filmov
tv
File System in OS II - Data Allocation | File System | Data allocation methods | system requirements

Показать описание
This video talks at length about data allocation methods used by file systems to store files on hard drive. File system provides the user various features to store and manipulate their data. File systems have various requirements and one should learn the advantages and disadvantages of various data memory allocation methods in the operating system.
This is the 2nd of the 3 video series on File Systems. This video talks about the requirements of a file system while translating from user to system view. This requires that we know about user access and usage patterns that are captured from years of analysis and experience. This is very important because while designing a file system we want to accommodate the user in how they want to access and control their files.
As the prime responsibility of the File system is to map the user files onto the physical sectors of a disk drive in a way that is efficient so that the user could access their files with ease. The video talks in detail about the data allocation techniques that are evaluated against the most important operations and usage patterns such as sequential and random accesses.
This is the 2nd of the 3 video series on File Systems. This video talks about the requirements of a file system while translating from user to system view. This requires that we know about user access and usage patterns that are captured from years of analysis and experience. This is very important because while designing a file system we want to accommodate the user in how they want to access and control their files.
As the prime responsibility of the File system is to map the user files onto the physical sectors of a disk drive in a way that is efficient so that the user could access their files with ease. The video talks in detail about the data allocation techniques that are evaluated against the most important operations and usage patterns such as sequential and random accesses.
Комментарии
 0:09:55
0:09:55
 0:02:44
0:02:44
 0:12:03
0:12:03
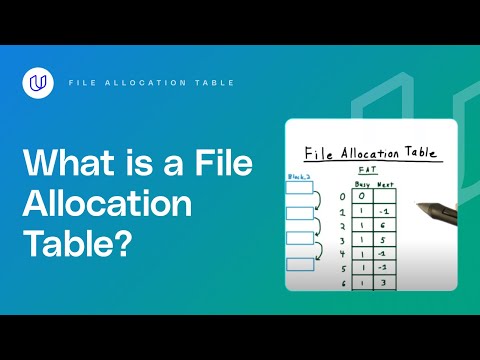 0:02:55
0:02:55
 0:02:53
0:02:53
 0:20:33
0:20:33
 0:06:38
0:06:38
 0:05:16
0:05:16
 0:22:42
0:22:42
 0:11:05
0:11:05
 0:06:03
0:06:03
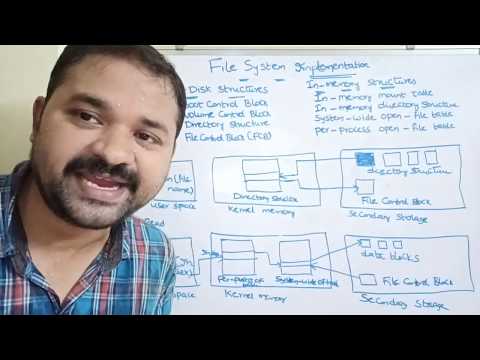 0:10:27
0:10:27
 0:13:25
0:13:25
 0:11:14
0:11:14
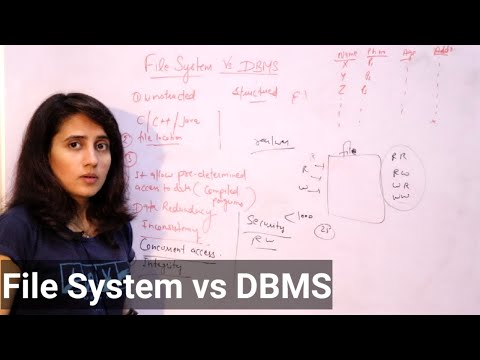 0:23:18
0:23:18
 0:07:54
0:07:54
 0:08:04
0:08:04
 0:15:59
0:15:59
 0:07:18
0:07:18
 0:08:01
0:08:01
 0:21:20
0:21:20
 0:00:51
0:00:51
 0:05:40
0:05:40
 0:06:01
0:06:01