filmov
tv
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoC

Показать описание
Samsung S7 is connected to Pixel as HID device (keyboard) that tries to brute force lock screen PIN (PoC) and then download, install and launch Metasploit payload
How to prevent such scenario
1) Charge you smartphone using you own adapter when possible
2) Don't use trivial PIN or password lock screen protection
3) Use mobile security software that will detect Metasploit payload
How to prevent such scenario
1) Charge you smartphone using you own adapter when possible
2) Don't use trivial PIN or password lock screen protection
3) Use mobile security software that will detect Metasploit payload
Hacking into Android in 32 seconds | HID attack | Metasploit | PIN brute force PoC
Hacking into Android in 32 seconds // HID attack // Metasploit // PIN brute force.
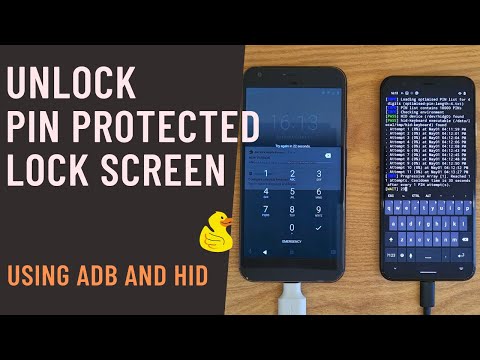
How to unlock PIN protected Android device using ADB and HID method | Brute force | Rubber Ducky
Hacking Android In LAN | How Hackers Hack Phones? 💀
Kali Linux NetHunter Android install in 5 minutes (rootless)
Hacking into Android phone using another phone?
TURN YOUR ANDROID PHONE TO A PORTABLE HACKING MACHINE!
Hacking/bypassing android lockscreen
Termux Course in 1 Hour in Hindi for free
Top 5 Ethical Hacking apps for Android |learn Ethical Hacking and Practice 2023 | #hacking
How To Hack A Phone Remotely?
Hacking Mobile Phones | Android & iOS | 2022
android hacking #linux #trojan #hackers #exploit #msfconsole#security #python #pythontools
Access Android with Metasploit Kali (Cybersecurity)
Small Demo of a Big Tool🔥 HACKADROID #shorts #ytshorts #github #hacking
Introduction to Android Hacking
Android Bluetooth Hacking
Advanced Android Hacking: Create a backdoor in an original application with Termux.
Turn your Phone into Hacking Machine || Android Hacking App || Mobile Hacking Tool || Android App
Turn your Android phone into a HACKING Machine without Root !
Turn you phone into a hacking device 😈💀
Hacking cell phones like Mr Robot
Android hacking 😈 tool 2021#hacking #hacker #androidhacking #shorts #tool #viral #termux #termuxtool...
Hack into Android using APK - Andro Rat | Lan Practical | Ethical Hacking
Комментарии
 0:00:34
0:00:34
 0:00:48
0:00:48
 0:10:59
0:10:59
 0:06:53
0:06:53
 0:05:44
0:05:44
 0:05:48
0:05:48
 0:14:44
0:14:44
 0:00:43
0:00:43
 0:54:02
0:54:02
 0:01:25
0:01:25
 0:07:06
0:07:06
 1:14:10
1:14:10
 0:00:51
0:00:51
 0:13:05
0:13:05
 0:00:31
0:00:31
 0:34:13
0:34:13
 0:35:14
0:35:14
 0:07:42
0:07:42
 0:00:13
0:00:13
 0:07:46
0:07:46
 0:00:16
0:00:16
 0:31:31
0:31:31
 0:00:31
0:00:31
 0:12:11
0:12:11