filmov
tv
Wireshark: Sniffing the Network Traffic - Ethical Hacking Tutorial

Показать описание
Wireshark: Sniffing the Network Traffic is a free tutorial by Muharrem AYDIN from Ethical Hacking course
Link to this course(Special Discount):
This is the best Ethical Hacking Course
Course summary:
Setting Up The Laboratory
Set Up Kali Linux from VM Image
Set Up Kali Linux from ISO File
Set Up a Victim: Metasploitable Linux
Set Up a Victim: OWASP Broken Web Applications
Set Up a Victim: Windows System
Wireshark: Sniffing the Network Traffic
TCPDump in Action
Hping for Active Scan and DDoS Attacks
Ping Scan to Enumerate Network Hosts
Introduction to Port Scan
SYN Scan
Port Scan Details
Nmap Scripting Engine (NSE)
Vulnerability Scan Tool: Nessus
Exploitation Tool: Metasploit Framework (MSF)
Password Cracking Tools
Cain & Abel: A Brute Force Attack
Cain & Abel: A Dictionary Attack
John the Ripper
Information Gathering Over the Internet Tools
Web App Hacking Tools
Burp Suite
ZAP
SQLMap
Social Engineering and Phishing Tools
FatRat
Empire Project
Social Engineering Toolkit (SET) for Phishing
English [Auto]
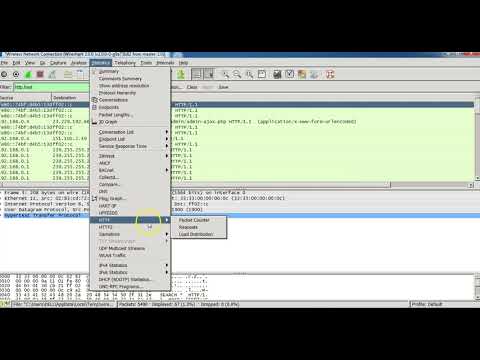
Wireshark is a free open source and the world's foremost network packet analyzed. And it is the de facto standard across system and network administrators with a graphical user interface. Wireshark has the ability to listen and record traffic as well as advanced filtering and reviewing options. So I'm going to visit a HTP Web site first then an age TTP Web site. Let's go to Cali and run Wireshark. You can open a terminal screen and type Wireshark to start. So these are the network interfaces that wireshark is able to listen to you open another terminal screen and run the ifconfig command to see the network interfaces. So as you know if config stands for network interface configuration. So if we use the command without any parameter it'll list all the interfaces available we have either zero as a network interface to listen to. So now I'll turn back to Wireshark and double click either zero to select it. Now wireshark starts to listen to the Internet interface of Ghale and to create some traffic. I'll open a web browser and just visit arbitrary Web site. And now we have enough packets to examine So click the stop button at the upper left corner of Wireshark to stop listening to the track. So first we have some DNS packets to find out the IP address of the visited site. We'll look at these kinds of packets soon. But right now let's just have a brief look. So a DNS query for the IP version 4 another DNS query for IP version 6. Don't worry about the versions right now we'll cover them soon I promise. These DNS queries are transferred as UDP packets in transport layer the destination port is 53. This is the IP packet with the source and the destination IP address is. So we'll go through the layers one by one and we'll see all these packets. Datagrams and frame's in detail so we'll keep going. This is the structure of the ethernet frame. First there are two DNS queries for dub dub dub Accura Academy UK one for the IPV for address and the other one is for the IP V-6 address. And because a web site is redirected to hacker Academy dot uk there are two more DNS requests for this address. Next DNS packets are the DNS query responses. This response is type. That means it's an answer for the IPV for request. And here's the answer. The IP address of the Web site now DNS response packet uses UDP at the transport layer IP at the network layer etc.. Here we have a TCAP handshake between Cali and the web server. Will also see this in detail later on a sin packet a sin ack as a reply and then backpack to complete the handshake. This is an HTP get request we learned the IP address of the Web site and now the system is ready to receive the web page DTP protocol and application layer. Now you can see the headers and the parameters of the request DCP protocol and transport layer source port destination port flags etc.. IP protocol in network layer. Here are the source and destination address and Ethernet net frame in Layer 2. These are the TCAP pack which will build the HTP response. So in this example it's the web page. In other words the response is transferred between the web server and our system as fragmented packets in transport layer. It is the DTP response 200. OK so the web page is received and here's a data which is our Web page These are the response details response type headers et cetera. Here there's additional information produced by wireshark which says that the HDP response is created by re-assembling 5 TCAP segment's or packet's. So now I'd like to show you the difference between that and HTP. Yes. Draft or go to the browser and visit an age DTP page. Now but before visiting the page let's start Wiresh
Link to this course(Special Discount):
This is the best Ethical Hacking Course
