filmov
tv
Encryption vs Cryptographic Hash - Friday Minis 36

Показать описание
How is data stored in high-security applications? What are the different techniques available and under what situations are they used? We explore two such examples in today's episode of Friday Minis!
= Intro Track Adapted From =
Licensed under Creative Commons: By Attribution 3.0
ISRC: USUAN120010
= Intro Track Adapted From =
Licensed under Creative Commons: By Attribution 3.0
ISRC: USUAN120010
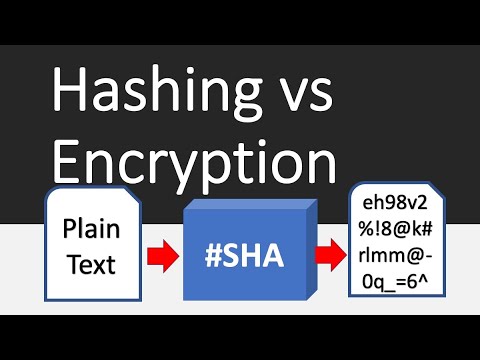
Hashing vs Encryption Differences
7 Cryptography Concepts EVERY Developer Should Know
Encryption vs Cryptographic Hash - Friday Minis 36
Encryption vs Hashing
What is a Cryptographic Hashing Function? (Example + Purpose)
Passwords & hash functions (Simply Explained)
What Is Hashing? | What Is Hashing With Example | Hashing Explained Simply | Simplilearn
Asymmetric Encryption - Simply explained
Difference Between Encryption vs Encoding vs Hashing vs Obfuscation Explained
How secure is 256 bit security?
Hashing and Digital Signatures - CompTIA Security+ SY0-701 - 1.4
Hashing Vs Encryption
Cryptographic Hash Functions - CompTIA Security+ SY0-401: 6.2
Encryption vs Hashing - Difference between encryption and hashing | Encryption Consulting
SHA: Secure Hashing Algorithm - Computerphile
Data Integrity - How Hashing is used to ensure data isn't modified - HMAC - Cryptography
Encryption and Hashing explanation and differences in 5 minutes
What is Hashing on the Blockchain?
What is a Cryptographic Hash? | Hash Functions | Hashing v/s Encryption
CyberSecurity Definitions | Hash vs Encryption
21. Cryptography: Hash Functions
Password Storage Tier List: encryption, hashing, salting, bcrypt, and beyond
What are Cryptographic Hash Functions?
The difference between checksums and cryptographic hashes
Комментарии
 0:19:38
0:19:38
 0:11:55
0:11:55
 0:03:17
0:03:17
 0:02:29
0:02:29
 0:07:08
0:07:08
 0:07:28
0:07:28
 0:09:45
0:09:45
 0:04:40
0:04:40
 0:06:51
0:06:51
 0:05:06
0:05:06
 0:10:24
0:10:24
 0:02:07
0:02:07
 0:07:04
0:07:04
 0:05:53
0:05:53
 0:10:21
0:10:21
 0:07:24
0:07:24
 0:05:34
0:05:34
 0:04:48
0:04:48
 1:35:37
1:35:37
 0:00:41
0:00:41
 1:22:01
1:22:01
 0:10:16
0:10:16
 0:05:43
0:05:43
 0:02:43
0:02:43