filmov
tv
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150)
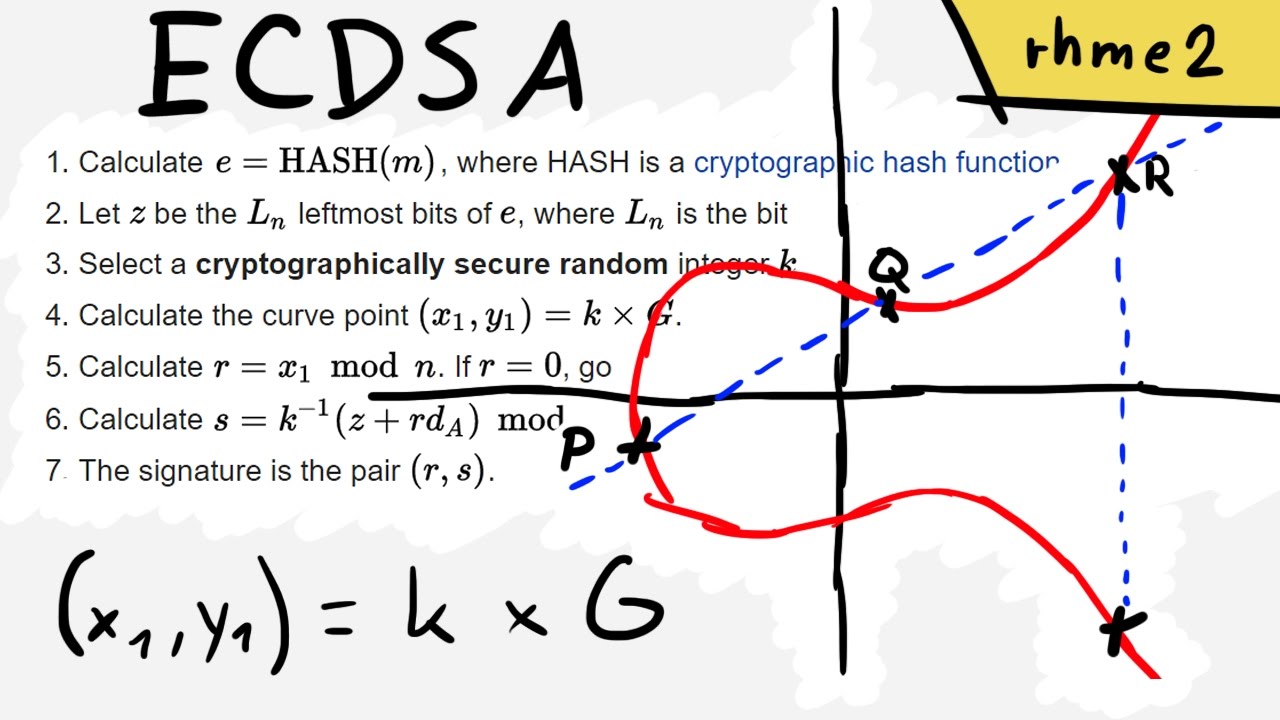
Показать описание
We are going to recover a ECDSA private key from bad signatures. Same issue the Playstation 3 had that allowed it to be hacked.
-=[ 🔴 Stuff I use ]=-
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#CTF #Cryptography
-=[ 🔴 Stuff I use ]=-
-=[ ❤️ Support ]=-
-=[ 🐕 Social ]=-
-=[ 📄 P.S. ]=-
All links with "*" are affiliate links.
LiveOverflow / Security Flag GmbH is part of the Amazon Affiliate Partner Programm.
#CTF #Cryptography
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150)
Elliptic Curve Cryptography Overview
Math Behind Bitcoin and Elliptic Curve Cryptography (Explained Simply)
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Curves which make Bitcoin possible.
Elliptic Curve Back Door - Computerphile
ECDSA Basics
Digital Signatures - ECDSA, EdDSA and Schnorr
Elliptic Curves and ECDSA - Bitcoin, Blockchain and Cryptoassets
Breaking encryption with 100x less qubits? #quantumcomputing #encryption #security
ECDSA, The Nonce and The Private Key
LadderLeak: Breaking ECDSA with Less than One Bit of Nonce Leakage
Elliptic Curve Cryptography: Key Exchange (ECDH), Digital Sig (ECDSA/EdDSA) and Encryption (ECIES)
Signature Malleability In 60 Seconds
Elliptic Curve Cryptography Tutorial - An Introduction to Elliptic Curve Cryptography
LadderLeak Breaking ECDSA with Less than One Bit of Nonce Leakage
Lesson 18: Elliptic Curve Cryptography
How did the NSA hack our emails?
Bitcoin's Elliptic Curve Algorithm Visualized / The Math Behind Bitcoin / ECDSA SECP256k1
Elliptic Curve Digital Signature Algorithm for Blockchains & Cryptocurrencies
Digital Signature Algorithm: ECDSA
Break RSA Encryption in 10 Lines of Python Code | #Shorts Quantum Computing with Shor's Algorit...
ECDSA & solving the Elliptic Curve Discrete Logarithm Problem
Elliptic Curve Digital Signature Algorithm (ECDSA) (Money Button Documentation Series)
Комментарии
 0:08:19
0:08:19
 0:11:29
0:11:29
 0:11:13
0:11:13
 0:11:34
0:11:34
 0:07:45
0:07:45
 0:12:24
0:12:24
 0:05:11
0:05:11
 0:19:51
0:19:51
 0:35:37
0:35:37
 0:00:39
0:00:39
 0:14:14
0:14:14
 0:34:12
0:34:12
 0:47:40
0:47:40
 0:00:46
0:00:46
 0:09:34
0:09:34
 0:34:12
0:34:12
 0:27:59
0:27:59
 0:10:59
0:10:59
 0:11:33
0:11:33
 0:20:43
0:20:43
 0:09:36
0:09:36
 0:00:39
0:00:39
 0:01:01
0:01:01
 0:34:46
0:34:46