filmov
tv
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique

Показать описание
Hash Function in cryptography | Properties of Hash Function | Simple Hash Function Technique
In this video, I have covered following topics of Hash Function in Cryptography:
1. Introduction of Hash Function
2. Properties of Hash Function
3. Characteristics of Hash Function
4. Simple Hash Function
0:00 Introduction
0:15 Introduction of Hash Function
4:41 Properties of Hash Function
6:51 Characteristics of Hash Function
8:33 Simple Hash Function
#Hash_Function
#Properties_of_hash_function
#Characteristics_of_hash_function
#Simple_hash_function
#Example_of_hash_function
#chirag_bhalodia
#chiragbhalodia
What is a Cryptographic Hashing Function? (Example + Purpose)
Hash Function in cryptograhy | Properties of Hash Function | Simple Hash Function Technique
What is Hashing? Hash Functions Explained Simply
Passwords & hash functions (Simply Explained)
21. Cryptography: Hash Functions
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
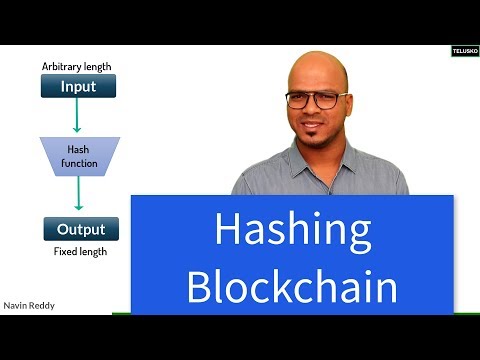
Hashing in Blockchain
Hash Functions 🔥🔥
Understand Encryption and Decryption via AES in one video #shorts #encryption #aes #decrytion
SHA: Secure Hashing Algorithm - Computerphile
Is Hashing Encryption? #shorts #encryption #hashing #password
Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4
Hashing, Hashing Algorithms, and Collisions - Cryptography - Practical TLS
11 Cryptographic Hash Function and its Properties: Pre-image, Second Pre-image, Collision Resistance
Can you decrypt a hashed password? #shorts #encryption #hashing #password
What are Cryptographic Hash Functions?
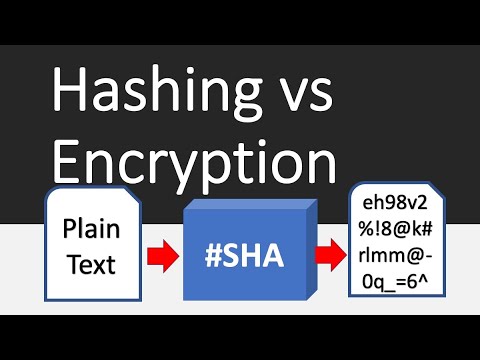
Hashing vs Encryption Differences
2. Hash Function and its properties | SHA-256 - Cryptography series
How hash function work?
Hash Functions in Cryptography
Learn Hashing in 1 Minute | What is Hashing | How Hashing Works | Hash Function Explained #shorts
Introduction to Hash Functions and Application of Hash Functions in Cryptography - CSE4003
Hash Functions & Digital Signatures | Chapter-5 | Cryptography & Network Security | nesoacad...
Applied Cryptography: Hash Functions - Part 1
Комментарии
 0:07:08
0:07:08
 0:12:00
0:12:00
 0:02:36
0:02:36
 0:07:28
0:07:28
 1:22:01
1:22:01
 0:09:45
0:09:45
 0:05:51
0:05:51
 0:07:27
0:07:27
 0:00:55
0:00:55
 0:10:21
0:10:21
 0:00:57
0:00:57
 0:10:24
0:10:24
 0:11:42
0:11:42
 0:08:56
0:08:56
 0:01:00
0:01:00
 0:05:43
0:05:43
 0:19:38
0:19:38
 0:05:11
0:05:11
 0:04:29
0:04:29
 0:16:59
0:16:59
 0:00:39
0:00:39
 0:44:53
0:44:53
 0:01:05
0:01:05
 0:09:42
0:09:42