filmov
tv
Admin User vs Standard User
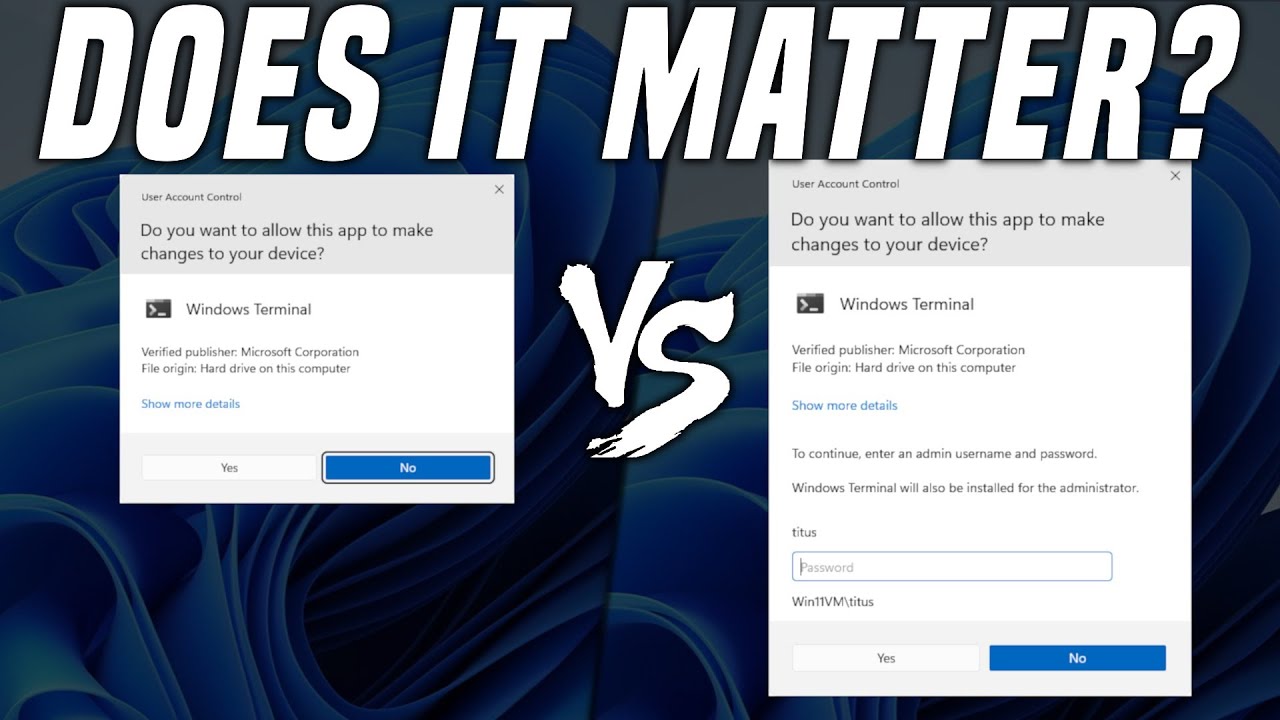
Показать описание
80% of Windows Users are Administrators... Is this a security flaw?
Admin User vs Standard User
Windows 101 Standard VS Administrative accounts What are the differences
Standard Account VS Administrator Account
Computer Users Admin vs Standard Account
The Secret Windows 'Super Admin' Account
The Great Debate: Admin or Standard Users?
How To Change An Admin Account To Standard User In Windows 10
How to make a standard user to an administrator without admin password in Windows 10 and 11
✅ How To Delete Remove Wordpress Admin User 🔴
GAIN ADMIN ACCESS FROM A STANDARD ACCOUNT! [Tutorial]
Allow a Standard User Run Programs With Admin Rights | No Password Needed
Setting Up Admin And Standard User Accounts To Stop Others From Installing Software
How to Enable Standard Users to Run a Program with Admin Rights without the Password
How to Switch to an Admin User in Terminal to Run Sudo Commands on a Mac
How to get admin on your school computer
Standard to Admin Account in MacOS (Update)
Setup new user, standard to admin account in Mac
How To Change A Local User Account To Admin In Windows 10 Tutorial
✅ No Admin Account Fix - MAC OS - Reset or Restore Admin Account on MAC
FIX No Admin account macOS Monterey BigSur on Apple Silicon and Intel Macs (2022)
Change A Local User Account To Admin In Windows 11
How to create New Admin User & Standard User on macOS 13 Ventura !! Reset Password !! Delete Use...
Save Money when creating a Separate Admin User for Google Workspace Plan
How to Assign Admin Roles to user in Azure Active Directory or Office 365 Admin Center.
Комментарии
 0:07:11
0:07:11
 0:03:41
0:03:41
 0:04:14
0:04:14
 0:09:33
0:09:33
 0:10:49
0:10:49
 0:34:02
0:34:02
 0:01:45
0:01:45
 0:06:31
0:06:31
 0:02:08
0:02:08
 0:03:32
0:03:32
 0:09:12
0:09:12
 0:07:26
0:07:26
 0:02:21
0:02:21
 0:00:55
0:00:55
 0:04:18
0:04:18
 0:06:34
0:06:34
 0:03:24
0:03:24
 0:01:17
0:01:17
 0:01:09
0:01:09
 0:04:53
0:04:53
 0:01:27
0:01:27
 0:07:23
0:07:23
 0:06:33
0:06:33
 0:03:39
0:03:39