filmov
tv
Cryptography Part 5: Key Management

Показать описание
In this lesson, I describe methods of protecting and safely using private and symmetric keys, including secure key generation, separation of duties, dual control, and split knowledge. You can download the script for this video at the beginning or the end of the video.
Cryptography Part 5: Key Management
Cryptographic Key Management Practices
Learn Cryptography | Part 5 - Hash Functions
Cryptography and Network Security Part 5/5 | WIlliam Stallings |Secure communication - S8 EC, CS,KTU
Cryptographic Key Management Policy Walkthrough
The Role of Cryptography - Part 5
Cryptography: Key Exchange
5 minutes of...Key Management in a Pervasive Encryption world
CompTIA Security+ SY0-701 Practice test OBJ 1.4
Key Management - IPSEC ( KTU CSE 409 Cryptography & Network Security - Module 5)
CSS322, Lecture 21, 25 Jan 2013 - Key Management with Symmetric Encryption
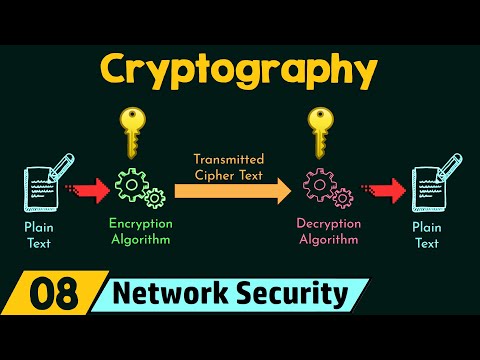
Cryptography
Asymmetric Encryption - Simply explained
Part 5 - 6.0 Digital Locksmithing - Cryptography and Encryption
Key Management and Key Distribution in Cryptography | Key Management | Key Distribution
CIS Part 5 | Simple Cryptography Solves Biggest Enterprise Risk - PASSWORD
8 Cryptographic Key Management Best Practices
LTE Security Part 5: Key Hierarchy
LECTURE 2 - AUTHENTICATION AND BASIC CRYPTOGRAPHY (PART 5)
Security of RSA - Asymmetric Cryptography and Key Management
5. Applied Cryptography and Trust: Key Exchange
Foundations of Cryptography 5-5: Key Escrow
Security - Key Management Service
Learn Cryptography | Part 1 - Introduction to Cryptography Risk
Комментарии
 0:06:05
0:06:05
 0:12:59
0:12:59
 0:24:26
0:24:26
 0:37:29
0:37:29
 0:03:10
0:03:10
 0:06:35
0:06:35
 0:12:30
0:12:30
 0:07:11
0:07:11
 0:10:58
0:10:58
 0:18:45
0:18:45
 1:12:39
1:12:39
 0:13:34
0:13:34
 0:04:40
0:04:40
 0:18:21
0:18:21
 0:06:57
0:06:57
 1:08:45
1:08:45
 0:02:52
0:02:52
 0:07:20
0:07:20
 0:06:19
0:06:19
 0:05:27
0:05:27
 0:27:36
0:27:36
 0:05:11
0:05:11
 0:01:33
0:01:33
 0:17:16
0:17:16