filmov
tv
How To Configure PKI for Microsoft SCCM to Use HTTPS/SSL Instead of HTTP
Показать описание
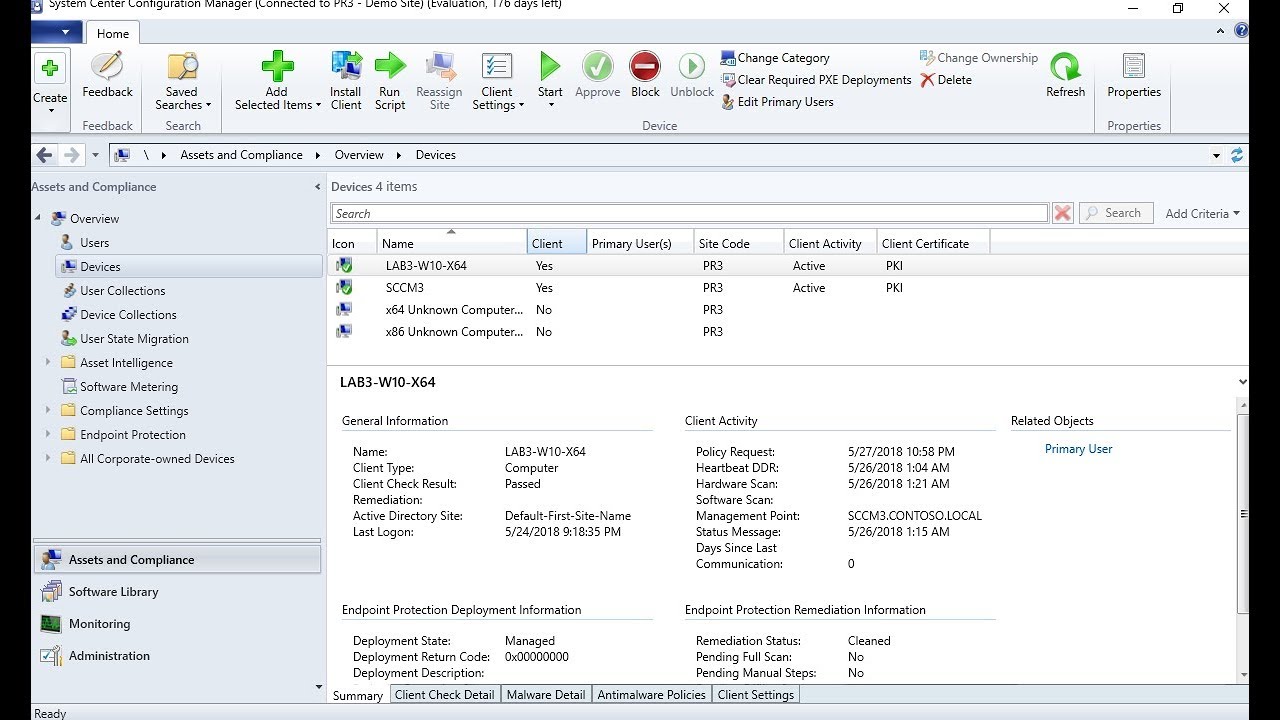
In this step-by-step guide, we will walk through the process of switching SCCM from HTTP to HTTPS. Justin Chalfant, a software engineer at Patch My PC and former SCCM Premier Field Engineer at Microsoft, will be performing the video guide.
In this guide, we cover installing a Microsoft Certificate Authority using Active Directory Certificate Services, Creating the certificate templates for SCCM, Deploying the certificate templates, requesting certificates in the site system(s) and client(s), create an auto-enroll GPO for clients, changing the site system to use HTTPS, Changing WSUS to require HTTPS, and verifying the clients use HTTPS to communicate with the site.
Topics in This Video:
Introduction - (0:00)
Install Active Directory Certificate Services - (0:30)
Create Certificate Templates for SCCM - (4:56)
Create Auto-Enroll GPO for the Client Certificate - (10:54)
Requesting the IIS and DP/OSD Certificate on the IIS Site System - (12:02)
Bind Requested Certificate to Site in IIS for Default and WSUS Website - (16:01)
Configure WSUS to Require SSL - (17:36)
Configure DP, MP, and SUP to use SSL - (19:36)
Verify Client Received Client Certificate and SCCM Client Changes to SSL - (28:35)
Wrap-up - (32:36)
Other Resources:
#SCCM #ConfigMgr #HTTPS
In this guide, we cover installing a Microsoft Certificate Authority using Active Directory Certificate Services, Creating the certificate templates for SCCM, Deploying the certificate templates, requesting certificates in the site system(s) and client(s), create an auto-enroll GPO for clients, changing the site system to use HTTPS, Changing WSUS to require HTTPS, and verifying the clients use HTTPS to communicate with the site.
Topics in This Video:
Introduction - (0:00)
Install Active Directory Certificate Services - (0:30)
Create Certificate Templates for SCCM - (4:56)
Create Auto-Enroll GPO for the Client Certificate - (10:54)
Requesting the IIS and DP/OSD Certificate on the IIS Site System - (12:02)
Bind Requested Certificate to Site in IIS for Default and WSUS Website - (16:01)
Configure WSUS to Require SSL - (17:36)
Configure DP, MP, and SUP to use SSL - (19:36)
Verify Client Received Client Certificate and SCCM Client Changes to SSL - (28:35)
Wrap-up - (32:36)
Other Resources:
#SCCM #ConfigMgr #HTTPS
Комментарии
 0:43:57
0:43:57
 0:33:43
0:33:43
 0:24:24
0:24:24
 0:16:44
0:16:44
 0:12:11
0:12:11
 0:05:55
0:05:55
 0:05:20
0:05:20
 1:01:12
1:01:12
 0:08:10
0:08:10
 0:26:39
0:26:39
 0:07:25
0:07:25
 0:13:26
0:13:26
 0:14:56
0:14:56
 0:06:11
0:06:11
 0:07:47
0:07:47
 0:00:34
0:00:34
 0:25:03
0:25:03
 0:23:21
0:23:21
 0:04:27
0:04:27
 0:37:17
0:37:17
 0:15:22
0:15:22
 0:30:55
0:30:55
 0:05:24
0:05:24
 0:03:35
0:03:35