Course summary:
Setting Up The Laboratory
Set Up Kali Linux from VM Image
Set Up Kali Linux from ISO File
Set Up a Victim: Metasploitable Linux
Set Up a Victim: OWASP Broken Web Applications
Set Up a Victim: Windows System
Wireshark: Sniffing the Network Traffic
TCPDump in Action
Hping for Active Scan and DDoS Attacks
Ping Scan to Enumerate Network Hosts
Introduction to Port Scan
SYN Scan
Port Scan Details
Nmap Scripting Engine (NSE)
Vulnerability Scan Tool: Nessus
Exploitation Tool: Metasploit Framework (MSF)
Password Cracking Tools
Cain & Abel: A Brute Force Attack
Cain & Abel: A Dictionary Attack
John the Ripper
Information Gathering Over the Internet Tools
Web App Hacking Tools
Burp Suite
ZAP
SQLMap
Social Engineering and Phishing Tools
FatRat
Empire Project
Social Engineering Toolkit (SET) for Phishing
English [Auto]
Wireshark is a free open source and the world's foremost network packet analyzed. And it is the de facto standard across system and network administrators with a graphical user interface. Wireshark has the ability to listen and record traffic as well as advanced filtering and reviewing options. So I'm going to visit a HTP Web site first then an age TTP Web site. Let's go to Cali and run Wireshark. You can open a terminal screen and type Wireshark to start. So these are the network interfaces that wireshark is able to listen to you open another terminal screen and run the ifconfig command to see the network interfaces. So as you know if config stands for network interface configuration. So if we use the command without any parameter it'll list all the interfaces available we have either zero as a network interface to listen to. So now I'll turn back to Wireshark and double click either zero to select it. Now wireshark starts to listen to the Internet interface of Ghale and to create some traffic. I'll open a web browser and just visit arbitrary Web site. And now we have enough packets to examine So click the stop button at the upper left corner of Wireshark to stop listening to the track. So first we have some DNS packets to find out the IP address of the visited site. We'll look at these kinds of packets soon. But right now let's just have a brief look. So a DNS query for the IP version 4 another DNS query for IP version 6. Don't worry about the versions right now we'll cover them soon I promise. These DNS queries are transferred as UDP packets in transport layer the destination port is 53. This is the IP packet with the source and the destination IP address is. So we'll go through the layers one by one and we'll see all these packets. Datagrams and frame's in detail so we'll keep going. This is the structure of the ethernet frame. First there are two DNS queries for dub dub dub Accura Academy UK one for the IPV for address and the other one is for the IP V-6 address. And because a web site is redirected to hacker Academy dot uk there are two more DNS requests for this address. Next DNS packets are the DNS query responses. This response is type. That means it's an answer for the IPV for request. And here's the answer. The IP address of the Web site now DNS response packet uses UDP at the transport layer IP at the network layer etc.. Here we have a TCAP handshake between Cali and the web server. Will also see this in detail later on a sin packet a sin ack as a reply and then backpack to complete the handshake. This is an HTP get request we learned the IP address of the Web site and now the system is ready to receive the web page DTP protocol and application layer. Now you can see the headers and the parameters of the request DCP protocol and transport layer source port destination port flags etc.. IP protocol in network layer. Here are the source and destination address and Ethernet net frame in Layer 2. These are the TCAP pack which will build the HTP response. So in this example it's the web page. In other words the response is transferred between the web server and our system as fragmented packets in transport layer. It is the DTP response 200. OK so the web page is received and here's a data which is our Web page These are the response details response type headers et cetera. Here there's additional information produced by wireshark which says that the HDP response is created by re-assembling 5 TCAP segment's or packet's. So now I'd like to show you the difference between that and HTP. Yes. Draft or go to the browser and visit an age DTP page. Now but before visiting the page let's start Wiresh
 0:01:57
0:01:57
 0:10:05
0:10:05
 0:08:33
0:08:33
 0:10:38
0:10:38
 0:04:20
0:04:20
 0:20:12
0:20:12
 0:19:07
0:19:07
 0:10:39
0:10:39
 0:01:04
0:01:04
 0:19:25
0:19:25
 0:12:24
0:12:24
 0:06:03
0:06:03
 0:09:27
0:09:27
 0:08:08
0:08:08
 0:11:26
0:11:26
 0:08:15
0:08:15
 0:02:06
0:02:06
 0:19:03
0:19:03
 0:08:41
0:08:41
 0:54:30
0:54:30
 0:13:07
0:13:07
 0:12:01
0:12:01
 0:28:07
0:28:07
 0:11:55
0:11:55