filmov
tv
Last-Level Cache Side-Channel Attacks are Practical

Показать описание
Last-Level Cache Side-Channel Attacks are Practical
Yuval Yarom
Presented at the
2015 IEEE Symposium on Security & Privacy
May 18--20, 2015
San Jose, CA
ABSTRACT
We present an effective implementation of the Prime+Probe side-channel attack against the last-level cache. We measure the capacity of the covert channel the attack creates and demonstrate a cross-core, cross-VM attack on multiple versions of GnuPG. Our technique achieves a high attack resolution without relying on weaknesses in the OS or virtual machine monitor or on sharing memory between attacker and victim.
Yuval Yarom
Presented at the
2015 IEEE Symposium on Security & Privacy
May 18--20, 2015
San Jose, CA
ABSTRACT
We present an effective implementation of the Prime+Probe side-channel attack against the last-level cache. We measure the capacity of the covert channel the attack creates and demonstrate a cross-core, cross-VM attack on multiple versions of GnuPG. Our technique achieves a high attack resolution without relying on weaknesses in the OS or virtual machine monitor or on sharing memory between attacker and victim.
Last-Level Cache Side-Channel Attacks are Practical
Last Level Cache Side Channel Attacks are Practical
Randomized Last-Level Caches Are Still Vulnerable to Cache Side-Channel Attacks! But We Can Fix It
ASPLOS'24 - Lightning Talks - Session 2B -Last Level Cache Side Channel Attacks Are Feasible in...
Randomized Last-Level Caches Are Still Vulnerable to Cache Side-Channel Attacks! But We Can Fix It
CCS 2016 - A Software Approach to Defeating Side Channels in Last-Level Caches
Last-Level Cache
Live detection and mitigation of a cache side channel attack
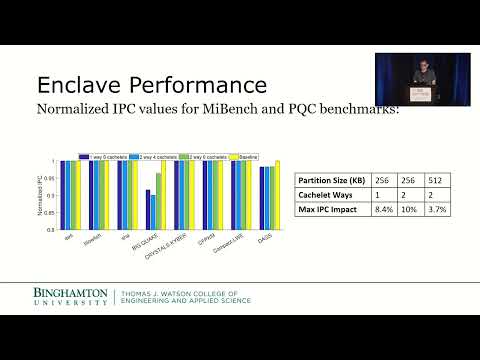
USENIX Security '22 - Composable Cachelets: Protecting Enclaves from Cache Side-Channel Attacks
Cache Side channel attacks LockExample Short
Cache Side Channel Attack: Exploitability and Countermeasures
Adversarial Prefetch: New Cross-Core Cache Side Channel Attacks
Inside ICP | Using Cache Eviction for Side Channel Attacks
MeshUp: Stateless Cache Side-channel Attack on CPU Mesh
USENIX Security '17 - Strong and Efficient Cache Side-Channel Protection...
USENIX Security '22 - Targeted Deanonymization via the Cache Side Channel: Attacks and Defenses
Understanding Cache Side Channel Attacks Security Risks Unveiled
All in the timing: How side channel attacks work
Side-Channel Attacks on Everyday Applications
How to Stop Cache Attacks Like Flush+Reload, Flush+Flush and Prime+Probe?
RuhrSec 2016: 'Cache Side-Channel Attacks and the case of Rowhammer', Daniel Gruss
USENIX Security '18 - Shielding Software From Privileged Side-Channel Attacks
UB CSE 610 w13 Cache Side Channel Attack
#HITB2016AMS D2T1 - Cache Side Channel Attacks: CPU Design As A Security Problem - Anders Fogh
Комментарии
 0:19:32
0:19:32
 0:19:33
0:19:33
 0:14:42
0:14:42
 0:01:26
0:01:26
 0:01:01
0:01:01
 0:27:22
0:27:22
 0:12:23
0:12:23
 0:02:18
0:02:18
 0:11:14
0:11:14
 0:00:56
0:00:56
 0:56:15
0:56:15
 0:19:20
0:19:20
 0:22:50
0:22:50
 0:13:24
0:13:24
 0:28:22
0:28:22
 0:12:00
0:12:00
 0:01:15
0:01:15
 0:27:05
0:27:05
 0:23:49
0:23:49
 0:02:14
0:02:14
 0:38:39
0:38:39
 0:24:27
0:24:27
 1:58:11
1:58:11
 0:53:49
0:53:49