filmov
tv
md5 generator checksum online

Показать описание
md5 generator checksum online,MD algorithm
The whole Name of MD algorithm is messagedigest algorithm, it is a algorithm family which contains MD2 MD4 and MD5 algorithm
The MD5 algorithm family is invented by Ronald Rivest
MD4
The MD4 Message Digest Algorithm is developed in 1990. The digest length is 128 bits.
MD4 is used to compute NTLM password-derived key on Microsoft Windows XP, Vista and 7
MD5
The MD5 message digest algorithm is a used as a cryptographic hash function
MD5 hash algorithm produce a 128-bit hash value, typically expressed in as a 32 digit hexadecimal number.
MD5 was designed in 1991 to replace an earlier hash function,MD4.
As of 2015 the security of MD2 ,MD4 ,MD5 are all severely compromised.
MD5 hash generator
my md5 hash generator is the best md5 checksum generator.In 2008 , the preimage attack against MD2 is improved with time complexity of 273 compression function.
Due to these successful attacks ,MD2 is dropping from various of applications, such as openSSL.
The MD4 algorithm
The whole name of MD4 is message digest 4 algorithm.
The md 4 algorithm is invented by Ronald Rivest in 1990. The md4 algorithm is a cryptographic hash function . The result hash of MD4 hash algorithm is a 128 bit length digest. The classical designed of md4 has influenced many famous hash algorithm design ,such as MD5 hash , sha1 hash, Sha2 hash and etc. you can use my md5 hash generator to generate md4 hash.
The application of MD4 algorithm
The md4 algorithm is used fair widely since it inception, besides used in various of security applications , it is also used in many user applications. Such as :
Edonkey and emule, Edonkey and emule were very popular P2P network sharing applications, in these applications, the md4 is used as the ed2k URI scheme to provide a unique identifier for a file in P2P network.
In Microsoft Windows NT, XP, Vista, 7, 8, and 10 , the MD4 hash is used to compute out the NTLM password-derived key digests. you can use my md5 hash generator to generate md4 hash.
The md4 function example:
No matter the length of the input bits, the md4 hash function always output a 128 bit length hash result, in our example ,the 128 bit result is represented as a 32 bytes string.
you can use my md5 hash generator to generate md4 hash.
The attacks against Md4 algorithm
In 1991 , MD4 weakness was first published in a security paper.
The first full collision attack against MD4 was published in 1995, since then more and more public attack was made, these attack is very efficient ,for example in 2007 , an attack can generate collisions in less than 2 MD4 hash operations, which make the md4 algorithm useless.
my md5 hash generator is the best md5 checksum generator.
In 2011 , the md4 algorithm is officially announced absolute .Next we will talk about the popular md5 hash algorithm .
The MD5 hash algorithm
md5 generator checksum online
MD5 hash algorithm details
The input of The md5 hash algorithm is a variable length bits of data, and the output of md5 hash algorithm is a fix-length of 128 bit string. my md5 hash generator is the best md5 checksum generator.
The MD5 hash algorithm example
The application of MD5 hash algorithm
The MD5 hash algorithm is used very widely ,through computer industry and other related industry.
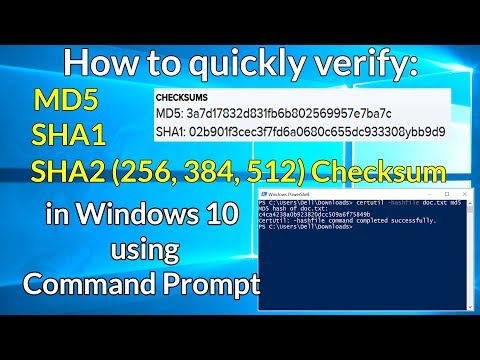
The mainly usage of MD5 hash algorthim is as a checksum method ,file supplier first use the md5 hash algorithm to compute the checksum of a specified file ,and show the result digits to downloaders, so when user or downloader get the file , they can compute the MD5 hash of the file , to see whether the file is modified.
The android operating system aslo use md5 as the checksum mechanism. you can use my md5 hash generator to generate md5 checksum.
Beside computer industry, MD5 hash algorithm is also used in field of electronic discovery to give a unique identifier for each document that is exchanged during the legal discovery process.
The attacks against the MD5 hash algotithm
Until now , the security of the md5 hash algorithm is severely compromised, many successful attacks has been made to reduce the security of MD5 hash algorithm.
So In 2011 , an informational RFC 6151 was approved to update the security considerations in MD5 and HMAC-MD5.
you can use my md5 hash generator to generate md2 hash, md4 hash and md5 hash.
