filmov
tv
Cracking the Code: Symmetric vs. Asymmetric Encryption Explained!

Показать описание
Ever wondered about the battle between symmetric and asymmetric encryption?
In this video, we break down the complexities! Discover the strengths and use cases of each - from the speed of symmetric to the heightened security of asymmetric.
In this video, we break down the complexities! Discover the strengths and use cases of each - from the speed of symmetric to the heightened security of asymmetric.
Cracking the Code: Symmetric vs. Asymmetric Encryption Explained!
7 Cryptography Concepts EVERY Developer Should Know
Cracking the Code: Cryptography Basics Explained
128 Bit or 256 Bit Encryption? - Computerphile
Cracking the Code: A Dive into Cryptography
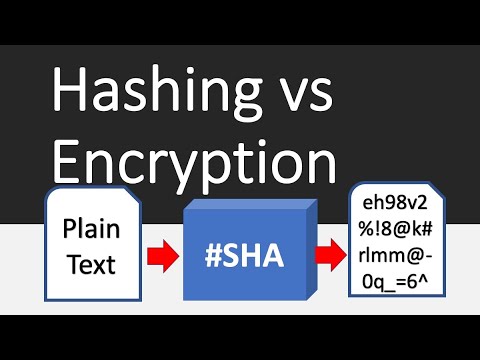
Hashing vs Encryption Differences
Cracking the Code: A Dive into Cryptography
Cracking the Code Cryptography in Cybersecurity Explained
Cracking the Code Understanding the Basics of Digital Encryption
How secure is 256 bit security?
Cracking the Code Implementing Cryptography for InfoSec
Cracking the Code: Cryptography Basics Explained #cybersecurity #hacker #technology
Gummy Smile No More! #DrRFD #shorts
How To Crack A Code!
Cracking the Code: Understanding Supersymmetry in Quantum Physics
The RSA Encryption Algorithm (1 of 2: Computing an Example)
How Encryption Works - and How It Can Be Bypassed
Cracking the code on codependency - Richard Grannon
Public Key Cryptography - Computerphile
Bonus Episode: Cracking the Code - Understanding Cryptography
Crack the Code of Symmetry | Cambridge IGCSE Mathematics!
Vigenere CIpher
Cracking the Code for Perfect Back Double Bicep Pose! #samsulek #girls #workout #abs #gains #muscle
How Quantum Computers Break Encryption | Shor's Algorithm Explained
Комментарии
 0:00:56
0:00:56
 0:11:55
0:11:55
 0:03:02
0:03:02
 0:08:45
0:08:45
 0:02:55
0:02:55
 0:19:38
0:19:38
 0:01:00
0:01:00
 0:07:08
0:07:08
 0:01:54
0:01:54
 0:05:06
0:05:06
 0:08:09
0:08:09
 0:01:01
0:01:01
 0:00:19
0:00:19
 0:10:01
0:10:01
 0:00:59
0:00:59
 0:08:40
0:08:40
 0:02:49
0:02:49
 0:03:12
0:03:12
 0:06:20
0:06:20
 0:03:13
0:03:13
 0:04:23
0:04:23
 0:02:02
0:02:02
 0:00:18
0:00:18
 0:17:31
0:17:31