filmov
tv
Top 16 Nmap Commands You Must Know! #nmap #cybersecurity #scanner #top16nmapcommands@ScanderLoud

Показать описание
Top 16 Nmap Commands You Must Know!
OUTLINE:
00:00:00
Intro
00:00:15
Basic Nmap Scan against IP or Host
00:00:44 Nmap Ping Scan
00:01:09 Scan Specific Ports or Entire Port Ranges
00:01:43 Scan Multiple IP Addresses
00:02:14 Scan IP Ranges
00:02:40 Scan the Most Popular Ports
00:03:05 Scan Hosts and IP Addresses from a Text File
00:03:27 Save Nmap Scan Results to a File
00:03:53 Disable DNS Name Resolution
00:04:16 OS and Service Detection with Fast Execution
00:04:42 Detect Service/Daemon Versions
00:05:05 Scan Using TCP or UDP Protocols
00:05:38 CVE Detection Using Nmap
00:06:01 Flood Testing with Nmap
00:06:26 Testing Brute Force Attacks
00:06:59 Detecting Malware Infections on Remote Hosts
00:07:26 Conclusion
Top 16 Nmap Commands: A Comprehensive Guide
1. Basic Nmap Scan against IP or Host
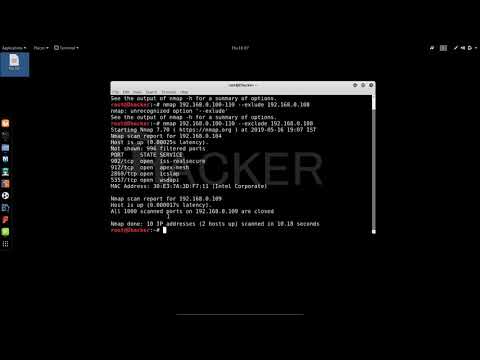
* Explanation: This is the most basic form of Nmap scanning, used to check the status of a single IP or domain. It helps determine if the host is up and accessible, and what services might be running.
2. Nmap Ping Scan
* Command: nmap -sp 192.168.5.0/24
* Explanation: This command is used to identify live hosts on a network by sending ICMP echo requests (pings). It's a quick way to discover which devices are active within a specified IP range.
3. Scan Specific Ports or Entire Port Ranges
* Command: nmap -p 1-65535 localhost
* Explanation: This command scans all 65,535 ports on a host, which is useful for comprehensive security assessments. You can also specify particular ports for faster results, e.g., nmap -p 80,443 8.8.8.8.
4. Scan Multiple IP Addresses
* Command: nmap 1.1.1.1 8.8.8.8 or nmap 1.1.1.1,2,3,4
* Explanation: This command allows scanning of multiple IP addresses or a list of IPs sequentially. It’s useful for assessing multiple targets at once.
5. Scan IP Ranges
* Command: nmap 8.8.8.0/28
* Explanation: This command scans an entire CIDR IP range, useful for network-wide scans. It can also be specified with ranges like nmap 8.8.8.1-14 or wildcard nmap 8.8.8.* for broader scans.
6. Scan the Most Popular Ports
* Command: nmap --top-ports 20 192.168.1.106
* Explanation: This scans the top N most commonly used ports (e.g., 20 in the example), which is efficient for quickly identifying the most critical services on a host.
7. Scan Hosts and IP Addresses from a Text File
8. Save Nmap Scan Results to a File
* Explanation: Saves the scan results in a specified format, like normal text (-oN) or XML (-oX), useful for documentation or further analysis.
9. Disable DNS Name Resolution
* Command: nmap -p 80 -n 8.8.8.8
* Explanation: This speeds up scans by disabling reverse DNS resolution, which can be particularly helpful for large network scans.
11. Detect Service/Daemon Versions - Command: nmap -sV localhost - Explanation: This command identifies the version of services running on open ports, which is crucial for vulnerability assessment and security auditing.
12. Scan Using TCP or UDP Protocols - Command: nmap -sT 192.168.1.1 (TCP) or nmap -sU localhost (UDP) - Explanation: Nmap can scan using both TCP (-sT) and UDP (-sU) protocols, allowing for comprehensive network mapping and service identification.
13. CVE Detection Using Nmap - Command: nmap -Pn --script vuln 192.168.1.105 - Explanation: This uses Nmap’s scripting engine (NSE) to detect vulnerabilities based on known CVEs (Common Vulnerabilities and Exposures), making it a powerful tool for identifying security flaws.
16. Detecting Malware Infections on Remote Hosts - Command: nmap -sV --script=http-malware-host 192.168.1.105 - Explanation: This command scans for malware and backdoors by checking known malware signatures and behaviors on remote hosts.
