filmov
tv
pfSense - Configure VPN Site to Site IPSec in pfSense Firewall

Показать описание
pfSense - Configure VPN Site to Site IPSec with Pre-Shared Keys in pfSense Firewall
📌 Firewall tutorials
✳️ pfSense Firewall
👉 How to Install and Configure pfSense Firewall on GNS3: updating
✳️ OPNSense Firewall
👉 How to Install and Configure OPNSense Firewall on GNS3: updating
✳️ FortiGate Firewall
👉 How to Install and Configure FortiGate Firewall on VMware Workstation: updating
👉 How to Install and Configure FortiGate Firewall on Virtualbox: updating
👉 How to Install and Configure FortiGate Firewall on Hyper-V: updating
👉 How to Install and Configure FortiGate Firewall on GNS3: updating
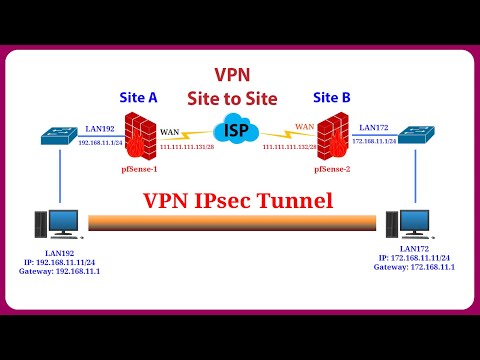
VPN Site-to-Site IPsec in pfSense is a powerful tool for establishing and maintaining secure links between different locations, enhancing network security and management.
🔸Data Encryption: Provides a layer of security by encrypting data transmitted over the VPN channel. This ensures that sensitive information, such as business data, cannot be intercepted or altered during transmission.
🔸Secure Authentication: Utilizes robust authentication methods to ensure the integrity of information. The IPsec protocol supports multiple authentication methods, including pre-shared keys and certificates.
🔸Integrated Security: Integrates tightly with other security features in pfSense, such as the firewall, to enhance safety and access control.
🔸Web Interface Management: Offers a simple and user-friendly web interface for configuring and managing VPN Site-to-Site IPsec connections. Administrators can make changes and monitor connection status remotely through a web browser.
🔸High Performance: Designed to deliver high and stable performance, ensuring that the network is maintained at maximum speed without compromising user experience.
🔸Cross-Platform Support: Supports multiple platforms, allowing connections between different devices and environments, facilitating integration and system scalability.
🔸Flexibility: Provides various configuration options, allowing administrators to adjust parameters such as IP addresses, encryption algorithms, and authentication methods to meet the specific needs of the organization.
📌 Firewall tutorials
✳️ pfSense Firewall
👉 How to Install and Configure pfSense Firewall on GNS3: updating
✳️ OPNSense Firewall
👉 How to Install and Configure OPNSense Firewall on GNS3: updating
✳️ FortiGate Firewall
👉 How to Install and Configure FortiGate Firewall on VMware Workstation: updating
👉 How to Install and Configure FortiGate Firewall on Virtualbox: updating
👉 How to Install and Configure FortiGate Firewall on Hyper-V: updating
👉 How to Install and Configure FortiGate Firewall on GNS3: updating
VPN Site-to-Site IPsec in pfSense is a powerful tool for establishing and maintaining secure links between different locations, enhancing network security and management.
🔸Data Encryption: Provides a layer of security by encrypting data transmitted over the VPN channel. This ensures that sensitive information, such as business data, cannot be intercepted or altered during transmission.
🔸Secure Authentication: Utilizes robust authentication methods to ensure the integrity of information. The IPsec protocol supports multiple authentication methods, including pre-shared keys and certificates.
🔸Integrated Security: Integrates tightly with other security features in pfSense, such as the firewall, to enhance safety and access control.
🔸Web Interface Management: Offers a simple and user-friendly web interface for configuring and managing VPN Site-to-Site IPsec connections. Administrators can make changes and monitor connection status remotely through a web browser.
🔸High Performance: Designed to deliver high and stable performance, ensuring that the network is maintained at maximum speed without compromising user experience.
🔸Cross-Platform Support: Supports multiple platforms, allowing connections between different devices and environments, facilitating integration and system scalability.
🔸Flexibility: Provides various configuration options, allowing administrators to adjust parameters such as IP addresses, encryption algorithms, and authentication methods to meet the specific needs of the organization.
Комментарии
 0:11:42
0:11:42
 0:12:54
0:12:54
 0:12:47
0:12:47
 0:17:07
0:17:07
 0:11:43
0:11:43
 0:14:23
0:14:23
 0:06:15
0:06:15
 0:19:12
0:19:12
 0:13:07
0:13:07
 0:20:29
0:20:29
 0:08:02
0:08:02
 0:09:22
0:09:22
 0:27:05
0:27:05
 0:31:49
0:31:49
 0:09:46
0:09:46
 0:13:55
0:13:55
 0:00:59
0:00:59
 0:45:07
0:45:07
 0:25:23
0:25:23
 0:11:28
0:11:28
 0:17:57
0:17:57
 0:12:32
0:12:32
 0:25:46
0:25:46
 0:09:00
0:09:00