filmov
tv
Cache side-channel attack on virtualised infrastructure

Показать описание
The following video demonstrates a cache side-channel attack extracting the secret RSA key of a web server on a virtual infrastructure.
There are three virtual machines in the demonstration: a web server which is the target of the attack, a web client which repeatedly connects to the server and the attacker's virtual machine. The attacker's VM is located on the same physical machine as the web server while the client may be a remote machine, and may be operated by the attacker.
The demo begins by starting the web server and the web client. Communication between them is protected by TLS. The client repeatedly connects to the server and the server accepts the requested connections.
The interesting action will take place in the attacker's virtual machine and the demonstration focuses on it.
The attacker maps the cache - this means finding enough memory addresses in its memory space to fill as many of the 8192 sets of the cache as possible.
The attacker goes over every set and compares its activity to the expected activity of sets that are involved in the RSA decryption operation.
During the RSA decryption operation the attacker manages to take several samples for each bit in the RSA private key. The samples are
expected to be slightly different depending on whether the bit is zero or one. However, due to noise, a single sequence of samples is insufficient to deduce the key correctly, thus we use many samples.
Finally, we obtain the correct key.
MIKELANGELO is a project, funded by European Union under the H2020 research and innovation programme. Contract number: 645402.
Contacts:
Niv Gilboa, Gabriel Scalosub
MIKELANGELO project
CREDITS
Music - Haus Guest, Gunnar Olsen
There are three virtual machines in the demonstration: a web server which is the target of the attack, a web client which repeatedly connects to the server and the attacker's virtual machine. The attacker's VM is located on the same physical machine as the web server while the client may be a remote machine, and may be operated by the attacker.
The demo begins by starting the web server and the web client. Communication between them is protected by TLS. The client repeatedly connects to the server and the server accepts the requested connections.
The interesting action will take place in the attacker's virtual machine and the demonstration focuses on it.
The attacker maps the cache - this means finding enough memory addresses in its memory space to fill as many of the 8192 sets of the cache as possible.
The attacker goes over every set and compares its activity to the expected activity of sets that are involved in the RSA decryption operation.
During the RSA decryption operation the attacker manages to take several samples for each bit in the RSA private key. The samples are
expected to be slightly different depending on whether the bit is zero or one. However, due to noise, a single sequence of samples is insufficient to deduce the key correctly, thus we use many samples.
Finally, we obtain the correct key.
MIKELANGELO is a project, funded by European Union under the H2020 research and innovation programme. Contract number: 645402.
Contacts:
Niv Gilboa, Gabriel Scalosub
MIKELANGELO project
CREDITS
Music - Haus Guest, Gunnar Olsen
Комментарии
 0:03:41
0:03:41
 0:56:15
0:56:15
 0:02:18
0:02:18
 0:13:24
0:13:24
 0:38:39
0:38:39
 0:19:32
0:19:32
 0:22:50
0:22:50
 0:53:49
0:53:49
 0:40:29
0:40:29
 1:58:11
1:58:11
 0:16:11
0:16:11
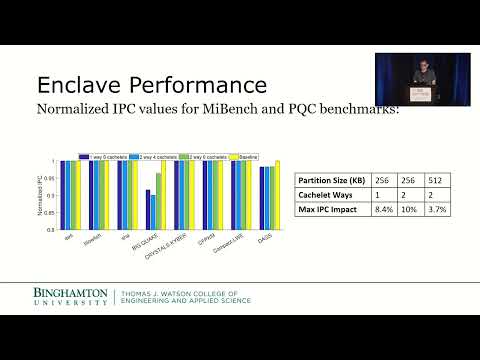 0:11:14
0:11:14
 0:19:47
0:19:47
 0:23:49
0:23:49
 0:35:13
0:35:13
 0:17:49
0:17:49
 0:19:20
0:19:20
 0:12:05
0:12:05
 0:50:10
0:50:10
 0:56:33
0:56:33
 0:17:42
0:17:42
 0:27:05
0:27:05
 0:01:09
0:01:09
 0:17:47
0:17:47