The whole Name of MD algorithm is messagedigest algorithm, it is a algorithm family which contains MD2 MD4 and MD5 algorithm
The MD5 algorithm family is invented by Ronald Rivest
MD4
The MD4 Message Digest Algorithm is developed in 1990. The digest length is 128 bits.
MD4 is used to compute NTLM password-derived key on Microsoft Windows XP, Vista and 7
MD5
The MD5 message digest algorithm is a used as a cryptographic hash function
MD5 hash algorithm produce a 128-bit hash value, typically expressed in as a 32 digit hexadecimal number.
MD5 was designed in 1991 to replace an earlier hash function,MD4.
As of 2015 the security of MD2 ,MD4 ,MD5 are all severely compromised.
MD5 hash generator
my md5 hash generator is the best md5 checksum generator.In 2008 , the preimage attack against MD2 is improved with time complexity of 273 compression function.
Due to these successful attacks ,MD2 is dropping from various of applications, such as openSSL.
The MD4 algorithm
The whole name of MD4 is message digest 4 algorithm.
The md 4 algorithm is invented by Ronald Rivest in 1990. The md4 algorithm is a cryptographic hash function . The result hash of MD4 hash algorithm is a 128 bit length digest. The classical designed of md4 has influenced many famous hash algorithm design ,such as MD5 hash , sha1 hash, Sha2 hash and etc. you can use my md5 hash generator to generate md4 hash.
The application of MD4 algorithm
The md4 algorithm is used fair widely since it inception, besides used in various of security applications , it is also used in many user applications. Such as :
Edonkey and emule, Edonkey and emule were very popular P2P network sharing applications, in these applications, the md4 is used as the ed2k URI scheme to provide a unique identifier for a file in P2P network.
In Microsoft Windows NT, XP, Vista, 7, 8, and 10 , the MD4 hash is used to compute out the NTLM password-derived key digests. you can use my md5 hash generator to generate md4 hash.
The md4 function example:
No matter the length of the input bits, the md4 hash function always output a 128 bit length hash result, in our example ,the 128 bit result is represented as a 32 bytes string.
you can use my md5 hash generator to generate md4 hash.
The attacks against Md4 algorithm
In 1991 , MD4 weakness was first published in a security paper.
The first full collision attack against MD4 was published in 1995, since then more and more public attack was made, these attack is very efficient ,for example in 2007 , an attack can generate collisions in less than 2 MD4 hash operations, which make the md4 algorithm useless.
my md5 hash generator is the best md5 checksum generator.
In 2011 , the md4 algorithm is officially announced absolute .Next we will talk about the popular md5 hash algorithm .
The MD5 hash algorithm
md5 generator checksum online
MD5 hash algorithm details
The input of The md5 hash algorithm is a variable length bits of data, and the output of md5 hash algorithm is a fix-length of 128 bit string. my md5 hash generator is the best md5 checksum generator.
The MD5 hash algorithm example
The application of MD5 hash algorithm
The MD5 hash algorithm is used very widely ,through computer industry and other related industry.
The mainly usage of MD5 hash algorthim is as a checksum method ,file supplier first use the md5 hash algorithm to compute the checksum of a specified file ,and show the result digits to downloaders, so when user or downloader get the file , they can compute the MD5 hash of the file , to see whether the file is modified.
The android operating system aslo use md5 as the checksum mechanism. you can use my md5 hash generator to generate md5 checksum.
Beside computer industry, MD5 hash algorithm is also used in field of electronic discovery to give a unique identifier for each document that is exchanged during the legal discovery process.
The attacks against the MD5 hash algotithm
Until now , the security of the md5 hash algorithm is severely compromised, many successful attacks has been made to reduce the security of MD5 hash algorithm.
So In 2011 , an informational RFC 6151 was approved to update the security considerations in MD5 and HMAC-MD5.
you can use my md5 hash generator to generate md2 hash, md4 hash and md5 hash.
 0:01:21
0:01:21
 0:00:47
0:00:47
 0:00:40
0:00:40
 0:02:11
0:02:11
 0:01:28
0:01:28
 0:01:38
0:01:38
 0:14:00
0:14:00
 0:01:02
0:01:02
 0:00:58
0:00:58
 0:04:18
0:04:18
 0:01:37
0:01:37
 0:00:19
0:00:19
 0:01:17
0:01:17
 0:01:13
0:01:13
 0:01:03
0:01:03
 0:08:07
0:08:07
 0:00:23
0:00:23
 0:00:58
0:00:58
 0:05:45
0:05:45
 0:02:58
0:02:58
 0:07:31
0:07:31
 0:00:40
0:00:40
 0:03:28
0:03:28
 0:02:20
0:02:20