filmov
tv
I hacked into my own car

Показать описание
You can buy my books here:
You can support me on Patreon and get access to the exclusive Discord:
just like these amazing people:
Glenn Watson
Peter Turner
Joël van der Loo
Matthew Cocke
Mark Brouwer
Deneb
You can support me on Patreon and get access to the exclusive Discord:
just like these amazing people:
Glenn Watson
Peter Turner
Joël van der Loo
Matthew Cocke
Mark Brouwer
Deneb
I Hacked Into My Own Car
I hacked into my own car
'I Show You How Easily Your Phone Can Be Hacked' Edward Snowden
I Hacked My Own School Using Kali Linux #kalilinux
Alright…Who hacked my Netflix account? #hacked #netflix #kurtcunning
This laptop was MADE to be HACKED!
he hacked my websites
Someone HACKED My ROBLOX Account! ⚠️
How To Recover Hacked Epic Games Account
How I hacked a hardware crypto wallet and recovered $2 million
3 SIGNS YOUR PHONE WAS HACKED!🤯
Your Friend Hacked Nintendo Switch!
Check Your PC/Laptop is Hacked or Not? #shorts
let's hack your home network // FREE CCNA // EP 9
How to hack wifi passwords : I Hacked Every WiFi Network In My Neighborhood
i HACKED my wife’s web browser (it’s SCARY easy!!)
I Hacked 1000 WiFi Passwords
Watch these hackers crack an ATM in seconds
I Secretly Hacked in My Schools SMP!
How to tell if your iphone has been hacked! #shorts
How to check if your #phone is #tapped or #Hacked . #iphone13
I hacked some LEGO Sonic sets to create my own dream Sonic level #ad #LEGOPartner
my fortnite account just got hacked
My Roblox Account Got HACKED LIVE in DOORS Stream 😱💀
Комментарии
 0:20:29
0:20:29
 0:01:01
0:01:01
 0:06:34
0:06:34
 0:00:09
0:00:09
 0:00:16
0:00:16
 0:13:11
0:13:11
 0:34:24
0:34:24
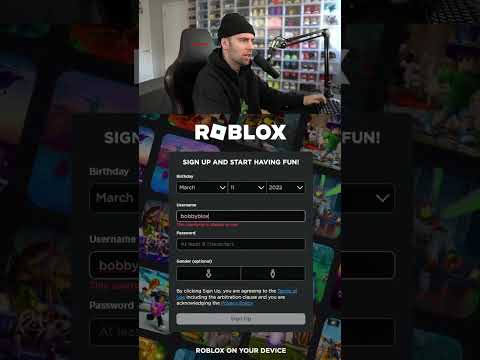 0:00:10
0:00:10
 0:01:12
0:01:12
 0:32:18
0:32:18
 0:00:31
0:00:31
 0:00:30
0:00:30
 0:00:12
0:00:12
 0:30:16
0:30:16
 0:00:16
0:00:16
 0:14:36
0:14:36
 0:00:33
0:00:33
 0:05:42
0:05:42
 0:19:23
0:19:23
 0:00:10
0:00:10
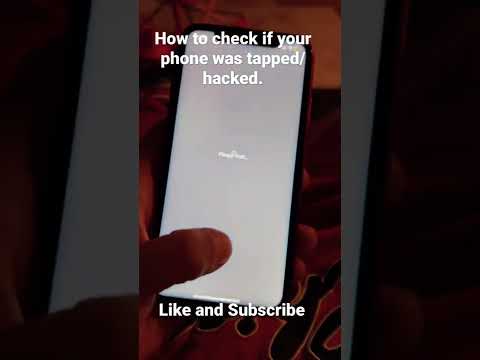 0:00:33
0:00:33
 0:00:47
0:00:47
 0:00:46
0:00:46
 0:00:35
0:00:35