filmov
tv
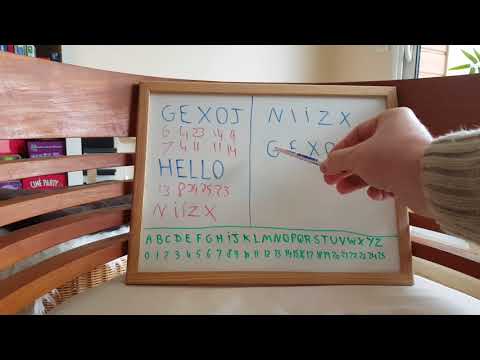
How to Send an Unbreakable Encrypted Secret Message.

Показать описание
Subscribe to my alternate platforms:
Send Bitcoins to: bc1qc5jq4dxt7359sh80lkv9v8rlsgnh322hmn6xyc Send Ethereum : 0xe7cC2e415E0D2d1De91604B2b693f124dfBCf9B8
Send Litecoin : LYwDy55mZSeb1Czx6JUiTS5YkqjfmWKK5H
Send Bitcoins to: bc1qc5jq4dxt7359sh80lkv9v8rlsgnh322hmn6xyc Send Ethereum : 0xe7cC2e415E0D2d1De91604B2b693f124dfBCf9B8
Send Litecoin : LYwDy55mZSeb1Czx6JUiTS5YkqjfmWKK5H
How to Send an Unbreakable Encrypted Secret Message.
HOW TO SEND MAIL ANONYMOUSLY TO ANYONE WITH UNBREAKABLE PRIVACY 100% WORKING ~by TECHNICAL RAHEEM
World’s Strongest Man vs Unbreakable Car (video credit: @PrestonYT)
Encrypted Cellphones 2021: How to secretly send unbreakable messages on all social media
Dusk Explained: Zero-Knowledge Demystified, AKA Unbreakable Privacy
Unbreakable Water Glass vs. Some Idiot #shorts #unbreakable #destroy #viral #glass #water #crazy
unbreakable lighting mug, ## send to oder ## Free home delivery, Mo-7622967345
how to make unbreakable blocks in minecraft using 1 command! (1.16.5+!)
Creating Unbreakable Bonds
Hollow Knight - How to Make Fragile Charms Unbreakable
The Unbreakable Kryptos Code
Can We Make Encryption That's 'Unbreakable?' | John Prisco | TEDxMidAtlantic
Why did you send me an unbreakable plane?
Jocko Willink's Secrets to Building an Unbreakable Mindset
Priyanka Chopra and Dwayne Johnson's Unbreakable Friendship 💪👫 #shorts #priyankajonas
Voicians - Unbreakable
Destroy The Unbreakable Cube, Win $1,000!
UNBREAKABLE: The Western States 100 - Feature Film - Limited Release
Unbreakable Umbrella Thoughts and Tips
My Four Unbreakable Rules
❤️ Send to someone who u wanna have unbreakable Bond....
MrBeast Trapped me in an Unbreakable Box and this happened..
'Brotherhood Unbreakable: Supporting Each Other Through Thick and Thin!' 💪 #shorts
TRAPPED THE GIRLS IN AN UNBREAKABLE BOX!!
Комментарии
 0:10:01
0:10:01
 0:04:52
0:04:52
 0:00:44
0:00:44
 0:00:13
0:00:13
 0:04:47
0:04:47
 0:00:43
0:00:43
 0:00:14
0:00:14
 0:02:59
0:02:59
 1:02:43
1:02:43
 0:10:34
0:10:34
 0:47:01
0:47:01
 0:13:34
0:13:34
 0:00:08
0:00:08
 0:00:18
0:00:18
 0:00:15
0:00:15
 0:03:03
0:03:03
 0:30:15
0:30:15
 1:45:55
1:45:55
 0:04:12
0:04:12
 0:01:41
0:01:41
 0:00:09
0:00:09
 0:00:45
0:00:45
 0:00:26
0:00:26
 0:10:46
0:10:46