filmov
tv
3. Signatures

Показать описание
MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018
Instructor: Tadge Dryja
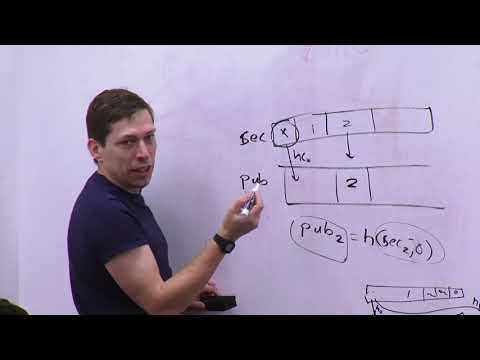
Discussion of hash signatures, public and private keys, examples of how to use elliptic curves vs. hashes.
License: Creative Commons BY-NC-SA
Instructor: Tadge Dryja
Discussion of hash signatures, public and private keys, examples of how to use elliptic curves vs. hashes.
License: Creative Commons BY-NC-SA
3. Signatures
Tutorial | Adding 3 Signatures | PLUS a helpful technique!
3/4 VS 6/8 Time Signatures
Sewing 3 Signatures for a Hidden Spine Junk Journal Tutorial!
How to make time signatures WAY less confusing
#3 How I Make Signatures for a Junk Journal, Junk Journal Tutorials, Pink Monarch Prints
Time Signatures Explained for Beginners - my formula to figure out any time signature!
Understanding Time Signatures in Music ⏰ (Essential Tips for Musicians)
✅ How to make Signature | Signature style of my name @SignatureExpert
What are Irrational time signatures?
The Difference Between 3/4 and 3/8 Time Signatures - Music Theory
Time signatures ⏳⌛️ in Piano Music 🎶
How to Identify Time Signatures by Ear [EXPLAINED]
All You Need to Know About Time Signatures | Guitar For Beginners
3 Stupid Mistakes To Avoid In Your Signatures
Time Signatures: Everything You Need to Know
Time Signatures Explained for Beginners with Lauren Bateman on Guitar
How to Sew Multiple Signatures into a Hardcover Junk Journal (Beginner Tutorial)
Bookbinding 3 signatures with some extras DIY EASY
Best Signatures 🖊️ ☠️ #edit #signature
The Difference Between 3/4 and 6/8 Time Signatures - Music Theory
Key Signatures - Everything You Need To Know in 6 minutes
What are Digital Signatures? - Computerphile
Biden-era document signatures 'automated' except letter dropping out of race, report says
Комментарии
 1:14:44
1:14:44
 0:33:19
0:33:19
 0:01:00
0:01:00
 0:39:07
0:39:07
 0:01:00
0:01:00
 0:06:02
0:06:02
 0:07:22
0:07:22
 0:14:54
0:14:54
 0:01:30
0:01:30
 0:00:59
0:00:59
 0:11:59
0:11:59
 0:00:15
0:00:15
 0:12:43
0:12:43
 0:06:14
0:06:14
 0:05:24
0:05:24
 0:12:53
0:12:53
 0:06:22
0:06:22
 0:24:02
0:24:02
 0:28:38
0:28:38
 0:00:27
0:00:27
 0:13:50
0:13:50
 0:06:02
0:06:02
 0:10:17
0:10:17
 0:00:37
0:00:37