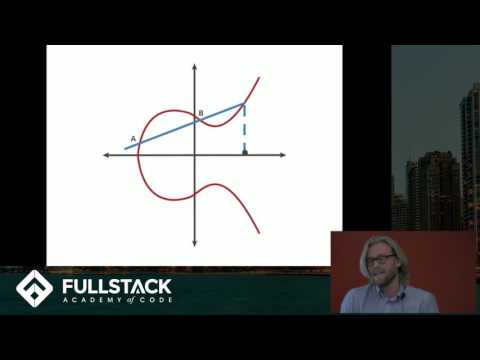
Elliptic Curves - Computerphile
Elliptic Curves #6: Diffie-Hellman Key Exchange
Elliptic Curves: Diffie-Hellman key exchange
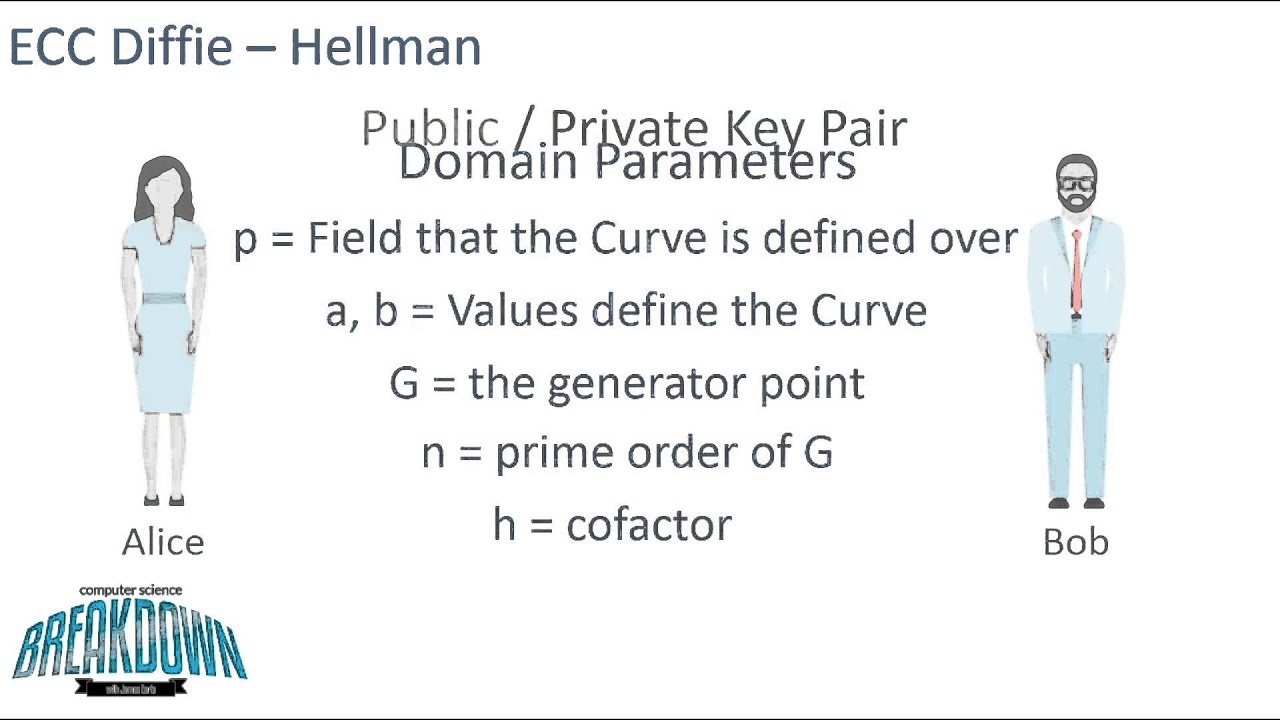
Elliptic Curve Cryptography & Diffie-Hellman
Secret Key Exchange (Diffie-Hellman) - Computerphile
18 Diffie Hellman vs Elliptic Curve Cryptography
19 ECDHE - Elliptic Curve Diffie Hellman Exchange
Elliptic Curve Back Door - Computerphile
Key Exchange Problems - Computerphile
ECDH (Elliptic Curve Diffie Hellman) with X25519
Elliptic Curves and Diffie Hellman
Diffie Hellman -the Mathematics bit- Computerphile
Elliptic Curve Cryptography | ECC in Cryptography and Network Security
Cryptoshorts e01: elliptic curve & Diffie-Hellman protocol
Elliptic Curve Diffie-Hellman
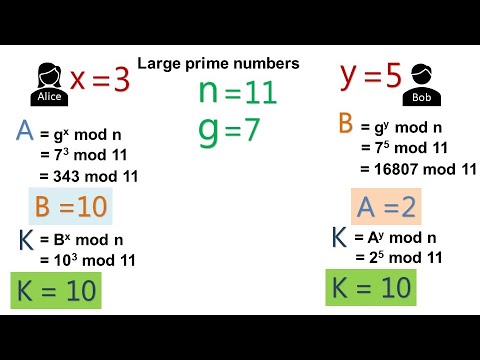
7 - Cryptography Basics - Diffie-Hellman Key Exchange
Elliptic Curve Diffie-Hellman (ECDH) Key Exchange Explained
Diffie-Hellman vs. RSA Encryption Algorithms: What's the Difference?
Diffie-Hellman Key Exchange Explained | A deep dive
Elliptic Curve Diffie Hellman (ECDH) with secp256k1
Elliptic Curve Diffie-Hellman - part 1 (VID 20181115 174313)
Diffie-Hellman, Perfect Forward Secrecy, Elliptic Curve Diffie-Hellman
Diffie Hellman Key Exchange using Bitcoin's Elliptic Curve Algorithm / The Math Behind Bitcoin
Комментарии
 0:11:34
0:11:34
 0:08:42
0:08:42
 0:13:06
0:13:06
 0:03:16
0:03:16
 0:12:10
0:12:10
 0:08:40
0:08:40
 0:02:51
0:02:51
 0:05:48
0:05:48
 0:12:24
0:12:24
 0:09:18
0:09:18
 0:19:43
0:19:43
 0:27:43
0:27:43
 0:07:05
0:07:05
 0:14:32
0:14:32
 0:04:57
0:04:57
 0:03:34
0:03:34
 0:08:48
0:08:48
 0:03:04
0:03:04
 0:03:33
0:03:33
 0:23:46
0:23:46
 0:08:12
0:08:12
 0:10:01
0:10:01
 0:02:05
0:02:05
 0:13:51
0:13:51