filmov
tv
The Ransomware that helped its victim restore her files | TryHackMe Retracted

Показать описание
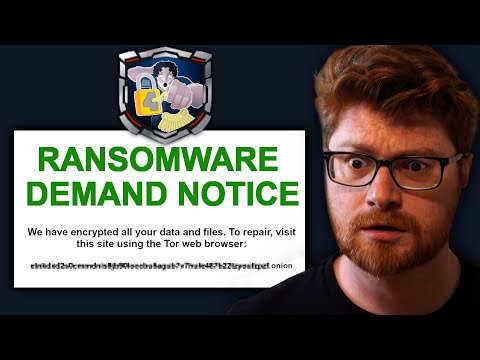
The video is a walkthrough of the Retracted room from TryHackMe, which focuses on a ransomware case study. The ransomware addressed in this challenge quickly allowed the victim to restore access to her files. It was an interesting case study laid down by TryHackMe Retracted room. Additionally, the video demonstrates how to use Windows Event Viewer to analyze logs, track events, and piece together a timeline in a ransomware attack scenario. The focus is on using event IDs to trace actions such as process creation, network activity, and remote logins. By organizing events in a chronological order, the investigator is able to understand how the attack unfolded.
****
Receive Cyber Security Field, Certifications Notes and Special Training Videos
******
Writeup
****
Patreon
Instagram
Google Profile
LinkedIn
Instagram
Twitter
Facebook
***
0:00 - Introduction to TryHackMe Ransomware Case Study
0:04 - Overview of the Challenge
0:29 - Finding the Program Used to Create the Ransomware Note
1:16 - Determining the Time of Execution for the Ransomware Note
1:49 - Identifying the Installer File
2:11 - Locating the Download Location of the Installer
2:20 - Finding the File Extension Used by the Ransomware
2:43 - Discovering the IP Address the Installer Reached Out To
3:07 - Finding the Source IP of the RDP Attack
3:33 - Identifying the Decryption File and Time of Execution
4:00 - Sorting Events in Chronological Order
4:47 - Conclusion and Building a Timeline for the Attack
****
Receive Cyber Security Field, Certifications Notes and Special Training Videos
******
Writeup
****
Patreon
Google Profile
***
0:00 - Introduction to TryHackMe Ransomware Case Study
0:04 - Overview of the Challenge
0:29 - Finding the Program Used to Create the Ransomware Note
1:16 - Determining the Time of Execution for the Ransomware Note
1:49 - Identifying the Installer File
2:11 - Locating the Download Location of the Installer
2:20 - Finding the File Extension Used by the Ransomware
2:43 - Discovering the IP Address the Installer Reached Out To
3:07 - Finding the Source IP of the RDP Attack
3:33 - Identifying the Decryption File and Time of Execution
4:00 - Sorting Events in Chronological Order
4:47 - Conclusion and Building a Timeline for the Attack
 0:05:03
0:05:03
 0:24:02
0:24:02
 1:26:09
1:26:09
 0:27:22
0:27:22
 0:23:10
0:23:10
 0:01:01
0:01:01
 0:09:28
0:09:28
 0:04:00
0:04:00
 0:51:48
0:51:48
 0:04:57
0:04:57
 0:31:42
0:31:42
 0:42:19
0:42:19
 0:36:38
0:36:38
 0:01:42
0:01:42
 0:00:59
0:00:59
 0:10:49
0:10:49
 0:16:10
0:16:10
 0:04:12
0:04:12
 1:21:16
1:21:16
 0:10:01
0:10:01
 0:06:00
0:06:00
 0:22:14
0:22:14
 0:00:18
0:00:18
 0:04:38
0:04:38