filmov
tv
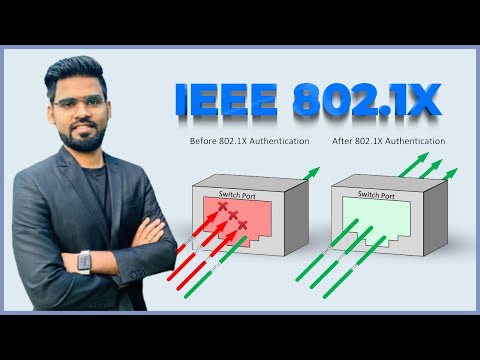
Network security with 802.1X: The Ultimate Configuration Guide

Показать описание
🟢 Please leave 👍🏼 to the video
🟢 Subscribe to the channel
Per consulenze aziendali in ambito networking, sistemi o cloud, è possibile inviare una richiesta via email.
For business consulting in networking, systems, or cloud services, please send an email request.
Netflix 4.93 euro al mese
Spotify 3.17 euro al mese
Disney+ 4.33 euro al mese
office 365 3.67 euro al mese
paramount+ 4 euro al mese
Canva 5.99 euro al mese
Duolingo 3.75 euro al mese
NordVPN 1.97 euro al mese
ChatGPT 4.0 plus 5.87 euro al mese
CODE PROMO YDZQ4
🔥 Social🔥
00:00 Intro
01:47 What do you need for 802.1x
02:23 Active directory
04:24 NPS server
07:06 Certificate Authority
11:14 Switch configuration
11:43 Windows Client
#VLANs #8021x #DynamicVLANs #networkconfiguration #networksecurity #ITGuide #VLANSetup #networkmanagement #cybersecurity #ITTraining
🟢 Subscribe to the channel
Per consulenze aziendali in ambito networking, sistemi o cloud, è possibile inviare una richiesta via email.
For business consulting in networking, systems, or cloud services, please send an email request.
Netflix 4.93 euro al mese
Spotify 3.17 euro al mese
Disney+ 4.33 euro al mese
office 365 3.67 euro al mese
paramount+ 4 euro al mese
Canva 5.99 euro al mese
Duolingo 3.75 euro al mese
NordVPN 1.97 euro al mese
ChatGPT 4.0 plus 5.87 euro al mese
CODE PROMO YDZQ4
🔥 Social🔥
00:00 Intro
01:47 What do you need for 802.1x
02:23 Active directory
04:24 NPS server
07:06 Certificate Authority
11:14 Switch configuration
11:43 Windows Client
#VLANs #8021x #DynamicVLANs #networkconfiguration #networksecurity #ITGuide #VLANSetup #networkmanagement #cybersecurity #ITTraining
Port Security - CompTIA Security+ SY0-701 - 3.2
MicroNugget: How to Use 802.1X and NAC
802.1X | Network Basics
Network security with 802.1X: The Ultimate Configuration Guide
what is 802 1x protocol? | 802.1x port based authentication | CCNA 200-301
IEEE 802.1X | Understanding 802.1X Authentication | What is IEEE 802.1X and How does 802.1X work?
Network Security with 802.1X | Intro to Network Design
CCNA LANs 11-15: 802.1X
802.1X Identity Based Networking
Port Security and 802.1X - CompTIA Security+ SY0-401: 1.2
802 1x Port Based Authentication Configuration! | 1 Minute Quick Configs | IPCisco.com
802 1x Port Based Authentication Configuration! | CCNP 350-401 | IPCisco.com
macmon 802.1X (English)
How To Disable IEEE 802.1X Authentication In Ricoh Printer | Ip Configuration
Network Security: What is 802.1X Authentications
Physical Network Access Control with 802.1X
Role of RADIUS in 802 1X Communications
What Is 802.1X Authentication? - SecurityFirstCorp.com
802.1X Authentication - Endpoint Security - Network Security - CCNA - KevTechify | vid 51
Port Security vs Port Based Authentication (802.1x) Whats the Difference?
802.1X Authentication and 4-Way Handshake for WiFi Step by Step
3. Introduction to WPA Enterprise 802 1x wireless
So sicherst du deine LAN Ports ab! - UniFi LAN Port Authentifizierung mit 802.1X
ExtremeCloud IQ – 802.1X Authentication – Extreme Dojo
Комментарии
 0:03:50
0:03:50
 0:03:47
0:03:47
 0:04:04
0:04:04
 0:17:00
0:17:00
 0:04:06
0:04:06
 0:07:12
0:07:12
 0:09:19
0:09:19
 0:04:20
0:04:20
 0:01:01
0:01:01
 0:05:33
0:05:33
 0:01:00
0:01:00
 0:01:00
0:01:00
 0:04:10
0:04:10
 0:01:52
0:01:52
 0:01:18
0:01:18
 0:35:14
0:35:14
 0:09:06
0:09:06
 0:02:20
0:02:20
 0:09:01
0:09:01
 0:13:12
0:13:12
 0:12:53
0:12:53
 0:10:11
0:10:11
 0:16:03
0:16:03
 0:17:31
0:17:31