filmov
tv
What is LDAP? Lightweight Directory Access Protocol Explained #Security #SSO #Authentication #Okta

Показать описание
LDAP (Lightweight Directory Access Protocol) is an open, vendor-neutral application protocol used to access and manage directory services over an IP network. It provides a standard way to store and retrieve hierarchical information in a directory, often used to authenticate and authorize users, manage user accounts, and store metadata about objects within a network.
Key Concepts of LDAP:
1. Directory Services:
LDAP is used to interact with directory services, which are specialized databases optimized for read-intensive tasks. Unlike traditional databases, directory services are designed for storing hierarchical data such as users, groups, devices, and other objects in a network.
A directory is essentially a type of database, but it is structured in a tree-like hierarchy that resembles a file system. It stores information in the form of objects, such as users, computers, printers, and more.
2. LDAP Data Model:
Entries: LDAP stores information in "entries." Each entry is a collection of attributes and values that define the object. For example, a user entry might have attributes like uid, cn (common name), sn (surname), mail, etc.
Distinguished Names (DNs): Each entry has a unique identifier called a Distinguished Name (DN). A DN specifies the location of an entry within the directory hierarchy. It is a combination of attribute-value pairs (e.g., uid=johndoe,ou=users,dc=example,dc=com).
Organizational Units (OUs): These are containers for entries and help to organize the directory. For instance, you might have ou=users and ou=groups as separate organizational units in the directory.
Attributes: Each entry contains a set of attributes that describe the object. Attributes have types (such as cn, mail, or telephoneNumber) and values.
3. LDAP Protocol Operations:
LDAP supports various operations to query and modify the directory. Common operations include:
Bind: Authenticates a client to the directory server.
Search: Retrieves entries from the directory that match a search filter.
Compare: Compares an entry’s attribute value with a given value.
Add: Adds a new entry to the directory.
Delete: Deletes an entry from the directory.
Modify: Updates the attributes of an existing entry.
Unbind: Terminates the session between the client and the LDAP server.
4. LDAP Schema:
A schema defines the rules and structure of the directory. It dictates which object classes are allowed, what attributes they can have, and the data types of these attributes. Common LDAP object classes include inetOrgPerson (for user entries) and groupOfNames (for groups).
The schema enforces consistency in the directory by ensuring that all entries conform to these predefined rules.
5. Authentication and Authorization:
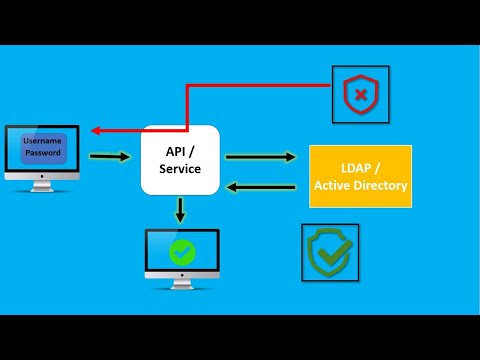
LDAP is frequently used for authentication and authorization in networked environments. When a user tries to access a system, LDAP verifies their credentials (username and password) and retrieves their authorization details (e.g., roles or group memberships).
Simple Authentication: In its basic form, LDAP supports simple authentication where the user’s DN and password are checked against the directory.
SASL Authentication: For stronger security, LDAP can use the Simple Authentication and Security Layer (SASL), which supports more complex mechanisms like Kerberos or SSL/TLS.
6. Security:
LDAP over SSL (LDAPS): LDAP can operate over SSL/TLS (Secure Sockets Layer/Transport Layer Security) to encrypt communication between the client and server. This ensures that credentials and other sensitive data are not transmitted in plain text.
Access Control Lists (ACLs): LDAP servers use ACLs to control who has permission to read, modify, or delete entries. ACLs define rules based on users' DNs, group memberships, and other attributes.
LDAP Use Cases:
Centralized Authentication: LDAP is commonly used in organizations for centralized user authentication and authorization across various services like email, file servers, VPN, and web applications. Systems such as Active Directory (which is based on LDAP) are used to manage users, computers, and other resources within a domain.
Single Sign-On (SSO): LDAP is often integrated with SSO systems to allow users to authenticate once and gain access to multiple systems without having to log in separately to each.
Directory-Based Services: Applications that need to store hierarchical information—such as email address books, organizational charts, or network resources—often rely on LDAP as the backend directory service.
Active Directory Integration: Microsoft Active Directory, one of the most widely used directory services, uses LDAP for querying and managing objects such as users, groups, and devices in a Windows domain environment.