OUTLINE:
00:00:00
Intro
00:00:15
Basic Nmap Scan against IP or Host
00:00:44 Nmap Ping Scan
00:01:09 Scan Specific Ports or Entire Port Ranges
00:01:43 Scan Multiple IP Addresses
00:02:14 Scan IP Ranges
00:02:40 Scan the Most Popular Ports
00:03:05 Scan Hosts and IP Addresses from a Text File
00:03:27 Save Nmap Scan Results to a File
00:03:53 Disable DNS Name Resolution
00:04:16 OS and Service Detection with Fast Execution
00:04:42 Detect Service/Daemon Versions
00:05:05 Scan Using TCP or UDP Protocols
00:05:38 CVE Detection Using Nmap
00:06:01 Flood Testing with Nmap
00:06:26 Testing Brute Force Attacks
00:06:59 Detecting Malware Infections on Remote Hosts
00:07:26 Conclusion
Top 16 Nmap Commands: A Comprehensive Guide
1. Basic Nmap Scan against IP or Host
* Explanation: This is the most basic form of Nmap scanning, used to check the status of a single IP or domain. It helps determine if the host is up and accessible, and what services might be running.
2. Nmap Ping Scan
* Command: nmap -sp 192.168.5.0/24
* Explanation: This command is used to identify live hosts on a network by sending ICMP echo requests (pings). It's a quick way to discover which devices are active within a specified IP range.
3. Scan Specific Ports or Entire Port Ranges
* Command: nmap -p 1-65535 localhost
* Explanation: This command scans all 65,535 ports on a host, which is useful for comprehensive security assessments. You can also specify particular ports for faster results, e.g., nmap -p 80,443 8.8.8.8.
4. Scan Multiple IP Addresses
* Command: nmap 1.1.1.1 8.8.8.8 or nmap 1.1.1.1,2,3,4
* Explanation: This command allows scanning of multiple IP addresses or a list of IPs sequentially. It’s useful for assessing multiple targets at once.
5. Scan IP Ranges
* Command: nmap 8.8.8.0/28
* Explanation: This command scans an entire CIDR IP range, useful for network-wide scans. It can also be specified with ranges like nmap 8.8.8.1-14 or wildcard nmap 8.8.8.* for broader scans.
6. Scan the Most Popular Ports
* Command: nmap --top-ports 20 192.168.1.106
* Explanation: This scans the top N most commonly used ports (e.g., 20 in the example), which is efficient for quickly identifying the most critical services on a host.
7. Scan Hosts and IP Addresses from a Text File
8. Save Nmap Scan Results to a File
* Explanation: Saves the scan results in a specified format, like normal text (-oN) or XML (-oX), useful for documentation or further analysis.
9. Disable DNS Name Resolution
* Command: nmap -p 80 -n 8.8.8.8
* Explanation: This speeds up scans by disabling reverse DNS resolution, which can be particularly helpful for large network scans.
11. Detect Service/Daemon Versions - Command: nmap -sV localhost - Explanation: This command identifies the version of services running on open ports, which is crucial for vulnerability assessment and security auditing.
12. Scan Using TCP or UDP Protocols - Command: nmap -sT 192.168.1.1 (TCP) or nmap -sU localhost (UDP) - Explanation: Nmap can scan using both TCP (-sT) and UDP (-sU) protocols, allowing for comprehensive network mapping and service identification.
13. CVE Detection Using Nmap - Command: nmap -Pn --script vuln 192.168.1.105 - Explanation: This uses Nmap’s scripting engine (NSE) to detect vulnerabilities based on known CVEs (Common Vulnerabilities and Exposures), making it a powerful tool for identifying security flaws.
16. Detecting Malware Infections on Remote Hosts - Command: nmap -sV --script=http-malware-host 192.168.1.105 - Explanation: This command scans for malware and backdoors by checking known malware signatures and behaviors on remote hosts.
 0:07:37
0:07:37
 0:16:35
0:16:35
 0:17:09
0:17:09
 0:10:50
0:10:50
 0:27:00
0:27:00
 0:02:28
0:02:28
 0:20:27
0:20:27
 0:00:32
0:00:32
 0:00:29
0:00:29
 0:01:04
0:01:04
 0:00:42
0:00:42
![[root] LiveBoot Samsung](https://i.ytimg.com/vi/14UcNcW4r0Q/hqdefault.jpg) 0:00:59
0:00:59
 0:02:06
0:02:06
 0:31:58
0:31:58
 0:11:11
0:11:11
 0:27:25
0:27:25
 0:13:29
0:13:29
 0:02:43
0:02:43
 0:12:02
0:12:02
 0:24:26
0:24:26
 0:00:34
0:00:34
 0:08:24
0:08:24
 0:01:40
0:01:40
 0:00:16
0:00:16