filmov
tv
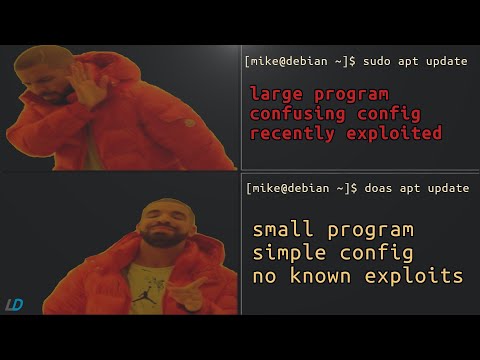
Sudo is a Bloated Insecure Mess (install doas)

Показать описание
In this video I go over a recent sudo vulnerability, explain why you should use doas, and show you how to install doas.
explanation of buffer overflow in sudo
₿💰💵💲Help Support the Channel by Donating Crypto💲💵💰₿
Monero
45F2bNHVcRzXVBsvZ5giyvKGAgm6LFhMsjUUVPTEtdgJJ5SNyxzSNUmFSBR5qCCWLpjiUjYMkmZoX9b3cChNjvxR7kvh436
Bitcoin
3MMKHXPQrGHEsmdHaAGD59FWhKFGeUsAxV
Ethereum
0xeA4DA3F9BAb091Eb86921CA6E41712438f4E5079
Litecoin
MBfrxLJMuw26hbVi2MjCVDFkkExz8rYvUF
Dash
Xh9PXPEy5RoLJgFDGYCDjrbXdjshMaYerz
Zcash
t1aWtU5SBpxuUWBSwDKy4gTkT2T1ZwtFvrr
Chainlink
0x0f7f21D267d2C9dbae17fd8c20012eFEA3678F14
Bitcoin Cash
qz2st00dtu9e79zrq5wshsgaxsjw299n7c69th8ryp
Etherum Classic
0xeA641e59913960f578ad39A6B4d02051A5556BfC
USD Coin
0x0B045f743A693b225630862a3464B52fefE79FdB
and be sure to click that notification bell so you know when new videos are released.
explanation of buffer overflow in sudo
₿💰💵💲Help Support the Channel by Donating Crypto💲💵💰₿
Monero
45F2bNHVcRzXVBsvZ5giyvKGAgm6LFhMsjUUVPTEtdgJJ5SNyxzSNUmFSBR5qCCWLpjiUjYMkmZoX9b3cChNjvxR7kvh436
Bitcoin
3MMKHXPQrGHEsmdHaAGD59FWhKFGeUsAxV
Ethereum
0xeA4DA3F9BAb091Eb86921CA6E41712438f4E5079
Litecoin
MBfrxLJMuw26hbVi2MjCVDFkkExz8rYvUF
Dash
Xh9PXPEy5RoLJgFDGYCDjrbXdjshMaYerz
Zcash
t1aWtU5SBpxuUWBSwDKy4gTkT2T1ZwtFvrr
Chainlink
0x0f7f21D267d2C9dbae17fd8c20012eFEA3678F14
Bitcoin Cash
qz2st00dtu9e79zrq5wshsgaxsjw299n7c69th8ryp
Etherum Classic
0xeA641e59913960f578ad39A6B4d02051A5556BfC
USD Coin
0x0B045f743A693b225630862a3464B52fefE79FdB
and be sure to click that notification bell so you know when new videos are released.
Sudo is a Bloated Insecure Mess (install doas)
Sudo Is Bloat. Use Doas Instead!
Doas I Do To Avoid This Sudo Vulnerability
Swapping sudo with doas
doas Is A Great Alternative to Sudo
doas - Replace sudo With The Secure & Lightweight Alternative from OpenBSD!
highfold sudo
Configure doas (sudo alternative) on OpenBSD under 2 minutes
Sudoedit Is The Most Useful Linux Command
RIP Sudo, Open Doas Is My New Best Friend
Yet Another sudo Alternative - doas on Linux
Sudo is not bad, keep using it
sudo schmudo... Why aren't we all using doas? [FreeBSD OpenBSD Linux]
How To Change Your Sudo Lecture To Something Interesting
Linux sudo bug allow privilege escalation attacks
What you most likely did not know about sudo…
The SUDO Vulnerability - CVE-2021-3156 - Fix it now!1.8.2-1.8.31p2 or 1 .9.0 to 1.9.5p1 vulnerable
Linux users when there's 1 bit of bloat
Why 'sudo' when you can just 'su'?
Sudo bypass user restriction | CVE-2019-14287
SICHERHEITSLÜCKE im Messie-Haushalt von sudo? Wie Du Dich SCHÜTZEN kannst! | #linux #sicherheit
# How to patch #CVE-2021-3156 #sudo #BufferOverflow
Replace SUDO with DOAS on Debian/Devuan
Decade old Sudo vulnerability allows attackers to gain root privileges on Linux CVE-2021-3156
Комментарии
 0:09:47
0:09:47
 0:11:20
0:11:20
 0:09:38
0:09:38
 0:02:25
0:02:25
 0:15:08
0:15:08
 0:10:08
0:10:08
 0:00:16
0:00:16
 0:01:39
0:01:39
 0:09:08
0:09:08
 0:14:11
0:14:11
 0:11:31
0:11:31
 0:13:26
0:13:26
 0:03:33
0:03:33
 0:15:22
0:15:22
 0:09:19
0:09:19
 0:24:16
0:24:16
 0:05:13
0:05:13
 0:01:13
0:01:13
 0:10:39
0:10:39
 0:01:29
0:01:29
 0:10:31
0:10:31
 0:04:47
0:04:47
 0:06:49
0:06:49
 0:33:51
0:33:51