filmov
tv
Linux Intro: Signing and verifying data using GPG

Показать описание
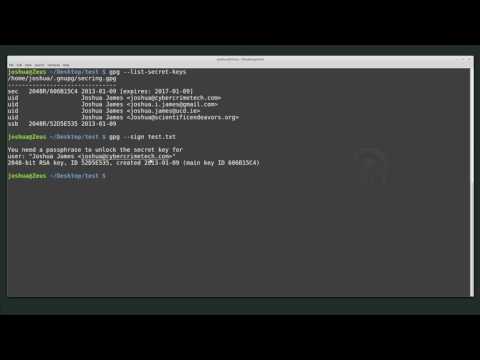
In this video we will be using GPG to sign and verify data. Signing is used as a secure way to check whether data has been modified from the time of signing. We sign the data with our private key. Other users can verify the data and signature by using your public key.
We are using Ubuntu Linux with the default install of GPG. Private keys were already generated.
010001000100011001010011011000110110100101100101011011100110001101100101
Get more Digital Forensic Science
010100110111010101100010011100110110001101110010011010010110001001100101
Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. Please link back to the original video. If you want to use this video for commercial purposes, please contact us first. We would love to see what you are doing.
We are using Ubuntu Linux with the default install of GPG. Private keys were already generated.
010001000100011001010011011000110110100101100101011011100110001101100101
Get more Digital Forensic Science
010100110111010101100010011100110110001101110010011010010110001001100101
Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. Please link back to the original video. If you want to use this video for commercial purposes, please contact us first. We would love to see what you are doing.
Linux Intro: Signing and verifying data using GPG
UEFI Linux Secure Boot Kernel Signing and Verification demo
Digital Signatures
Verify Digital Signatures (Linux)
Tsurugi Linux: Download, verify and first start
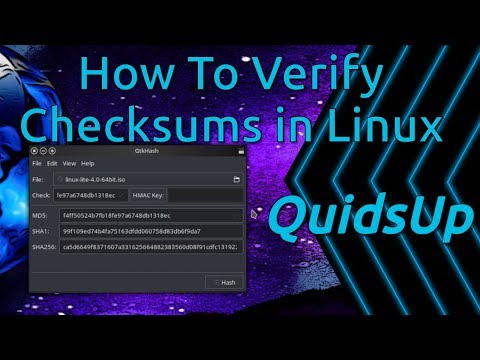
How to Verify Checksums In Linux
Linux Mint 22 Verify ISO
Howto Verify TailsOS ISO signature on Parrot Linux
How to Verify Checksum in Linux [GUI and Command Line]
Arch Linux VERIFY Aug 2024
Your Linux Server: Introduction 0001
How to verify signatures in Linux [HD]
Grokking Linux - A very brief intro to some terms for Linux Newbies
Introduction to Memory Management in Linux
Deepin Linux - Continuous Key Signing Party Introduction
'Basic Authentication' in Five Minutes
Linux Tutorial for Beginners - 9 - Verify Files Using Checksum
Hardware Wallets in TAILS or Ubuntu Linux - Verify GPG Electrum, udev rules, sweep Paper Wallet
How to verify authenticity of downloaded files on Linux
C++ Programming on Linux - OpenSSL RSA Digital Signature Sign and Verify
Arch Linux: PGP Signature Is Corrupted???
Intro to Linux Security
Secure boot in embedded Linux systems, Thomas Perrot
How to digitally sign a PDF file in Linux [Quick guide]
Комментарии
 0:08:31
0:08:31
 0:32:08
0:32:08
 0:03:36
0:03:36
 0:01:59
0:01:59
 0:14:14
0:14:14
 0:05:29
0:05:29
 0:28:24
0:28:24
 0:02:08
0:02:08
 0:03:56
0:03:56
 0:14:27
0:14:27
 0:18:13
0:18:13
 0:03:52
0:03:52
 0:19:11
0:19:11
 0:51:19
0:51:19
 0:18:24
0:18:24
 0:05:07
0:05:07
 0:08:03
0:08:03
 0:10:03
0:10:03
 0:06:08
0:06:08
 0:20:14
0:20:14
 0:11:33
0:11:33
 0:00:34
0:00:34
 0:21:47
0:21:47
 0:02:15
0:02:15