filmov
tv
RSA and AES-256 Keys explained | Boxcryptor Encryption

Показать описание
𝗧𝗵𝗶𝘀 𝗶𝘀 𝗛𝗼𝘄 𝗘𝗻𝗰𝗿𝘆𝗽𝘁𝗶𝗼𝗻 𝘄𝗶𝘁𝗵 𝗕𝗼𝘅𝗰𝗿𝘆𝗽𝘁𝗼𝗿 𝗪𝗼𝗿𝗸𝘀
We encrypt files and thus provide increased protection against espionage and data theft. For #encryption, we use a combination of #AES-256 encryption and #RSA encryption. Here we explain the two algorithms.
𝗔𝗘𝗦-𝟮𝟱𝟲 𝗘𝗻𝗰𝗿𝘆𝗽𝘁𝗶𝗼𝗻
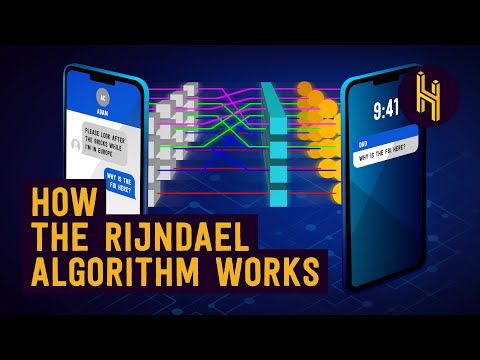
Advanced Encryption Standard (AES) is one of the most frequently used and most secure encryption algorithms available today. It is publicly accessible, and it is the cipher which the NSA uses for securing documents with the classification “top secret”. Based on the block structure of AES, the change of a single bit, either in the key, or in the plaintext block, results in a completely different ciphertext block – a clear advantage over traditional stream ciphers. The difference between AES-128, AES-192 and AES-256 finally is the length of the key: 128, 192 or 256 bit – all drastic improvements compared to the 56 bit key of DES. By way of illustration: Cracking a 128-bit AES key with a state-of-the-art supercomputer would take longer than the presumed age of the universe. And Boxcryptor even uses 256-bit keys. As of today, no practicable attack against AES exists. Therefore, AES remains the preferred encryption standard for governments, banks, and high security systems around the world.
𝗥𝗦𝗔 𝗘𝗻𝗰𝗿𝘆𝗽𝘁𝗶𝗼𝗻
RSA is one of the most successful, asymmetric encryption systems today.
As opposed to traditional, symmetric encryption systems, RSA works with two different keys: A public and a private one. Both work complementary to each other, which means that a message encrypted with one of them can only be decrypted by its counterpart. Since the private key cannot be calculated from the public key, the latter is generally available to the public.
Boxcryptor implements a combined encryption process based on asymmetric RSA and symmetric AES encryption. Every file has its own unique random file key, which is generated when the file is being created.
We encrypt files and thus provide increased protection against espionage and data theft. For #encryption, we use a combination of #AES-256 encryption and #RSA encryption. Here we explain the two algorithms.
𝗔𝗘𝗦-𝟮𝟱𝟲 𝗘𝗻𝗰𝗿𝘆𝗽𝘁𝗶𝗼𝗻
Advanced Encryption Standard (AES) is one of the most frequently used and most secure encryption algorithms available today. It is publicly accessible, and it is the cipher which the NSA uses for securing documents with the classification “top secret”. Based on the block structure of AES, the change of a single bit, either in the key, or in the plaintext block, results in a completely different ciphertext block – a clear advantage over traditional stream ciphers. The difference between AES-128, AES-192 and AES-256 finally is the length of the key: 128, 192 or 256 bit – all drastic improvements compared to the 56 bit key of DES. By way of illustration: Cracking a 128-bit AES key with a state-of-the-art supercomputer would take longer than the presumed age of the universe. And Boxcryptor even uses 256-bit keys. As of today, no practicable attack against AES exists. Therefore, AES remains the preferred encryption standard for governments, banks, and high security systems around the world.
𝗥𝗦𝗔 𝗘𝗻𝗰𝗿𝘆𝗽𝘁𝗶𝗼𝗻
RSA is one of the most successful, asymmetric encryption systems today.
As opposed to traditional, symmetric encryption systems, RSA works with two different keys: A public and a private one. Both work complementary to each other, which means that a message encrypted with one of them can only be decrypted by its counterpart. Since the private key cannot be calculated from the public key, the latter is generally available to the public.
Boxcryptor implements a combined encryption process based on asymmetric RSA and symmetric AES encryption. Every file has its own unique random file key, which is generated when the file is being created.
 0:02:43
0:02:43
 0:11:11
0:11:11
 0:08:40
0:08:40
 0:14:14
0:14:14
 0:10:17
0:10:17
 0:04:40
0:04:40
 0:03:33
0:03:33
 0:05:51
0:05:51
 0:34:30
0:34:30
 0:11:55
0:11:55
 0:05:06
0:05:06
 0:08:45
0:08:45
 0:06:42
0:06:42
 0:19:40
0:19:40
 0:05:10
0:05:10
 0:09:11
0:09:11
 0:15:48
0:15:48
 0:06:20
0:06:20
 0:10:45
0:10:45
 0:15:06
0:15:06
 0:10:17
0:10:17
 0:11:30
0:11:30
 0:08:16
0:08:16
 0:02:49
0:02:49