filmov
tv
Cryptography Coding - Essential Steps Revealed #crypto #codinglife #programminglanguage

Показать описание
Developing cryptography coding involves several steps, including understanding cryptographic principles, choosing appropriate algorithms, implementing them securely, and testing for robustness. Below is a basic guide to get you started:
Understand Cryptographic Principles: Before you start coding, it's essential to have a solid understanding of cryptographic principles, including encryption, decryption, hashing, digital signatures, key management, and secure protocols.
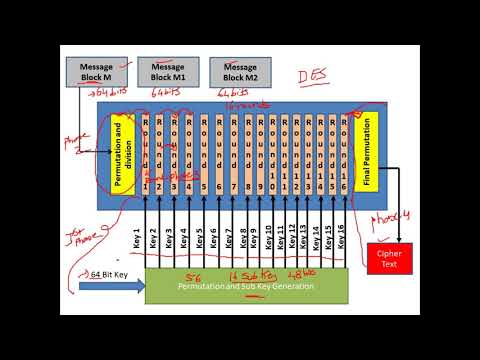
Select Cryptographic Algorithms: Choose the appropriate cryptographic algorithms based on your requirements. Common symmetric encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and symmetric-key ciphers. Asymmetric encryption algorithms include RSA, ECC (Elliptic Curve Cryptography), and Diffie-Hellman key exchange. For hashing, consider algorithms like SHA-256, SHA-3, or bcrypt for password hashing.
Choose Programming Language and Libraries: Select a programming language suitable for your project. Python, Java, C/C++, and Go are popular choices for cryptography coding. Additionally, utilize cryptographic libraries like OpenSSL, Bouncy Castle, or PyCryptodome, which provide implementations of various cryptographic algorithms and protocols.
Implement Encryption and Decryption Functions: Write functions to perform encryption and decryption using the chosen algorithms. Ensure that the implementation follows best practices for security, such as proper key management, padding (for block ciphers), and mode of operation (e.g., ECB, CBC, GCM).
Implement Hashing Functions: Create functions for hashing data using cryptographic hash functions. Ensure that the implementation prevents common vulnerabilities such as collision attacks and length extension attacks.
Key Management: Implement key generation, storage, and distribution mechanisms securely. Keys should be generated using cryptographically secure random number generators and protected from unauthorized access.
Secure Communication Protocols: If your project involves secure communication, implement secure protocols such as SSL/TLS or implement cryptographic primitives over lower-level protocols like TCP/IP.
Testing and Validation: Thoroughly test your cryptographic code to ensure its correctness, security, and performance. Test for edge cases, interoperability, resistance to known attacks, and compliance with relevant standards. Consider using automated testing tools and techniques such as fuzz testing.
Documentation and Best Practices: Document your cryptographic code thoroughly, including usage instructions, security considerations, and API documentation. Follow best practices for secure coding, such as avoiding hardcoding of sensitive information, using secure memory handling, and staying updated on security advisories.
Peer Review and Audit: Have your code reviewed by peers or security experts to identify potential vulnerabilities and ensure its security. Consider undergoing a security audit by third-party experts to validate the security of your cryptographic implementation.
Remember that cryptography is a complex field, and implementing cryptographic code securely requires careful consideration of various factors. Additionally, staying updated on the latest developments, vulnerabilities, and best practices in cryptography is essential for maintaining the security of your code.
Thank you
Everyday Be Coding
Understand Cryptographic Principles: Before you start coding, it's essential to have a solid understanding of cryptographic principles, including encryption, decryption, hashing, digital signatures, key management, and secure protocols.
Select Cryptographic Algorithms: Choose the appropriate cryptographic algorithms based on your requirements. Common symmetric encryption algorithms include AES (Advanced Encryption Standard), DES (Data Encryption Standard), and symmetric-key ciphers. Asymmetric encryption algorithms include RSA, ECC (Elliptic Curve Cryptography), and Diffie-Hellman key exchange. For hashing, consider algorithms like SHA-256, SHA-3, or bcrypt for password hashing.
