filmov
tv
Group Managed Service Accounts : GMSAs

Показать описание
GMSA Advantages:
1. No Password Management
2. Supports to share across multiple hosts
3. Can use to run scheduled tasks (Managed service accounts do not support some scheduled tasks)
4. It is uses Microsoft Key Distribution Service (KDC) to create and manage the passwords for the gMSA.
5. Stores keys in AD, no password stored in registry like normal svc accounts, so more secure.
#Setting Up GMSAs:
#1. Create New Sub-OU for GMSA and GMSA GSG
New-ADOrganizationalUnit -Name "GMSAs" -Path "OU=Service_DROIDS,DC=BattleStars,DC=fleet";
#2. Create GSG to palce users or services in that will be allowed to access the GMSA
$GMSA_Group = "GMSA_CYLON_USERS";
New-ADGroup -Name $GMSA_Group -SamAccountName $GMSA_Group `
-GroupCategory Security -GroupScope Global -DisplayName $GMSA_Group `
-Path "OU=GMSAs,OU=Service_DROIDS,DC=BattleStars,DC=fleet" `
-Description "GSG with Access to GMSA GMSA_CYLON_USERS";
#3. Add computer accounts to GSG that will make use of GMSA:
Add-ADGroupMember "CN=GMSA_CYLON_USERS,OU=GMSAs,OU=Service_DROIDS,DC=BattleStars,DC=fleet" `
-Members "Mail2019CORE-01$","Galactica$","Twilight1$";
#4. Create KDS root key. From DC with Enterprise;/Domain admin privs.
# With -EffectiveImmediately parameter? Can take up to 10 hours for key to become fully functional.
# So this step should be done the day BEFORE creating a GMSA
#Normal (best practice) can take 10 hours to replicate
#Add-KdsRootKey –EffectiveImmediately;
#FORCE replicaiton immediately (NOT best practice)
Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10));
#5. Test KDS Root Key. First, get the KDS root key "KeyID". Then use it with Test cmdlett:
Get-KdsRootKey;
#Return value = "0a7a08a3-d0c7-e221-f486-7a80ab23bb22"
Test-KdsRootKey -KeyId "0a7a08a3-d0c7-e221-f486-7a80ab23bb22";
#6. Create GMSA account (SAM/NAME Must be no more than 15 chars)
$GMSA_Name = "GMSA_AD_CYLONS";
$GMSA_Group = "GMSA_CYLON_USERS";
$GMSA_Servers = Get-ADGroupMember -Identity $GMSA_Group | Select-Object -ExpandProperty Name;
$GMSA_Server_IDs = $GMSA_Servers | ForEach-Object { Get-ADComputer -Identity $_ };
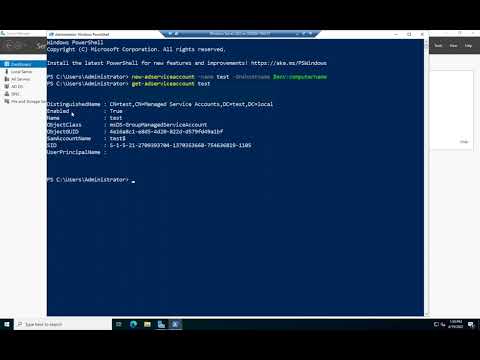
New-ADServiceAccount -Name $GMSA_Name -Enabled $true -Description “AD Managed Service Account for CYLON Servers” `
-Displayname $GMSA_Name –PrincipalsAllowedToRetrieveManagedPassword $GMSA_Server_IDs `
-DNSHostName $GMSA_FQDN;
#7. Verify GMSA Account
Get-ADServiceAccount "GMSA_AD_CYLONS";
#8. Install GMSA on computer (Log onto SERVER to be managed and run from there)
# MSAs (not GMSAs) can only be active and linked to a single computer at one time.
# If you attempt to install the same MSA account on another server? It asks for confirmation.
# It will then disable the MSA for the previous server.
# So if you want to use MSAs for multiple servers? You must create an MSA for each one.
# Otherwise, use a GMSA so you can use it with multiple servers by adding them to the GSG associated with it.
#Add-WindowsFeature RSAT-AD-PowerShell;
#Import-Module ActiveDirectory;
Install-ADServiceAccount -Identity "GMSA_AD_CYLONS";
#9. Test It (Log onto mail1 and run from there)
Test-ADServiceAccount "GMSA_AD_CYLONS";
#10. Removing a GMSA
Remove-ADServiceAccount –identity “GMSA_AD_CYLONS” -Confirm:$false;