Network Device Management: Network devices (routers, switches, firewalls) can use LDAP to authenticate administrators and users, ensuring secure access to the network infrastructure.
Key Concepts of LDAP:
1. Directory Services:
LDAP is used to interact with directory services, which are specialized databases optimized for read-intensive tasks. Unlike traditional databases, directory services are designed for storing hierarchical data such as users, groups, devices, and other objects in a network.
A directory is essentially a type of database, but it is structured in a tree-like hierarchy that resembles a file system. It stores information in the form of objects, such as users, computers, printers, and more.
2. LDAP Data Model:
Entries: LDAP stores information in "entries." Each entry is a collection of attributes and values that define the object. For example, a user entry might have attributes like uid, cn (common name), sn (surname), mail, etc.
Distinguished Names (DNs): Each entry has a unique identifier called a Distinguished Name (DN). A DN specifies the location of an entry within the directory hierarchy. It is a combination of attribute-value pairs (e.g., uid=johndoe,ou=users,dc=example,dc=com).
Organizational Units (OUs): These are containers for entries and help to organize the directory. For instance, you might have ou=users and ou=groups as separate organizational units in the directory.
Attributes: Each entry contains a set of attributes that describe the object. Attributes have types (such as cn, mail, or telephoneNumber) and values.
3. LDAP Protocol Operations:
LDAP supports various operations to query and modify the directory. Common operations include:
Bind: Authenticates a client to the directory server.
Search: Retrieves entries from the directory that match a search filter.
Compare: Compares an entry’s attribute value with a given value.
Add: Adds a new entry to the directory.
Delete: Deletes an entry from the directory.
Modify: Updates the attributes of an existing entry.
Unbind: Terminates the session between the client and the LDAP server.
4. LDAP Schema:
A schema defines the rules and structure of the directory. It dictates which object classes are allowed, what attributes they can have, and the data types of these attributes. Common LDAP object classes include inetOrgPerson (for user entries) and groupOfNames (for groups).
The schema enforces consistency in the directory by ensuring that all entries conform to these predefined rules.
5. Authentication and Authorization:
LDAP is frequently used for authentication and authorization in networked environments. When a user tries to access a system, LDAP verifies their credentials (username and password) and retrieves their authorization details (e.g., roles or group memberships).
Simple Authentication: In its basic form, LDAP supports simple authentication where the user’s DN and password are checked against the directory.
SASL Authentication: For stronger security, LDAP can use the Simple Authentication and Security Layer (SASL), which supports more complex mechanisms like Kerberos or SSL/TLS.
6. Security:
LDAP over SSL (LDAPS): LDAP can operate over SSL/TLS (Secure Sockets Layer/Transport Layer Security) to encrypt communication between the client and server. This ensures that credentials and other sensitive data are not transmitted in plain text.
Access Control Lists (ACLs): LDAP servers use ACLs to control who has permission to read, modify, or delete entries. ACLs define rules based on users' DNs, group memberships, and other attributes.
LDAP Use Cases:
Centralized Authentication: LDAP is commonly used in organizations for centralized user authentication and authorization across various services like email, file servers, VPN, and web applications. Systems such as Active Directory (which is based on LDAP) are used to manage users, computers, and other resources within a domain.
Single Sign-On (SSO): LDAP is often integrated with SSO systems to allow users to authenticate once and gain access to multiple systems without having to log in separately to each.
Directory-Based Services: Applications that need to store hierarchical information—such as email address books, organizational charts, or network resources—often rely on LDAP as the backend directory service.
Active Directory Integration: Microsoft Active Directory, one of the most widely used directory services, uses LDAP for querying and managing objects such as users, groups, and devices in a Windows domain environment.
Network Device Management: Network devices (routers, switches, firewalls) can use LDAP to authenticate administrators and users, ensuring secure access to the network infrastructure.
 0:01:51
0:01:51
 0:07:33
0:07:33
 0:09:07
0:09:07
 0:14:19
0:14:19
 0:02:57
0:02:57
 0:03:46
0:03:46
 0:03:12
0:03:12
 0:13:59
0:13:59
 0:04:01
0:04:01
 0:11:17
0:11:17
 0:03:46
0:03:46
 0:03:49
0:03:49
 0:06:28
0:06:28
 0:00:59
0:00:59
 0:03:27
0:03:27
 0:00:43
0:00:43
 0:00:08
0:00:08
 0:02:35
0:02:35
 0:03:12
0:03:12
 0:00:38
0:00:38
 0:00:16
0:00:16
 0:03:28
0:03:28
 0:16:55
0:16:55
 0:03:23
0:03:23