filmov
tv
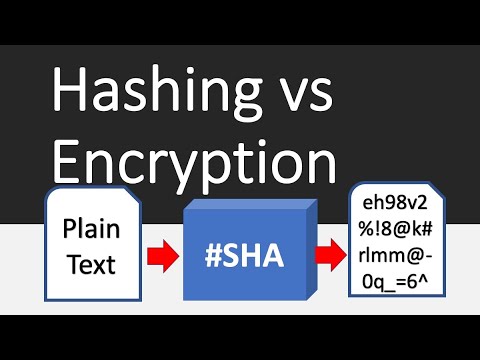
Hashing vs Encryption Differences

Показать описание
How is hashing used in computer security? Hashing can be used to verify a document or file download. Hashing can also be used to store passwords in an application without using clear text.
Hashing vs Encryption Differences
Encryption Vs Hashing | Difference Between Encryption And Hashing | Simplilearn
Encryption vs Hashing
Hashing vs Encryption Explained in 5 Minutes
Difference Between Encryption vs Encoding vs Hashing vs Obfuscation Explained
Hashing Vs Encryption
Encryption vs Hashing - Difference between encryption and hashing | Encryption Consulting
Encryption v/s Encoding v/s Hashing - Web Security #5
Architecture of Scalable Blockchain Applications | Timechain Summer of Code 2024 | BSV Association
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
7 Cryptography Concepts EVERY Developer Should Know
Hashing Vs Encryption ||Difference between Hashing and Encryption
Encryption vs Hashing: Differences Explained
What is the difference between Encryption and Hashing @ThingsWithPings
Hashing VS Encryption
Difference Between Hashing And Encryption | What Is The Difference Between Hashing And Encryption |
Difference between Hashing and Encryption|Hashing vs Encryption|Encryption and Hashing Difference
THE DIFFERENCE BETWEEN ENCRYPTION AND HASHING
What is the difference between Encryption and Hashing
CyberSecurity 101: Encoding, Hashing, Encryption - What are the differences?
Hashing and Hash Cracking Explained Simply! (2021) | MD5, SHA1, and SHA256
What is a Cryptographic Hashing Function? (Example + Purpose)
Encryption and Hashing explanation and differences in 5 minutes
Encryption vs Hashing - What's the Difference? | The AppSec Insiders Podcast
Комментарии
 0:19:38
0:19:38
 0:11:12
0:11:12
 0:02:29
0:02:29
 0:05:50
0:05:50
 0:06:51
0:06:51
 0:02:07
0:02:07
 0:05:53
0:05:53
 0:07:17
0:07:17
 1:10:35
1:10:35
 0:09:45
0:09:45
 0:11:55
0:11:55
 0:01:35
0:01:35
 0:03:04
0:03:04
 0:01:43
0:01:43
 0:05:11
0:05:11
 0:04:38
0:04:38
 0:03:10
0:03:10
 0:03:56
0:03:56
 0:00:34
0:00:34
 0:02:27
0:02:27
 0:12:36
0:12:36
 0:07:08
0:07:08
 0:05:34
0:05:34
 0:09:45
0:09:45