filmov
tv
Visualizing the OAuth Flow and Why PKCE is Needed

Показать описание
Visualizing the OAuth Flow and Why PKCE is Needed
OAuth 2 Explained In Simple Terms
OAuth Authorization code flow
OAuth device flow
oAuth for Beginners - How oauth authentication🔒 works ?
Implement the OAuth 2.0 client credentials grant type flow in Apigee
OAuth 2.0: An Overview
OAuth 2.0 Flow: How to Securely Get your Grapes
What's going on with the OAuth 2.0 Implicit flow?
Authorization Code Grant Flow Overview
Authorization Code Flow - The Insecurity of OAuth 2.0 in Frontends #programming #coding
OAuth implicit flow
Why is JWT popular?
What's the difference between Confidential and Public clients? - OAuth in Five Minutes
A Story of 3 Legged OAuth
What are the OAuth 2.0 Grant Type Flows? First up, Authorization Code
OAuth 2.0 - Implicit grant and how it works
OAuth 2.0 Implicit Grant Flow
OAuth 2 0 and OpenID Connect for Single Page Applications Philippe De Ryck
How Authentication and Authorization Work for SPAs
OAuth 2.0 Authorization Code Flow | Practical Example | oAuth 2.0 Authorization Flow
OAuth PKCE | OAuth Proof Key for Code Exchange explained
OAuth2 Authorisation Code + PKCE Grant Type Walkthrough
Introduction to OAuth 2.0 and OpenID Connect By Philippe De Ryck
Комментарии
 0:01:42
0:01:42
 0:04:32
0:04:32
 0:11:49
0:11:49
 0:02:59
0:02:59
 0:10:43
0:10:43
 0:05:01
0:05:01
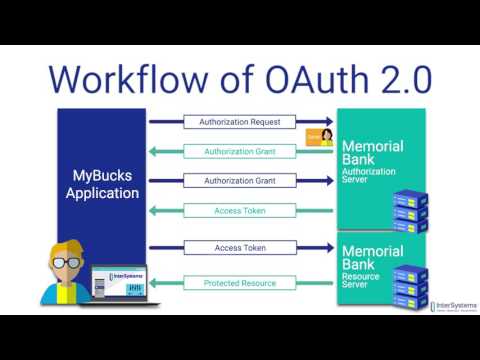 0:06:34
0:06:34
 0:01:11
0:01:11
 0:17:18
0:17:18
 0:04:25
0:04:25
 0:00:55
0:00:55
 0:06:41
0:06:41
 0:05:14
0:05:14
 0:05:03
0:05:03
 0:02:20
0:02:20
 0:03:36
0:03:36
 0:07:32
0:07:32
 0:00:36
0:00:36
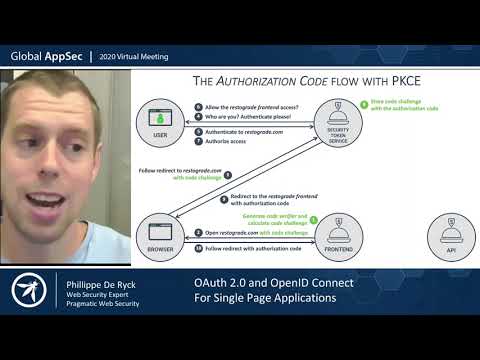 0:36:53
0:36:53
 0:09:33
0:09:33
 0:10:52
0:10:52
 0:09:39
0:09:39
 0:05:21
0:05:21
 2:43:46
2:43:46