Choose Programming Language and Libraries: Select a programming language suitable for your project. Python, Java, C/C++, and Go are popular choices for cryptography coding. Additionally, utilize cryptographic libraries like OpenSSL, Bouncy Castle, or PyCryptodome, which provide implementations of various cryptographic algorithms and protocols.
Implement Encryption and Decryption Functions: Write functions to perform encryption and decryption using the chosen algorithms. Ensure that the implementation follows best practices for security, such as proper key management, padding (for block ciphers), and mode of operation (e.g., ECB, CBC, GCM).
Implement Hashing Functions: Create functions for hashing data using cryptographic hash functions. Ensure that the implementation prevents common vulnerabilities such as collision attacks and length extension attacks.
Key Management: Implement key generation, storage, and distribution mechanisms securely. Keys should be generated using cryptographically secure random number generators and protected from unauthorized access.
Secure Communication Protocols: If your project involves secure communication, implement secure protocols such as SSL/TLS or implement cryptographic primitives over lower-level protocols like TCP/IP.
Testing and Validation: Thoroughly test your cryptographic code to ensure its correctness, security, and performance. Test for edge cases, interoperability, resistance to known attacks, and compliance with relevant standards. Consider using automated testing tools and techniques such as fuzz testing.
Documentation and Best Practices: Document your cryptographic code thoroughly, including usage instructions, security considerations, and API documentation. Follow best practices for secure coding, such as avoiding hardcoding of sensitive information, using secure memory handling, and staying updated on security advisories.
Peer Review and Audit: Have your code reviewed by peers or security experts to identify potential vulnerabilities and ensure its security. Consider undergoing a security audit by third-party experts to validate the security of your cryptographic implementation.
Remember that cryptography is a complex field, and implementing cryptographic code securely requires careful consideration of various factors. Additionally, staying updated on the latest developments, vulnerabilities, and best practices in cryptography is essential for maintaining the security of your code.
Thank you
Everyday Be Coding
 0:11:55
0:11:55
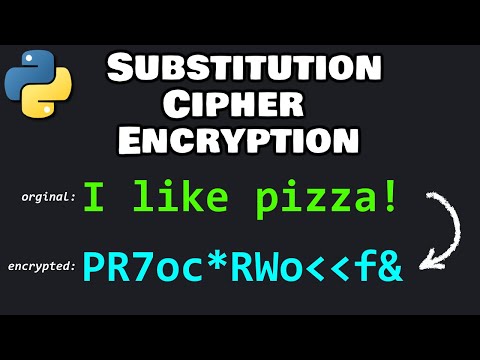 0:08:41
0:08:41
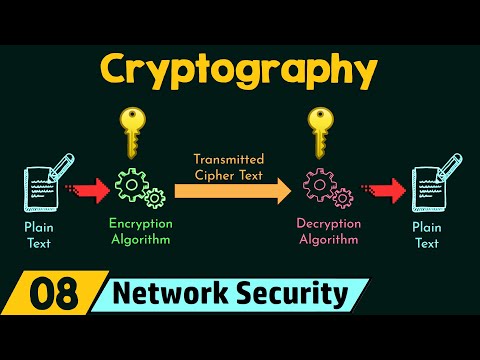 0:13:34
0:13:34
 2:15:01
2:15:01
 0:08:21
0:08:21
 0:17:31
0:17:31
 0:11:34
0:11:34
 0:08:40
0:08:40
 0:05:43
0:05:43
 0:06:14
0:06:14
 0:13:58
0:13:58
 0:06:20
0:06:20
 0:04:40
0:04:40
 0:05:17
0:05:17
 0:06:05
0:06:05
 0:12:33
0:12:33
 0:18:35
0:18:35
 0:00:41
0:00:41
 0:14:14
0:14:14
 0:43:30
0:43:30
 0:07:39
0:07:39
 0:06:55
0:06:55
 0:02:49
0:02:49
 0:51:39
0:51:39