filmov
tv
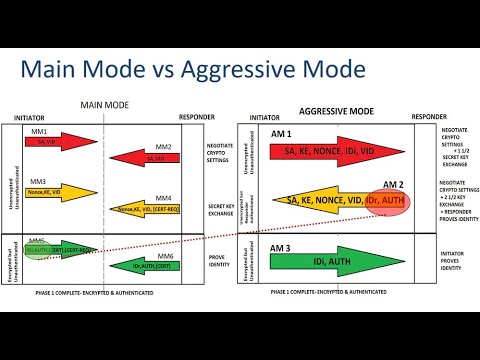
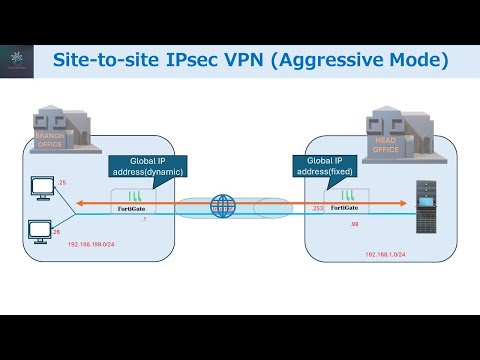
Main mode vs Aggresive Mode- IPSEC Training | #networkershome

Показать описание
In this video, we'll be digging deeper into IPSEC. We'll be taking a look at the message exchange details of this security protocol, so that you can understand how it works.
If you're interested in learning more about IPSEC, then this video is for you! By the end of this video, you'll have a better understanding of how IPSEC works and what its benefits are. So be sure to watch it to the end!
About Networkers Home:
At Networkers Home, we are dedicated to shaping the future of networking and cybersecurity professionals. Our mission is to provide top-tier education and training to help you excel in the fast-paced world of IT and networking. Learn from industry-leading experts and gain hands-on experience with our state-of-the-art labs located in Bangalore.
📱 Connect with Us:
Phone: 📞 9611027980
📚 Placement Programs:
CCNA + CCNP Combo
CCIE Security
AI CyberX Masters
AI Cloud Masters
📘 Cisco Courses:
CCNA Course 200-301
CCNP Enterprise
CCIE Enterprise
Cisco SDWAN
Cisco DNAC
Python Programming for Cisco Network Engineers
🔥 Firewall Courses:
F5 LTM v13
PALO ALTO Firewall
FortiGate Firewall
Cisco Firepower Next-Generation Firewall
☁️ Cloud and Security:
AWS Associate
AWS Professional
AWS Security
AWS Advance
AZ-104: Microsoft Azure Administrator
AZ-500: Microsoft Azure Security
Certified Ethical Hacker
=================================
⚠️ DISCLAIMER: We do not accept any liability for any loss or damage incurred from you acting or not acting as a result of watching any of our publications. You acknowledge that you use the information we provide at your own risk. Do your research.
Copyright Notice: This video and our YouTube channel contain dialogue, music, and images that are the property of NETWORKERS HOME. You are authorized to share the video link and channel and embed this video in your website or others as long as a link back to our YouTube channel is provided.
© NETWORKERS HOME
Комментарии
 1:26:55
1:26:55
 0:01:19
0:01:19
 0:40:59
0:40:59
 0:00:13
0:00:13
 0:00:35
0:00:35
 0:00:14
0:00:14
 0:00:49
0:00:49
 0:00:11
0:00:11
 0:00:18
0:00:18
 0:00:12
0:00:12
 0:37:14
0:37:14
 0:00:15
0:00:15
 0:21:17
0:21:17
 0:00:25
0:00:25
 0:00:19
0:00:19
 0:00:52
0:00:52
 0:00:09
0:00:09
 0:00:13
0:00:13
 0:00:14
0:00:14
 0:00:41
0:00:41
 0:01:00
0:01:00
 0:00:38
0:00:38
 0:00:09
0:00:09
 0:00:58
0:00:58