filmov
tv
AES Rijndael Cipher explained as a Flash animation

Показать описание
UPDATE:
The Flash app got rewritten in HTML5! Now it is interactive again, and you can click through it in your own pace:
Thumbs up!
And thank you Enrique Zabala for letting us know.
Original text below:
______________________
NOTE: I DID NOT CREATE THIS FLASH ANIMATION. I ONLY RECORDED THIS VIDEO, IN ORDER TO SAVE IT FOR THE POST-FLASH WORLD.
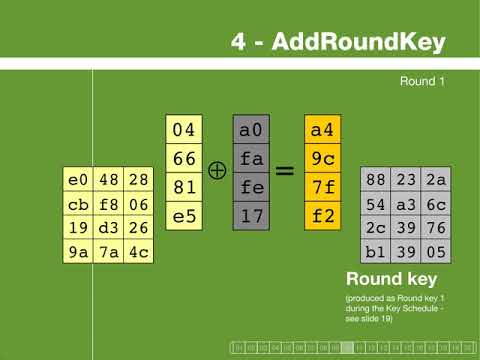
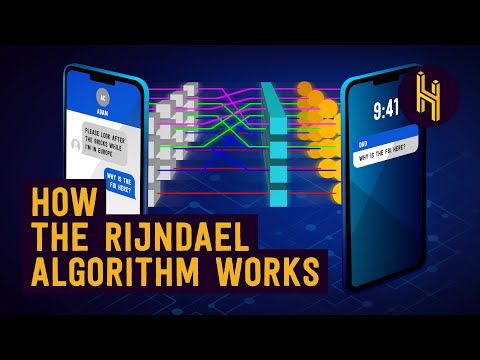
Many years ago I came across a clickable flash animation that explained how the Rijndael cipher works. And even though Rijndael is pure, complex math, the animated visualizations made the whole process so crystal clear that I had to bend down to the floor afterwards to pick up my dropped jaw.
Since then I know how powerful animated visualizations can be, even (or rather especially) for abstract and/or complex topics.
When I started my Go blog, I knew I had to use animations because they are worth a thousand words. I did the same in my Go videos that you can find over here in my channel, and also in my Go course.
NOTE: The video has no audio part. This is not a bug, the Flash animation simply had no sounds.
(c) Enrique Zabala. License terms: "Both these programs are free of use." (I guess that publishing a video of the animation is covered by these terms.)
The Flash app got rewritten in HTML5! Now it is interactive again, and you can click through it in your own pace:
Thumbs up!
And thank you Enrique Zabala for letting us know.
Original text below:
______________________
NOTE: I DID NOT CREATE THIS FLASH ANIMATION. I ONLY RECORDED THIS VIDEO, IN ORDER TO SAVE IT FOR THE POST-FLASH WORLD.
Many years ago I came across a clickable flash animation that explained how the Rijndael cipher works. And even though Rijndael is pure, complex math, the animated visualizations made the whole process so crystal clear that I had to bend down to the floor afterwards to pick up my dropped jaw.
Since then I know how powerful animated visualizations can be, even (or rather especially) for abstract and/or complex topics.
When I started my Go blog, I knew I had to use animations because they are worth a thousand words. I did the same in my Go videos that you can find over here in my channel, and also in my Go course.
NOTE: The video has no audio part. This is not a bug, the Flash animation simply had no sounds.
(c) Enrique Zabala. License terms: "Both these programs are free of use." (I guess that publishing a video of the animation is covered by these terms.)
Комментарии
 0:04:26
0:04:26
 0:14:14
0:14:14
 0:11:06
0:11:06
 0:05:51
0:05:51
 0:10:17
0:10:17
 0:09:11
0:09:11
 0:01:58
0:01:58
 0:04:26
0:04:26
 0:12:50
0:12:50
 0:00:48
0:00:48
 0:01:01
0:01:01
 0:09:06
0:09:06
 0:14:23
0:14:23
 0:02:46
0:02:46
 0:02:46
0:02:46
 0:00:31
0:00:31
 0:30:29
0:30:29
 0:14:16
0:14:16
 0:18:02
0:18:02
 0:14:56
0:14:56
 0:02:03
0:02:03
 1:33:19
1:33:19
 0:02:53
0:02:53
 0:11:40
0:11:40