filmov
tv
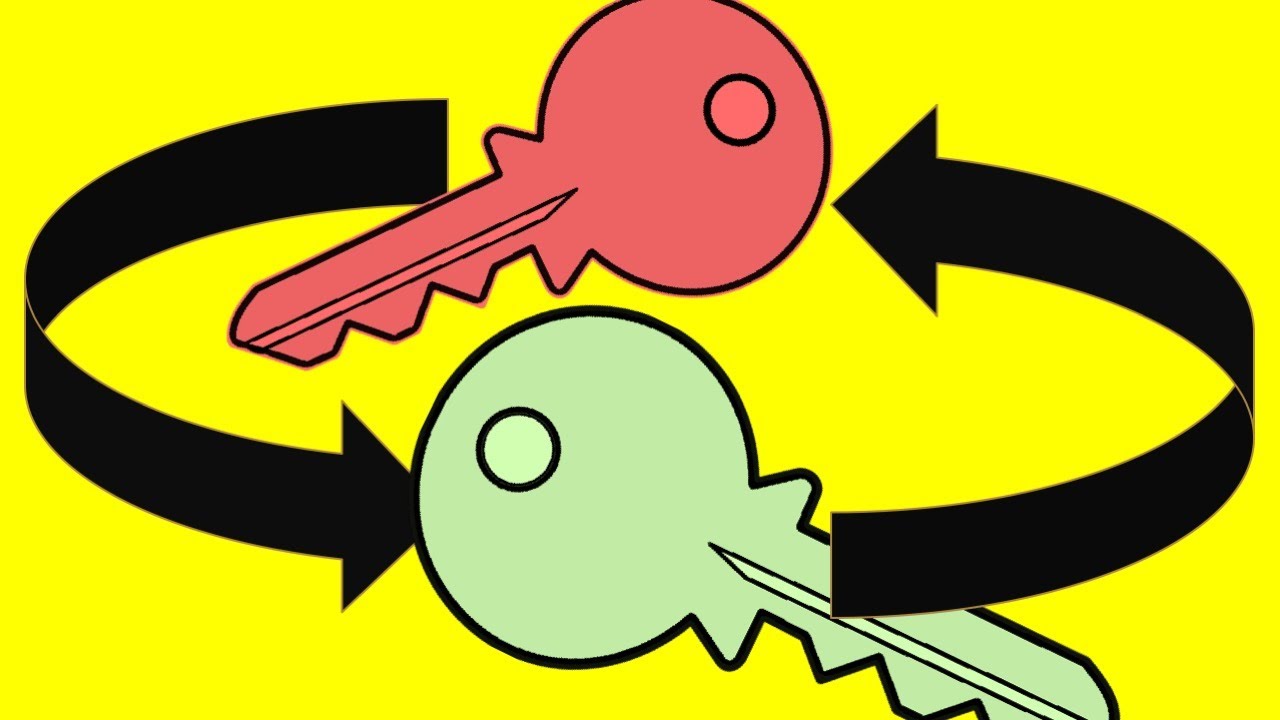
What is Public and Private Key Encryption?
Показать описание
How does public and private key encryption work? How is asynchronous encryption different than symmetric encryption?
Full course playlist for secure web development
Full course playlist for Information Security
Contents
0:00 Types of cryptography - Caesar DES AES asymmetric and hashing
0:45 Symmetric vs asymmetric encryption
1:15 public vs private keys
1:30 Whitfield Diffie New Directions in Cryptography
1:55 PGP Phil Zimmerman 1991 US Customs
2:50 Symmetric Encryption Standard Password Problems
4:10 Asymmetric encryption advantages
4:50 GPG gen-key
5:10 Share public key in GPG
5:35 import public key into gpg encrypt for user
Full course playlist for secure web development
Full course playlist for Information Security
Contents
0:00 Types of cryptography - Caesar DES AES asymmetric and hashing
0:45 Symmetric vs asymmetric encryption
1:15 public vs private keys
1:30 Whitfield Diffie New Directions in Cryptography
1:55 PGP Phil Zimmerman 1991 US Customs
2:50 Symmetric Encryption Standard Password Problems
4:10 Asymmetric encryption advantages
4:50 GPG gen-key
5:10 Share public key in GPG
5:35 import public key into gpg encrypt for user
Private Sector vs. Public Sector
What's Private and Public Sector? (Ep. 42)
Public vs Private IP Address
The Difference Between Public and Private Companies
public, private, and static in Java
The internet: public or private? | #PublicInterestTech
Private and Public Places Social Story
Public And Private Access Specifiers | C++ Tutorial
Maximize Your Sales: Showcasing Your Products in Public & Private Showrooms | Get to Know inFlow
The difference between public and private companies: Yahoo U explains
A quick introduction to Public-Private Partnership
Java Programming Tutorial 55 - Public vs Private
IP address : Public and Private IP address explained | CCNA 200-301
C# Programming Tutorial 58 - Public vs Private
What is the Difference Between Public & Private IP?
Public Cloud vs Private Cloud vs Hybrid Cloud
Private vs Public limited company: Difference between them with definition & comparison chart
What is a Private Cloud? Private vs. Public Cloud
Public versus private law
Networking - What is a the Difference Between a Public and Private IP Address?
OOP in C++ : How Public, Private & Protected Keyword impacts Inheritance
What is Public and Private Key Encryption?
Private School vs Public School - How Do The Students Compare?
Public v. Private Property [Introduction to Common Law] [No. 86]
Комментарии
 0:02:11
0:02:11
 0:05:30
0:05:30
 0:07:11
0:07:11
 0:02:39
0:02:39
 0:05:21
0:05:21
 0:03:12
0:03:12
 0:01:21
0:01:21
 0:08:49
0:08:49
 0:04:56
0:04:56
 0:02:00
0:02:00
 0:04:48
0:04:48
 0:05:00
0:05:00
 0:02:41
0:02:41
 0:05:20
0:05:20
 0:03:34
0:03:34
 0:03:28
0:03:28
 0:05:03
0:05:03
 0:02:20
0:02:20
 0:03:13
0:03:13
 0:01:27
0:01:27
 0:06:38
0:06:38
 0:06:55
0:06:55
 0:06:53
0:06:53
 0:03:16
0:03:16