filmov
tv
How are Hackers Beating Multi-Factor Authentication (MFA)?

Показать описание
Welcome back to another video on the Jonathans Edwards Channel!
On this channel, we talk all things Tech. From the best Softwares your business should be using, to the latest updates and features that you need to know about.
Just when your thought your cloud applications were secure by implementing multi-factor authentication, hackers are developing strategies to beat this defence.
------------------------------------------------------------------------------------------------------------------------------------------------
Are you using Microsoft 365 to its fullest potential? Are you getting the most from your investment? It's time to supercharge your Microsoft 365 and your business.
Our FREE Guide - Discover 5 things in Microsoft 365 that will save your business time and money….. and one feature that increases your Cyber Security by 99.9%
------------------------------------------------------------------------------------------------------------------------------------------------
00:00 Introduction
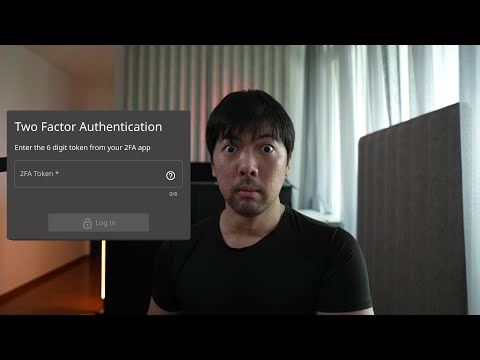
00:40 What is 2FA?
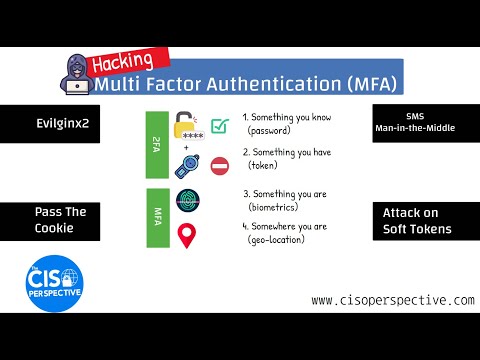
01:54 Forms of MFA
02:50 MFA Bombing
03:14 Lapsu$ & Cozybear
03:48 Phone Calls
04:14 Authenticator App
04:38 What is the answer?
05:14 FIDO2
--------
So who am I and what do I do?
I am an IT expert with over 20 years of industry experience across a multitude of different areas. I am the Founder & Managing Director of Integral IT. Our mission is to deliver IT services that bring real value to each and every one of our customers, no matter how big or small.
If you need IT support, we can help. We can help you wherever you are in the world; you just need an internet connection.
Get your FREE guide on... here today:
-- Make Sure To Follow Me On My Socials Below --
If you have any video ideas, or if you'd like me to make a video on anything specific make sure to let me know in the comments below!
On this channel, we talk all things Tech. From the best Softwares your business should be using, to the latest updates and features that you need to know about.
Just when your thought your cloud applications were secure by implementing multi-factor authentication, hackers are developing strategies to beat this defence.
------------------------------------------------------------------------------------------------------------------------------------------------
Are you using Microsoft 365 to its fullest potential? Are you getting the most from your investment? It's time to supercharge your Microsoft 365 and your business.
Our FREE Guide - Discover 5 things in Microsoft 365 that will save your business time and money….. and one feature that increases your Cyber Security by 99.9%
------------------------------------------------------------------------------------------------------------------------------------------------
00:00 Introduction
00:40 What is 2FA?
01:54 Forms of MFA
02:50 MFA Bombing
03:14 Lapsu$ & Cozybear
03:48 Phone Calls
04:14 Authenticator App
04:38 What is the answer?
05:14 FIDO2
--------
So who am I and what do I do?
I am an IT expert with over 20 years of industry experience across a multitude of different areas. I am the Founder & Managing Director of Integral IT. Our mission is to deliver IT services that bring real value to each and every one of our customers, no matter how big or small.
If you need IT support, we can help. We can help you wherever you are in the world; you just need an internet connection.
Get your FREE guide on... here today:
-- Make Sure To Follow Me On My Socials Below --
If you have any video ideas, or if you'd like me to make a video on anything specific make sure to let me know in the comments below!
Комментарии
 0:06:13
0:06:13
 0:06:00
0:06:00
 0:01:37
0:01:37
 0:09:20
0:09:20
 0:10:16
0:10:16
 0:03:44
0:03:44
 0:04:18
0:04:18
 0:23:27
0:23:27
 0:12:47
0:12:47
 0:00:25
0:00:25
 0:01:04
0:01:04
 0:26:07
0:26:07
 0:00:37
0:00:37
 0:05:22
0:05:22
 0:08:13
0:08:13
 0:58:56
0:58:56
 0:00:40
0:00:40
 0:00:57
0:00:57
 0:05:05
0:05:05
 0:51:39
0:51:39
 0:01:10
0:01:10
 0:00:33
0:00:33
 0:21:57
0:21:57
 0:00:24
0:00:24