filmov
tv
Understanding Stack-Based Buffer Overrun in C++ Memory Operation Code

Показать описание
Explore the causes of stack-based buffer overrun in C++ memory operation code, and understand how to detect and prevent these issues.
---
Disclaimer/Disclosure - Portions of this content were created using Generative AI tools, which may result in inaccuracies or misleading information in the video. Please keep this in mind before making any decisions or taking any actions based on the content. If you have any concerns, don't hesitate to leave a comment. Thanks.
---
Understanding Stack-Based Buffer Overrun in C++ Memory Operation Code
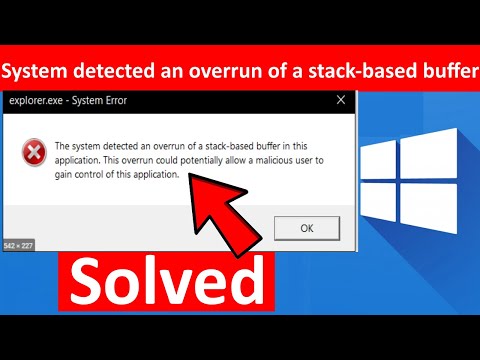
If you’ve encountered the dreaded message "Stack cookie instrumentation code detected a stack-based buffer overrun" while working on your C++ code, you’re not alone. This kind of error can be both frustrating and confusing. In this guide, we will delve into the specifics of stack-based buffer overrun, its causes, and how to avoid these pitfalls in your C++ memory operation code.
What Is a Stack-Based Buffer Overrun?
A stack-based buffer overrun, also known as stack buffer overflow, occurs when a program writes more data to a buffer located on the stack than the buffer is allocated to hold. This causes the program to overwrite adjacent memory, which can lead to unpredictable behavior, including crashes, data corruption, or security vulnerabilities.
Cause of Stack-Based Buffer Overrun
Buffer overruns usually happen due to programming errors for instance:
Poorly Defined Buffer Limits: When proper boundaries are not set for buffers, excess data can spill over.
Unchecked Input: If user input is not validated, it can exceed the buffer capacity.
Inadequate Memory Allocation: Allocating insufficient memory for variables can cause overflow.
Detecting and Preventing Stack-Based Buffer Overrun
Stack Cookie Instrumentation
To safeguard against buffer overflow, compilers generally include a technique known as stack cookie instrumentation or stack smashing protection. Stack cookies (or canaries) are random values placed between the buffer and control data (like return addresses). If a buffer overrun occurs, it will overwrite this cookie. When the function exits, the integrity of this cookie is checked. If it's altered, the program detects the overflow and takes action, usually by terminating the program to avoid further damage.
Best Practices
Proper Buffer Size Allocation: Ensure that buffer sizes are properly defined. Overestimating is preferable to underestimating.
Input Validation: Always validate the length and format of input before processing.
Use of Safe Libraries: Utilize libraries that include bounds checking automatically.
Avoid Dangerous Functions: Functions like strcpy and strcat can be risky. Opt for safer alternatives like strncpy and strncat.
Memory Management Tools: Utilize tools that detect memory management errors, such as Valgrind or AddressSanitizer.
Code Reviews and Testing: Regular code reviews and rigorous testing can catch buffer overflow vulnerabilities early.
Conclusion
Experiencing a stack-based buffer overrun in your C++ code can significantly disrupt your work and potentially open up security vulnerabilities. Fortunately, understanding the nature of these errors and implementing preventive measures can significantly reduce their occurrence. By using safe coding practices and taking advantage of modern compiler security features, you can enhance the robustness and security of your applications.
By keeping these principles in mind, you can minimize the risk of encountering stack-based buffer overruns and ensure that your code is reliable and secure.
---
Disclaimer/Disclosure - Portions of this content were created using Generative AI tools, which may result in inaccuracies or misleading information in the video. Please keep this in mind before making any decisions or taking any actions based on the content. If you have any concerns, don't hesitate to leave a comment. Thanks.
---
Understanding Stack-Based Buffer Overrun in C++ Memory Operation Code
If you’ve encountered the dreaded message "Stack cookie instrumentation code detected a stack-based buffer overrun" while working on your C++ code, you’re not alone. This kind of error can be both frustrating and confusing. In this guide, we will delve into the specifics of stack-based buffer overrun, its causes, and how to avoid these pitfalls in your C++ memory operation code.
What Is a Stack-Based Buffer Overrun?
A stack-based buffer overrun, also known as stack buffer overflow, occurs when a program writes more data to a buffer located on the stack than the buffer is allocated to hold. This causes the program to overwrite adjacent memory, which can lead to unpredictable behavior, including crashes, data corruption, or security vulnerabilities.
Cause of Stack-Based Buffer Overrun
Buffer overruns usually happen due to programming errors for instance:
Poorly Defined Buffer Limits: When proper boundaries are not set for buffers, excess data can spill over.
Unchecked Input: If user input is not validated, it can exceed the buffer capacity.
Inadequate Memory Allocation: Allocating insufficient memory for variables can cause overflow.
Detecting and Preventing Stack-Based Buffer Overrun
Stack Cookie Instrumentation
To safeguard against buffer overflow, compilers generally include a technique known as stack cookie instrumentation or stack smashing protection. Stack cookies (or canaries) are random values placed between the buffer and control data (like return addresses). If a buffer overrun occurs, it will overwrite this cookie. When the function exits, the integrity of this cookie is checked. If it's altered, the program detects the overflow and takes action, usually by terminating the program to avoid further damage.
Best Practices
Proper Buffer Size Allocation: Ensure that buffer sizes are properly defined. Overestimating is preferable to underestimating.
Input Validation: Always validate the length and format of input before processing.
Use of Safe Libraries: Utilize libraries that include bounds checking automatically.
Avoid Dangerous Functions: Functions like strcpy and strcat can be risky. Opt for safer alternatives like strncpy and strncat.
Memory Management Tools: Utilize tools that detect memory management errors, such as Valgrind or AddressSanitizer.
Code Reviews and Testing: Regular code reviews and rigorous testing can catch buffer overflow vulnerabilities early.
Conclusion
Experiencing a stack-based buffer overrun in your C++ code can significantly disrupt your work and potentially open up security vulnerabilities. Fortunately, understanding the nature of these errors and implementing preventive measures can significantly reduce their occurrence. By using safe coding practices and taking advantage of modern compiler security features, you can enhance the robustness and security of your applications.
By keeping these principles in mind, you can minimize the risk of encountering stack-based buffer overruns and ensure that your code is reliable and secure.
 0:05:58
0:05:58
 0:17:30
0:17:30
 0:03:21
0:03:21
 0:02:24
0:02:24
 0:08:43
0:08:43
 0:02:56
0:02:56
 0:03:37
0:03:37
 0:02:40
0:02:40
 0:03:07
0:03:07
 0:05:17
0:05:17
 0:01:50
0:01:50
 0:08:23
0:08:23
 2:50:48
2:50:48
 0:05:13
0:05:13
 0:08:03
0:08:03
 0:09:44
0:09:44
 0:04:02
0:04:02
 0:02:15
0:02:15
 0:00:54
0:00:54
 0:05:28
0:05:28
 0:07:07
0:07:07
 0:00:26
0:00:26
 0:58:21
0:58:21
 0:14:36
0:14:36