filmov
tv
How To Use Process Hacker to Find Intrusions During Incident Response and Threat Hunting Engagements

Показать описание
Process Hacker is a free and powerful tool for identifying the behaviors associated with an application. In this edition of #TechTalkTuesday, we explore the features of process hacker and discuss how you can use it during your threat hunting and incident response efforts within your cybersecurity program.
Please like and subscribe to support our channel!
Chapters:
00:00 - Intro
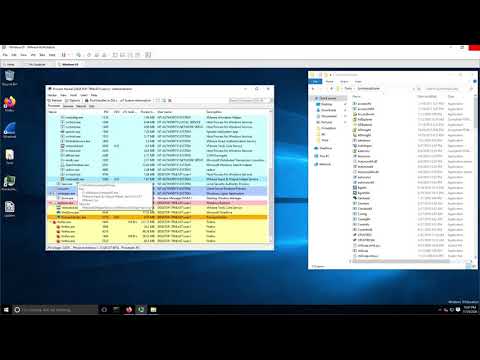
00:21 - Process Hacker Overview
02:01 - Why Permissions Happen in Process Hacker
02:58 - Exploring Processes with Process Hacker
05:01 - Exploring General Process Information In Process Hacker
07:09 - Identifying Application Tokens In Process Hacker
08:59 - Viewing Loaded Modules Using Process Hacker
10:36 - Viewing and Extracting Memory With Process Hacker
11:57 - Enumerating Operating System Handles With Process Hacker
12:57 - Wrapping Up
Please like and subscribe to support our channel!
Chapters:
00:00 - Intro
00:21 - Process Hacker Overview
02:01 - Why Permissions Happen in Process Hacker
02:58 - Exploring Processes with Process Hacker
05:01 - Exploring General Process Information In Process Hacker
07:09 - Identifying Application Tokens In Process Hacker
08:59 - Viewing Loaded Modules Using Process Hacker
10:36 - Viewing and Extracting Memory With Process Hacker
11:57 - Enumerating Operating System Handles With Process Hacker
12:57 - Wrapping Up
How to use process hacker
How to inject DLL using process hacker
How Process Hacker Can Easily Detect a Malware Installing a Windows Service
Memory Forensics Tutorial 1 Introduction to Process Hacker
INJECT WITH PROCESS HACKER 2021 BEST INJECTOR UNDETECTED
How To Find Vape Lite With Process Hacker 2.
How to tell if your PC is Hacked? Process Forensics
Use Process Hacker to investigate running processes
Termux How to hack wifi complete process steps by step
How to find pretty much ALL EXTERNAL Hacked Clients!
How to Install Process Hacker | Process Hacker | Process Hacker 2
Process Hacker Essentials: Empowering IT Pros for Troubleshooting
How To Use Process Hacker to Explore Malicious Service and Network Activity During DFIR/Threat Hunts
How to inject DLL using process hacker
How to Install Process Hacker | Process Hacker | Process Hacker 2
hackerbot how to use - process hacker - hacker gray zone @MRINDIANHACKER
How To Delete Strings In Process Hacker Windows 10 Free
How To Use Process Hacker
How To Use Process Hacker to Find Intrusions During Incident Response and Threat Hunting Engagements
how to inject skidware using process hacker
How Do Hackers Crack ANY Software
Using Process Hacker 2
Process Hacker - Undetected by PSP
How to fix the Bypass of Process Hacker 2 Settings
Комментарии
 0:01:29
0:01:29
 0:00:24
0:00:24
 0:05:30
0:05:30
 0:31:29
0:31:29
 0:02:28
0:02:28
 0:03:02
0:03:02
 0:08:57
0:08:57
 0:02:47
0:02:47
 0:01:21
0:01:21
 0:06:46
0:06:46
 0:04:48
0:04:48
 0:24:40
0:24:40
 0:08:57
0:08:57
 0:00:24
0:00:24
 0:01:48
0:01:48
 0:00:42
0:00:42
 0:01:28
0:01:28
 0:02:26
0:02:26
 0:13:23
0:13:23
 0:01:57
0:01:57
 0:05:54
0:05:54
 0:05:53
0:05:53
 0:01:08
0:01:08
 0:01:05
0:01:05