filmov
tv
MicroNugget: How to Contain Rogue Access Points in a WLAN

Показать описание
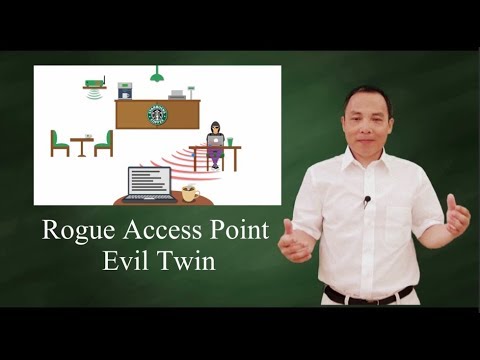
In this video, Keith Barker covers containing rogue access points in a wireless network. If you're running a network, the last thing you need is one of your users finding their way to a malicious network that's spoofing your SSID. Find them and stop them with WLCs.
Large corporate infrastructures or places like airports are common targets for malicious actors to set up a network that looks and feels a lot like your own. They're on the hunt for your users. If they can spoof your network and SSID successfully, they can get one of your users to use their system and compromise them. Then they might turn that device around and use it for a man-in-the-middle attack on your own network and eavesdrop all the traffic that passes through the device.
But wireless LAN controllers are always listening to their downstream access points, who are - in turn - scanning other channels and reporting back to their WLCs what other access points are broadcasting in nearby ranges. The WLC registers those rogue access points, and if you know how to find that registry, you can act to contain the threats.
Start learning with CBT Nuggets:
Комментарии
 0:07:21
0:07:21
 0:01:58
0:01:58
 0:04:35
0:04:35
 0:15:16
0:15:16
 0:00:34
0:00:34
 0:03:43
0:03:43
 0:04:12
0:04:12
 0:07:03
0:07:03
 0:08:58
0:08:58
 0:00:55
0:00:55
 0:05:59
0:05:59
 0:05:22
0:05:22
 0:44:01
0:44:01
 0:22:50
0:22:50
 0:01:06
0:01:06
 0:09:01
0:09:01
 0:05:26
0:05:26
 0:01:01
0:01:01
 0:04:16
0:04:16
 0:01:46
0:01:46
 0:02:20
0:02:20
 0:02:31
0:02:31
 0:00:59
0:00:59
 0:02:38
0:02:38