1. No Password Management
2. Supports to share across multiple hosts
3. Can use to run scheduled tasks (Managed service accounts do not support some scheduled tasks)
4. It is uses Microsoft Key Distribution Service (KDC) to create and manage the passwords for the gMSA.
5. Stores keys in AD, no password stored in registry like normal svc accounts, so more secure.
#Setting Up GMSAs:
#1. Create New Sub-OU for GMSA and GMSA GSG
New-ADOrganizationalUnit -Name "GMSAs" -Path "OU=Service_DROIDS,DC=BattleStars,DC=fleet";
#2. Create GSG to palce users or services in that will be allowed to access the GMSA
$GMSA_Group = "GMSA_CYLON_USERS";
New-ADGroup -Name $GMSA_Group -SamAccountName $GMSA_Group `
-GroupCategory Security -GroupScope Global -DisplayName $GMSA_Group `
-Path "OU=GMSAs,OU=Service_DROIDS,DC=BattleStars,DC=fleet" `
-Description "GSG with Access to GMSA GMSA_CYLON_USERS";
#3. Add computer accounts to GSG that will make use of GMSA:
Add-ADGroupMember "CN=GMSA_CYLON_USERS,OU=GMSAs,OU=Service_DROIDS,DC=BattleStars,DC=fleet" `
-Members "Mail2019CORE-01$","Galactica$","Twilight1$";
#4. Create KDS root key. From DC with Enterprise;/Domain admin privs.
# With -EffectiveImmediately parameter? Can take up to 10 hours for key to become fully functional.
# So this step should be done the day BEFORE creating a GMSA
#Normal (best practice) can take 10 hours to replicate
#Add-KdsRootKey –EffectiveImmediately;
#FORCE replicaiton immediately (NOT best practice)
Add-KdsRootKey –EffectiveTime ((get-date).addhours(-10));
#5. Test KDS Root Key. First, get the KDS root key "KeyID". Then use it with Test cmdlett:
Get-KdsRootKey;
#Return value = "0a7a08a3-d0c7-e221-f486-7a80ab23bb22"
Test-KdsRootKey -KeyId "0a7a08a3-d0c7-e221-f486-7a80ab23bb22";
#6. Create GMSA account (SAM/NAME Must be no more than 15 chars)
$GMSA_Name = "GMSA_AD_CYLONS";
$GMSA_Group = "GMSA_CYLON_USERS";
$GMSA_Servers = Get-ADGroupMember -Identity $GMSA_Group | Select-Object -ExpandProperty Name;
$GMSA_Server_IDs = $GMSA_Servers | ForEach-Object { Get-ADComputer -Identity $_ };
New-ADServiceAccount -Name $GMSA_Name -Enabled $true -Description “AD Managed Service Account for CYLON Servers” `
-Displayname $GMSA_Name –PrincipalsAllowedToRetrieveManagedPassword $GMSA_Server_IDs `
-DNSHostName $GMSA_FQDN;
#7. Verify GMSA Account
Get-ADServiceAccount "GMSA_AD_CYLONS";
#8. Install GMSA on computer (Log onto SERVER to be managed and run from there)
# MSAs (not GMSAs) can only be active and linked to a single computer at one time.
# If you attempt to install the same MSA account on another server? It asks for confirmation.
# It will then disable the MSA for the previous server.
# So if you want to use MSAs for multiple servers? You must create an MSA for each one.
# Otherwise, use a GMSA so you can use it with multiple servers by adding them to the GSG associated with it.
#Add-WindowsFeature RSAT-AD-PowerShell;
#Import-Module ActiveDirectory;
Install-ADServiceAccount -Identity "GMSA_AD_CYLONS";
#9. Test It (Log onto mail1 and run from there)
Test-ADServiceAccount "GMSA_AD_CYLONS";
#10. Removing a GMSA
Remove-ADServiceAccount –identity “GMSA_AD_CYLONS” -Confirm:$false;
Комментарии
 0:09:24
0:09:24
 0:14:54
0:14:54
 0:08:07
0:08:07
 0:07:30
0:07:30
 0:31:53
0:31:53
 0:08:50
0:08:50
 0:12:12
0:12:12
 0:12:10
0:12:10
 1:00:28
1:00:28
 0:12:15
0:12:15
 0:14:29
0:14:29
 0:07:38
0:07:38
 0:16:34
0:16:34
 0:03:14
0:03:14
 0:04:54
0:04:54
 0:09:27
0:09:27
 0:05:28
0:05:28
 0:16:01
0:16:01
 0:05:37
0:05:37
 0:29:30
0:29:30
 0:02:27
0:02:27
 0:15:15
0:15:15
 0:15:11
0:15:11
 0:08:26
0:08:26